Hack The Box Sherlocks: CrownJewel2

If you have not yet set up an environment for viewing logs, I suggest you check out my writeup on that process.
I needed to use most of the hints on this one because I have not worked in a Windows domain environment for a while, but it was fun to dive back in.
First download, extract, and upload the necessary files for this challenge.
Task 1
Windows Event ID 7036 is service start and stops. So a quick query for that revealed many events – about 100 various services, but narrowing this down by searching those services for "Shadow" pointed me in the right direction.
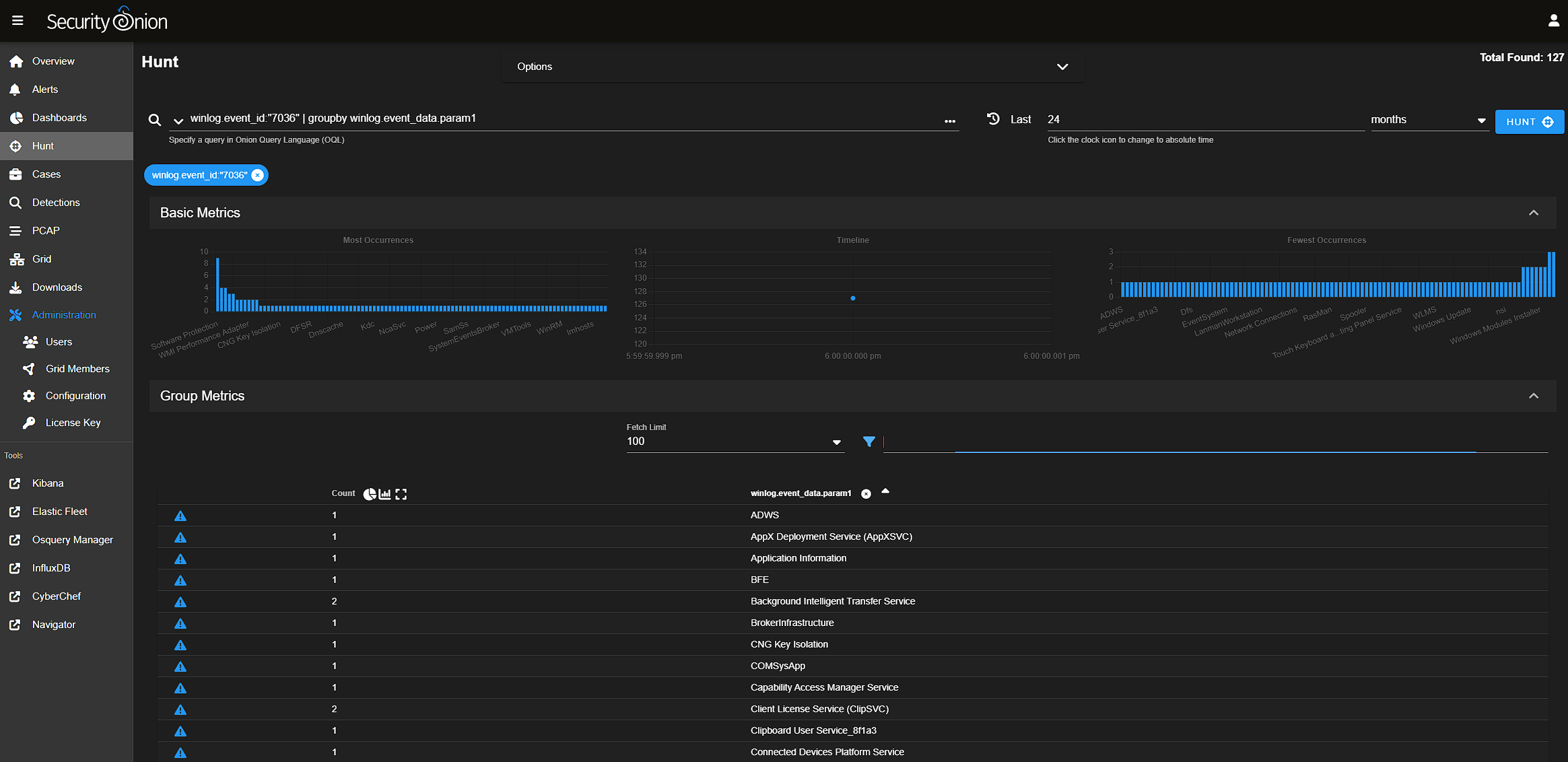
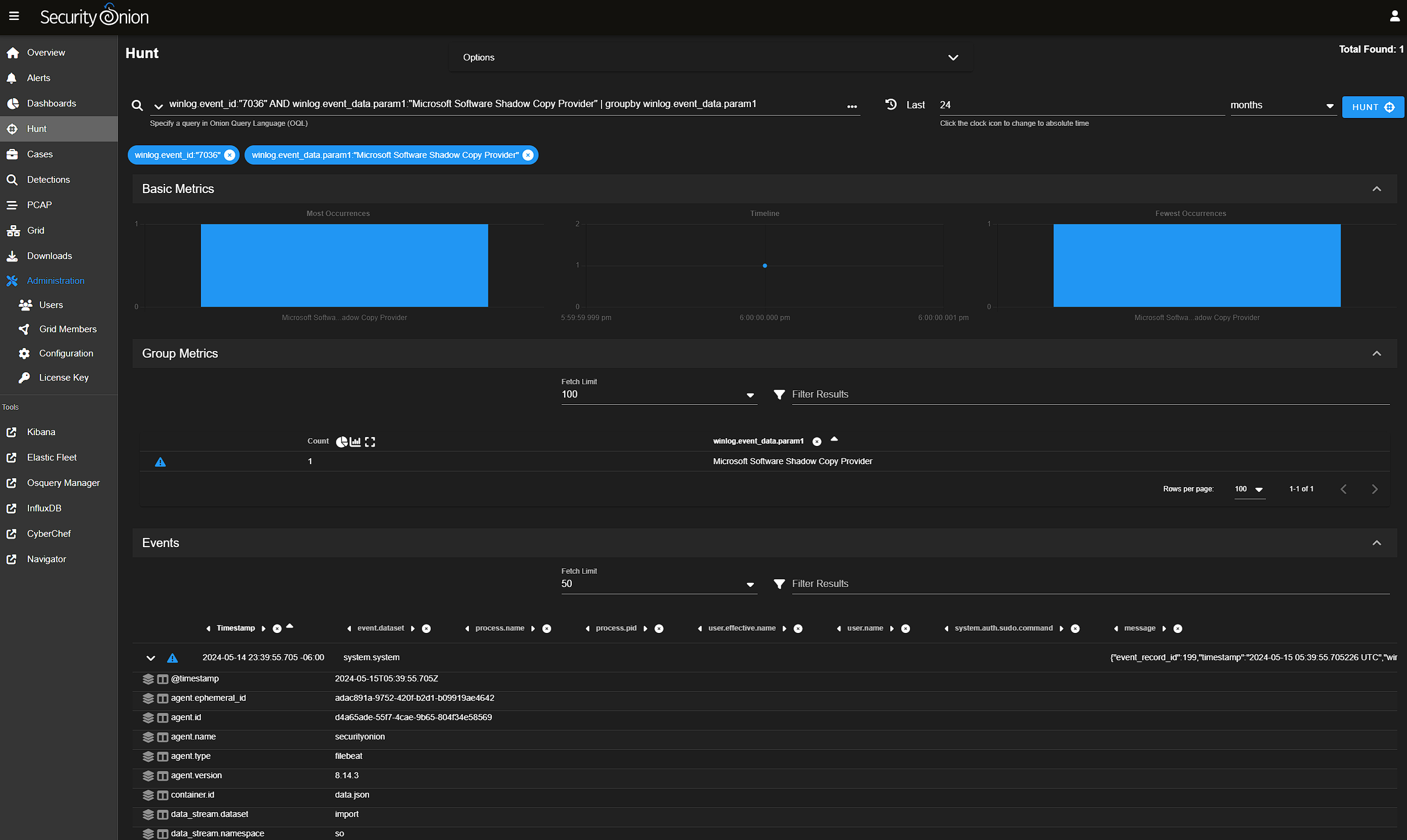
In the image above we can see one event of interest to us and the timestamp 2024-05-15T05:39:55.705Zthat is the answer to this challenge. Keep in mind the format and that you need to Zulu/UTC time. If you copy the time from the GUI row extracted value, you will get local time.
Task 2
Using the plumbing of a Velociraptor query I was able to craft my own query in Security Onion to find the events of interest.
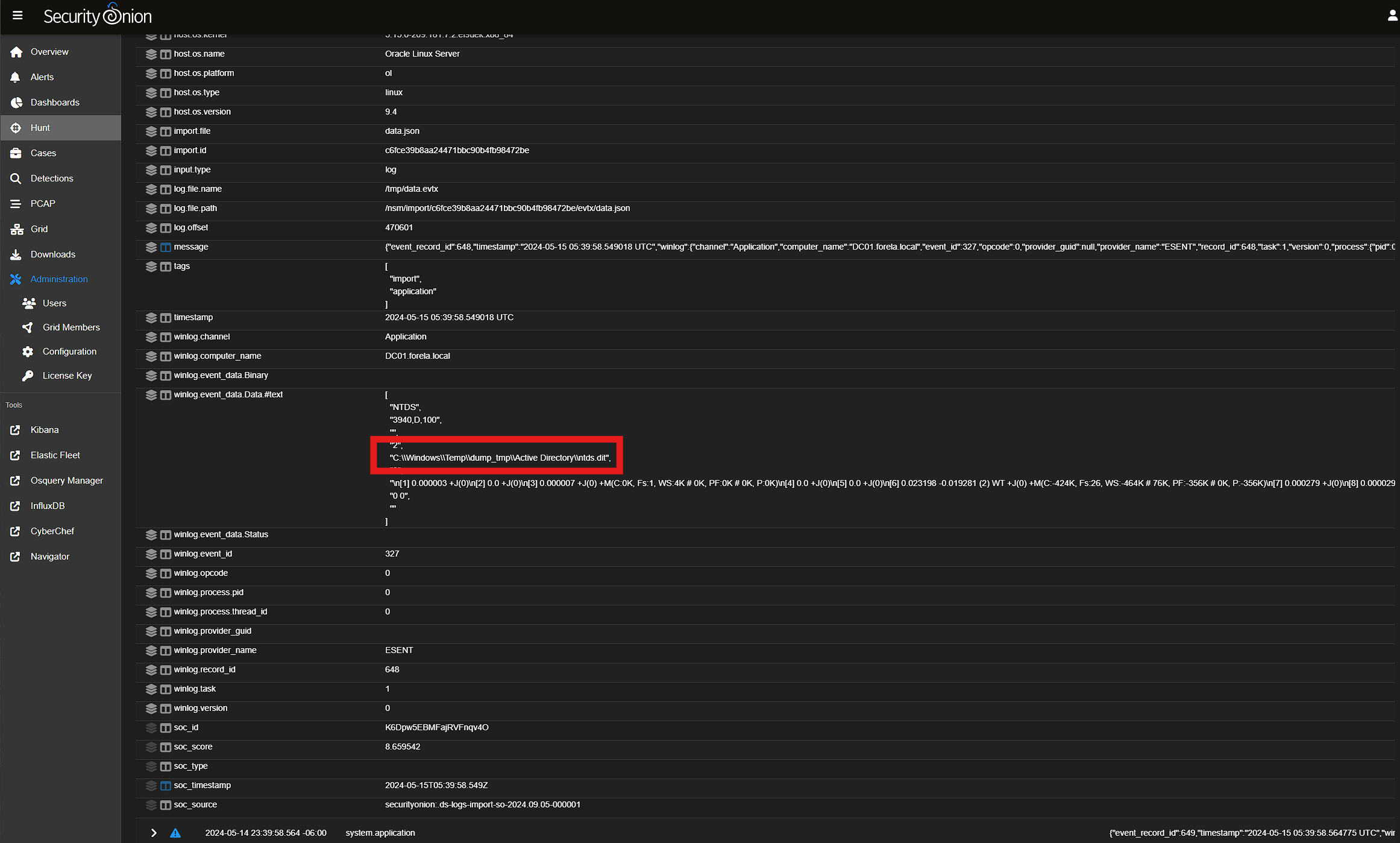
winlog.event_id:(216 OR 327 OR 326 OR 325) AND winlog.channel:Application AND "ntds.dit"
This resulted in a handful of events of which, only one seemed like it could reasonably be the event in question with a path of C:\\Windows\\Temp\\dump_tmp\\Active Directory\\ntds.dit
Task 3
Simply get the Timestamp from the event above
2024-05-15 05:39:56
Task 4
https://www.cisa.gov/news-events/cybersecurity-advisories/aa24-038a
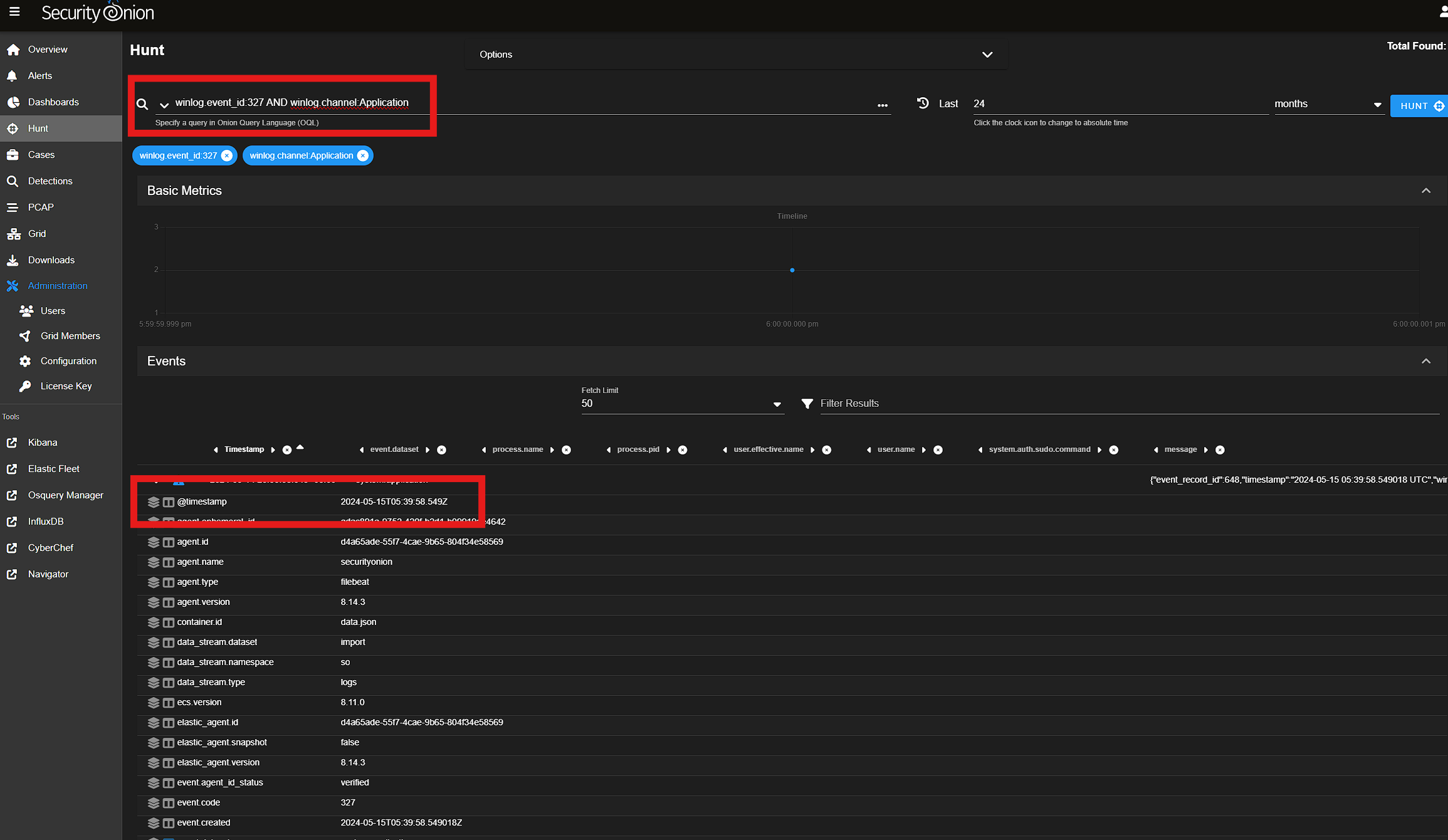
The middle of the article above defines some of the related events for an NTDS dump. Event 327 indicates the copy is complete. Only 2 events with this ID are returned both with the same timestamp.
Task 5
This is just more review of the logs we have been looking at. Specifically the Provider value, which is ESENT for the last few Tasks.
Task 6
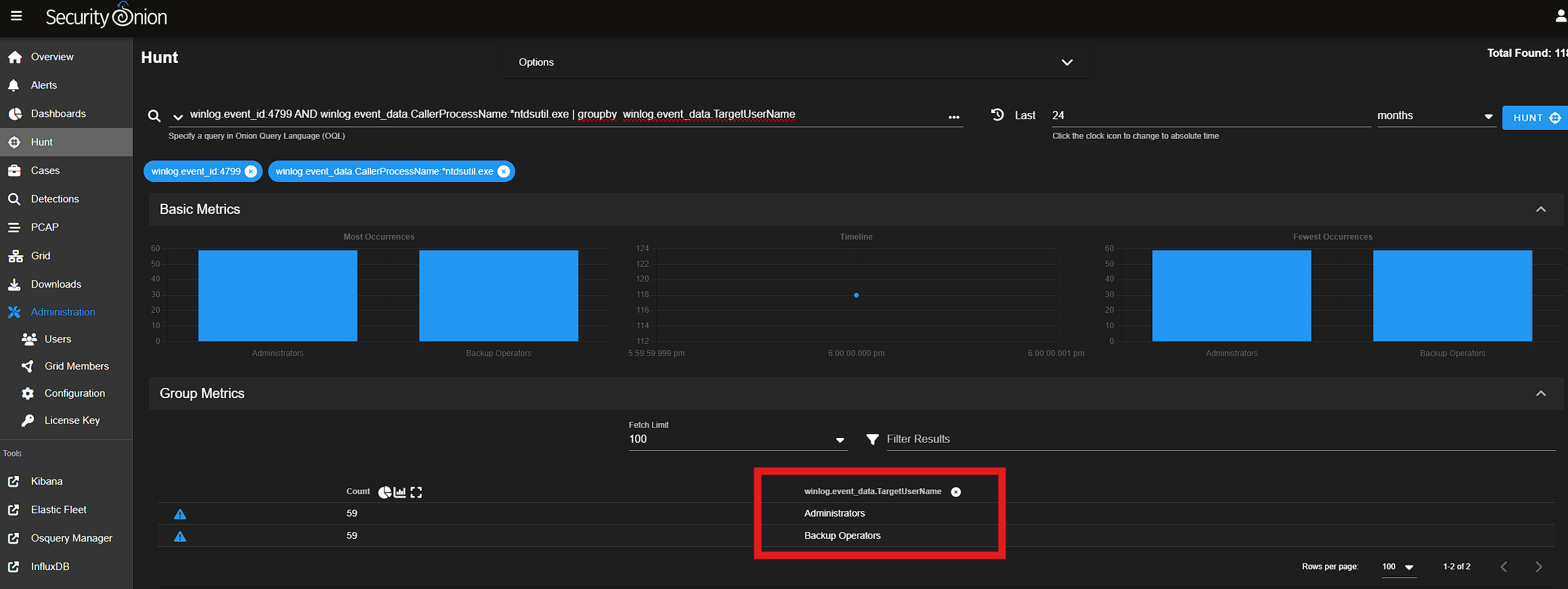
Based on the hint, Event 4799 is what we are looking for. This query groups the events by the Target ID, so we know which groups are enumerated. The individual log events include the Logon ID.
winlog.event_id:4799 AND winlog.event_data.CallerProcessName:*ntdsutil.exe | groupby winlog.event_data.TargetUserName
Task 7
Using the hint, it was easy enough to filter on the indicated log event IDs.
winlog.event_id:("4768" OR "4769" OR "5379")
