SANS 2024 Holiday Hack Challenge - Act 1

See my previous post for the Prologue.
After departing the Geese Islands, we make our way back to the North Pole for some new challenges so help find Santa.
cURLing
The first part of this challenge is just some simple curl-foo that isn't too difficult. The man page for curl or some Googling would help for those unfamiliar.
curl curlingfun:8080curl -khttps://curlingfun:9090curl -khttps://curlingfun:9090-d 'skip=alabaster'curl -khttps://curlingfun:9090-H 'Cookie: end=3'curl -khttps://curlingfun:9090-H 'Stone: Granite'curl -khttps://curlingfun:9090/../../etc/hacks--path-as-is
Those challenges were fairly easy but only get you Silver. There must be something else for Gold. Ahhh, there it is, some additional instructions sitting in the current directory.
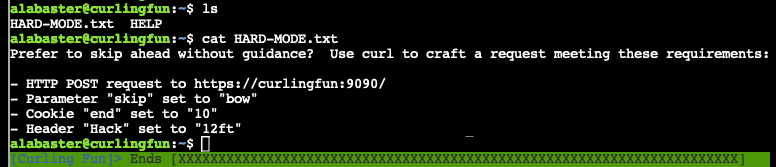
This "hard mode" challenge is very similar to the first challenge but you just have to put a few things together at once. Again, a fairly straightforward path to victory.
curl -k -d 'skip=bow' -H 'Cookie: end=10' -H 'Hack: 12ft'https://curlingfun:9090curl -k --path-as-ishttps://curlingfun:9090/../../etc/buttoncurl -k -Lhttps://curlingfun:9090/GoodSportsmanship
Frosty Keypad

This is the first challenge that seems directly related to finding Santa. On the keypad terminal is this mysterious sticky note that almost certainly looks like some kind of cipher.
Also nearby is The Frosty Book, which corresponds with one of the hints. I am thinking the codes on the sticky above relate to that. 14 pages in the book match with the highest first number, perhaps then the word and letter that correspond to a code. If I had not made this guess, some of the hints point towards an Ottendorf cipher.
We get SANTA if we do this method (after having to re-count for a hyphenated word). This seems fairly promising! Converting that to numbers equals 72682.
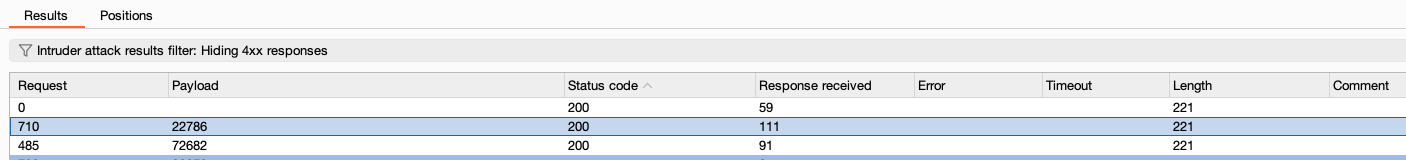
This is successful with a silver accomplishment. So now I need to figure out Gold.
I decided to try to brute force a code other than the one from the cipher using the available numbers, which I found after discovering the UV flashlight. This resulted in an additional valid code! Though this method was slow, I was able to go eat dinner while this attack ran.
Hardware Hacking Part 1
Speaking to Morcel Nougat after completing the keypad challenge, we get more information. From this conversation, we get 1000 pieces of paper – which is actually a zip file that contains 1000 JPG files that are thin slices of something. From the associated hint, we also get a Python script that might help us with heuristic edge detection.
For the script to work, we need to install numpy and pillow and then find the resultant assembled-image.png file. The first try results in a clear image but it seems flipped and off center making it hard to read. Using just some screen captures, I can get a good mirror image to see what we are working with. I had to reference the Wikipedia article on Serial Ports to make out a few of these items: https://en.wikipedia.org/wiki/Serial_port. I was too lazy to load this into image editing software to flip it, sorry.

- Baud: 115200
- Parity: Even
- Data: 7 Bits
- Stop Bits: 1 bit
- Flow Control: RTS
This looks a lot like serial connection parameters and will be useful for the next part of this challenge. Once we get to the actual challenge, the first thing we see is the elf trying to use the SLH to connect to some device with the hopes of finding Santa
The Santa's Little Helper (SLH) card has a voltage toggle for 3/5V and pins:
- VCC
- TX
- RX
- GND
This corresponds to the GRTV pins on the target device. On the console screen, we can set the settings as discovered previously. So, setting up the cables (TX-RX and vice-versa, I made the mistake of RX-RX initially) we can give this a try. The first try with 5V burnt out the chip, 3V was the right number. New pro tip, always start with voltage too low rather than too high. As an aside, I remember burning up chips in my robotics class in college trying to make my robot go fasters.
With the SLH connected, we now go speak with Jewel Loggins for the next step.
For Gold, if you look at the API calls that support Part 1, they go to an /api/v2/complete endpoint. I tried to send to the v1 version of the endpoint just to see what would happen, and it immediately gives you the gold completion.

Hardware Hacking Part 2
Now that we are connected to the device via the SLH, we can perform some interaction. Upon booting the device, we see a boot screen and then the options to startup the system normally or enter a U-boot console.
The U-Boot console does not contain much functionality or information, so we will only explore that later if necessary.
Startup system
Let's start with the default option.
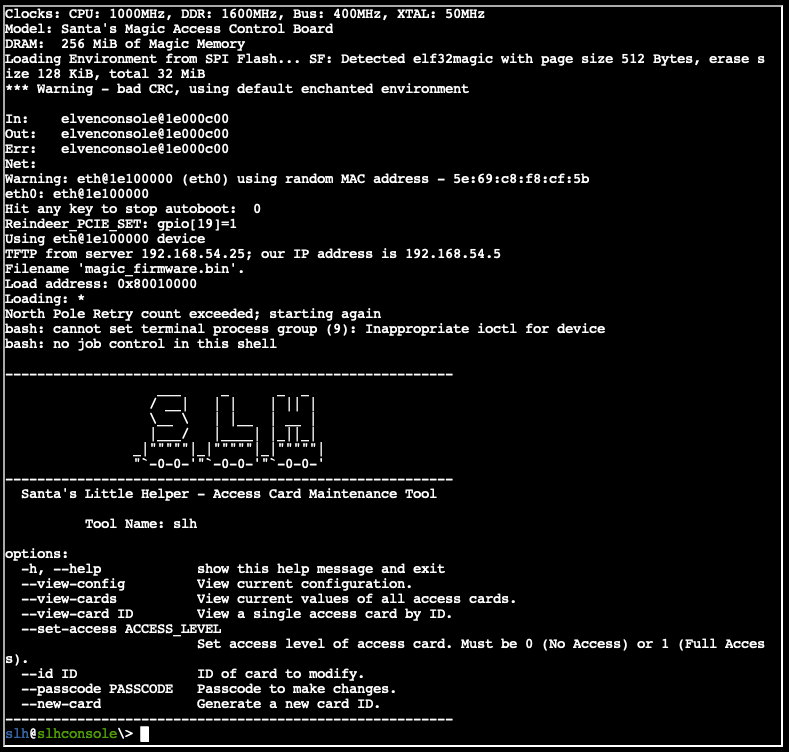
In this directory, we have an SQLite database called access_cards as identified by the file utility. And we have the slh utility itself. The utility seems to parse this database to perform functions.
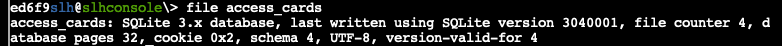
From the BASH history, we can see some interesting information including the passcode needed to make changes: CandyCaneCrunch77
According to Jewel Loggins, we need to modify card 42 and doing so earns us the silver reward.
For gold we have to talk to the elf again, the elf wants us to update card 42 (this was not immediately clear) by directly modifying the database and mentions an HMAC. First, looking at the card objects with the slh tool, it looks like the final attribute could be a hash. Putting a value into a hash identifier indicates this is a valid SHA256 hash.
Perhaps I can use the passcode as the key. Nope...but we can use sqlite3 to read the database file! This provides all the information we need to continue.
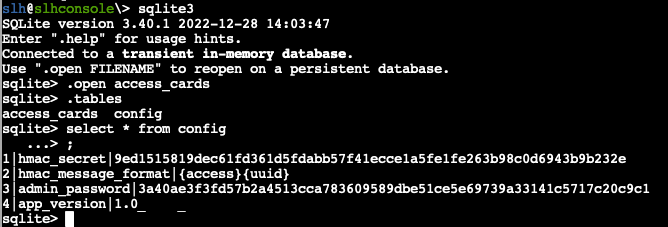
Now, with the details on how to construct the HMAC (key and message format), we should be able to insert our own information into the database using the CyberChef recipe linked in the hints(as one method). After trying for a while with this exact key, I finally determined that this is likely a hash of the key and put it into Google. Sure enough, this hash equates to pizza.
That turned out to be a dead end. But I still could not generate an HMAC that matched other cards' information. I finally stopped trying to validate my method with other access cards and just sent it using the key as is, which finally worked!
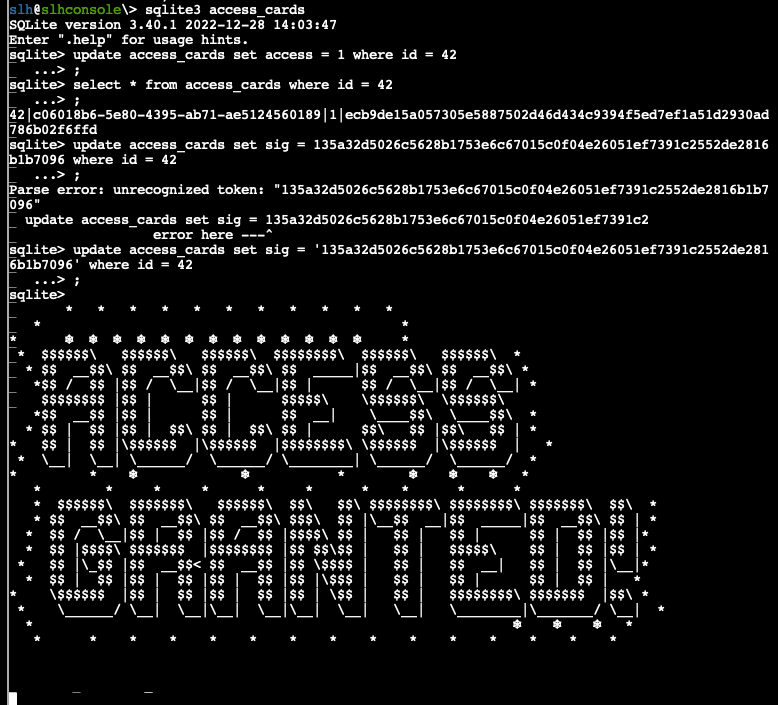
To be continued in Act 2!