SANS SEC660 - Advanced Penetration Testing, Exploit Writing, and Ethical Hacking

UPDATE: I took my exam and PASSED! I felt that the actual exam was a bit harder than the practice tests but I also get my best score out of the three. The material covered in class is great but you really have to have read the text in the books to get everything that is going to show up on the test.
I was again lucky enough to have the opportunity to attend a SANS course, this time the course was SEC 660: Advanced Penetration Testing, Exploit Writing, and Ethical Hacking. This is the follow on course to the intro-level penetration testing course (SEC 560).
Unlike with my decision to take SEC642 last time, I did not struggle at all with which course to take this time. Given that I had taken the OSCP already, I felt very comfortable with the described level of the material that would be covered in SEC660.
This class was absolutely the correct decision, but I have to admit that without the knowledge I had gained from the OSCP about basic exploit writing, I think that SEC660 would have been a bit too far over my head. This class is definitely not a direct follow-on from SEC560 (I have not taken it but spoke to a co-worker who took it at the same time). I think if a student went directly from one class to the other without intervening education, SEC660 would be extremely difficult.
SEC660 covers (as topics that stood out to me) execution of man-in-the-middle attacks (instead of just talking about them), advanced packet manipulation, fuzzing (first time ever really doing this), Linux exploitation, and Windows exploitation. All topics were covered at a very in-depth level (there was no scratching the surface here). Additionally, this class had a TON of labs, especially with the bootcamp style add-on content at the end of each day.
The labs were critical to understanding the material and I very much enjoyed that all the labs could be completed on modern Operating Systems (I was using Windows 10 for most of the Windows work).
The Linux and Windows exploitation blocks were definitely the most difficult. We went into a lot more detail than the OSCP and obviously had the added benefit of having an instructor there to bounce questions off of. That being said, we covered a TON of material about structures in memory, where different structures are loaded, the names of all sorts of memory constructs, and then never really "used" those things. I assume this was all about getting exposure to these things as a step towards further understanding while the labs really just focused on the 'basic' situations.
CTF
The class CTF was a lot of fun. Our team (ROPtimus Prime) led the class until about the last 20-30 minutes when another team pulled ahead. The CTF was very competitive and I was really surprised when I was able to write a ret2libc style exploit in about 15-20 minutes. The frustrating part was realizing after we did the walkthrough that we definitely over-thought almost every challenge.
NetWars
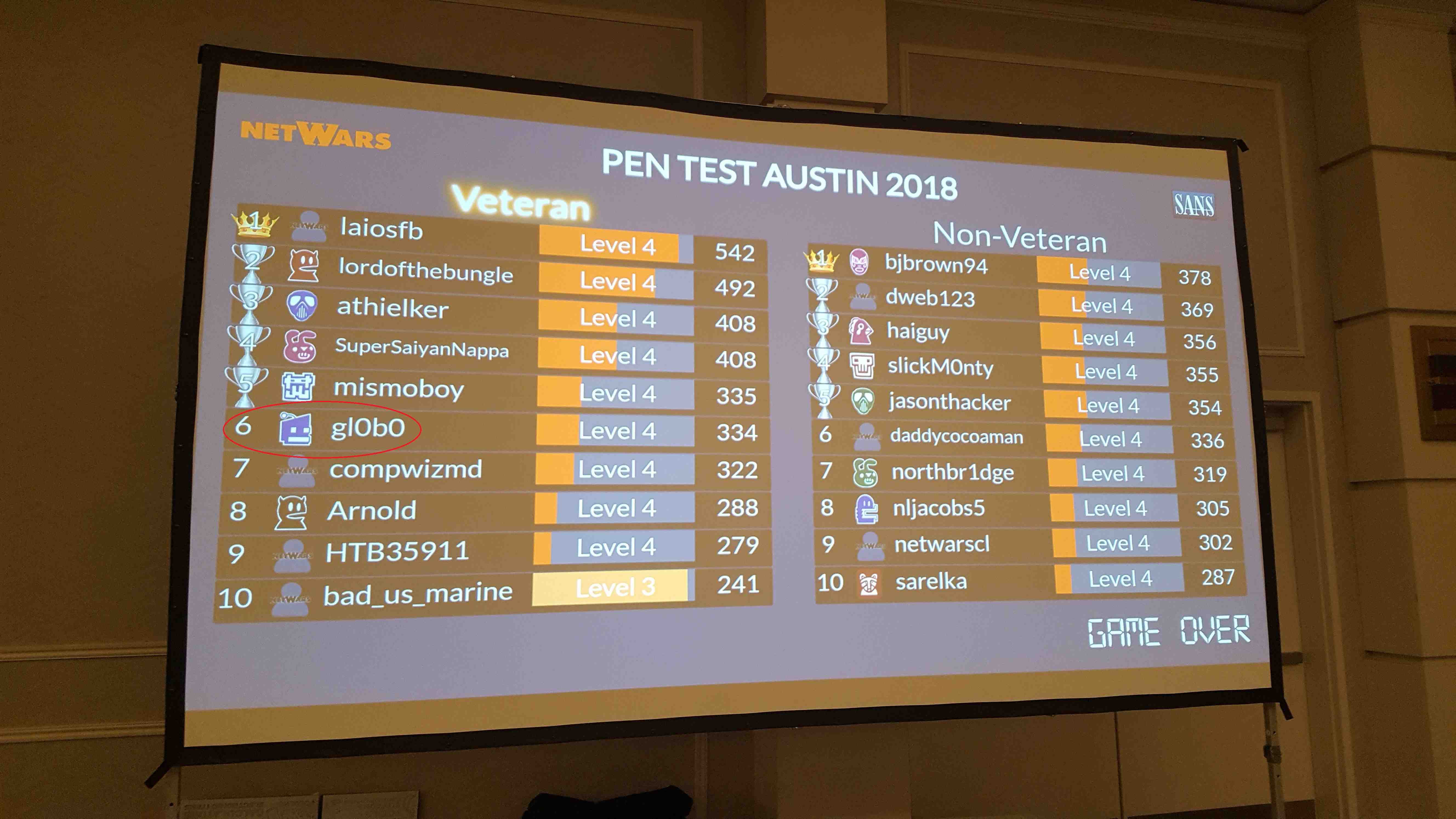
Once again, SANS hosted NetWars, though this time the event was also Coin-a-Palooza where participants have the opportunity to earn coins for classes they have taken in the past. Normally the only way to get a coin is to take a class and ALSO win the class CTF.
This was the same NetWars I had done previously so I was lumped into the 'Veteran' category. After 3 nights of tournament I ended up in 6th place with 334 points (WAY better than my previous 242 and took home 4 new SANS coins. 1 more point and I would have been in 5th place and eligible for the national tournament. Another co-worker also ended up on the leaderboard in the non-veteran category.
Unfortunately I had not saved my answers from the last time I played so spent a lot of time re-working a lot of the challenged and missed out on a 20 point question I had solved last time. I did get into the web application section this time which was a lot of fun too.
NetWars is an amazing event and the SANS crew did another great job of putting the event on (thanks for the free beer).
Bottom Line
This class is not for the faint of heart and goes really in depth on each of the topics we covered. I have seen this advice elsewhere and I would have to say I agree: A good course flow would be SEC560 > PWK/OSCP > SEC660 ...
Thanks to Tim and the SANS team for the great even and top notch education.
I will update this post once I take the exam.
